It's almost inevitable that security vulnerabilities will be discovered in a web application's components during its lifecycle. Such vulnerabilities can exist in custom code that was developed in-house, or in third-party components such as open source packages.
In the case of a vulnerability in custom code, the patching process will have to include development, testing and deployment teams, which can take hours, days or even weeks. When it comes to vulnerabilities in third-party components, however, the process is even more complicated since the teams have to wait for a third-party vendor to issue the fix. Only once the fix is available will they be able to begin testing it in their environment and deploying it to production.
“Virtual patching” enhances patch management, reducing risk in this window of time before an official software patch is available. As part of the latest release to the Prisma Cloud Web Application and API Security (WAAS) module, we have introduced several key capabilities related to virtual patching which customers can harness to continuously maintain good application security posture. These capabilities include:
- Custom WAAS rules management
- Ongoing protection updates delivered by Prisma Cloud Labs
- Customer-defined WAAS rules
What is Virtual Patching?
Virtual patching is the process of creating one or more detection rules that prevent malicious exploitation attempts against a vulnerability before an official patch is available. Prisma Cloud can deploy these virtual patching rules within minutes after a vulnerability is discovered, and users can keep them in place until the official patch is applied.
Virtual Patching with Prisma Cloud
When critical vulnerabilities for relevant application technologies are publicly reported, the Prisma Cloud Labs team may release updated WAAS rules and automatically push them to all customers, who would then be able to choose whether to apply them.
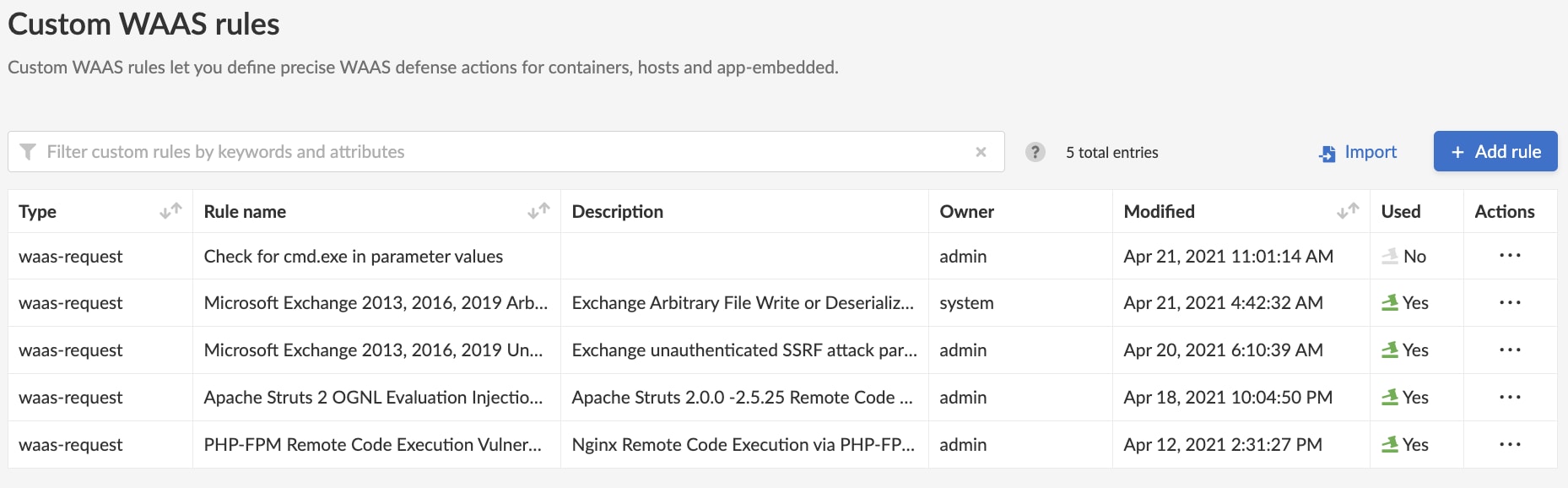
But because each application is unique, customers may want to create their own rules to meet the specific requirements of their own application. In such cases, new custom rules are easily created through the editor in the Defend > Custom Configurations screen.
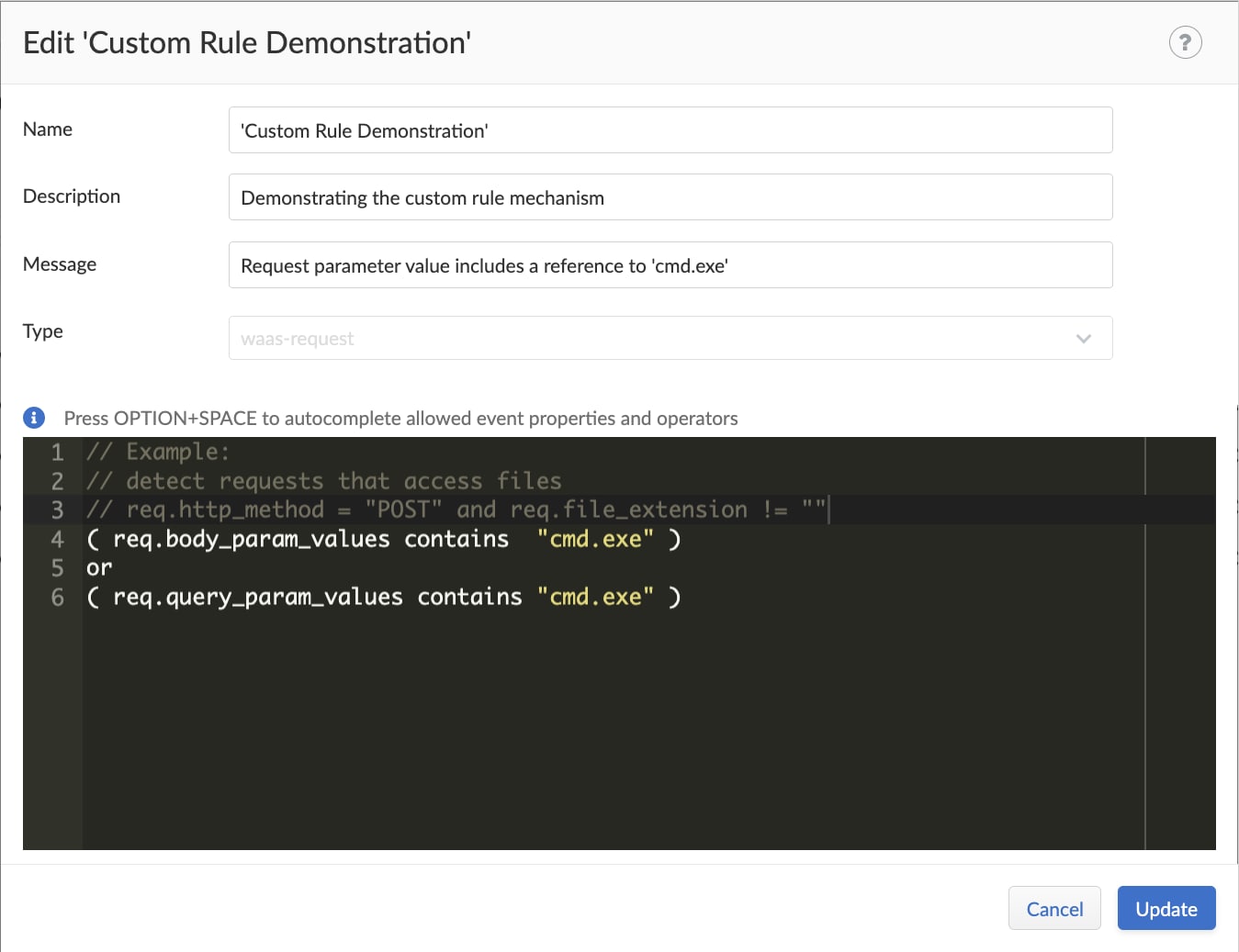
For simplicity and ease of use, the custom rules editor includes an auto-complete feature for code, in addition to syntax highlighting.
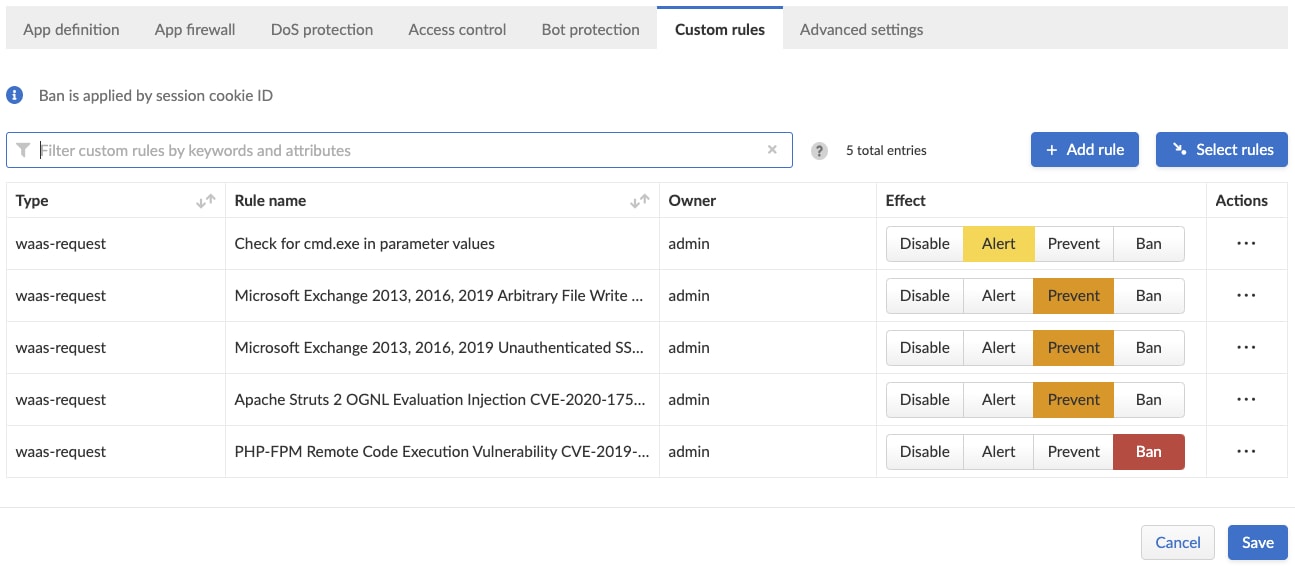
Once a rule exists in the central repository, it can be applied to different WAAS configurations with specific “effects” for each one. For example, a single rule could be set to “alert” on one Kubernetes cluster and “prevent” on a different cluster, as shown in the image below.
Summary
With this new virtual patching capability customers can rely on up-to-date virtual patches published by Palo Alto Networks, while still being able to create custom rules to match their specific needs.
Our continued investment to enhance our WAAS capabilities makes Prisma Cloud the best unified platform for securing cloud native applications, whether they run on hosts, containers or serverless architectures. To learn more about the WAAS module, download our whitepaper Raising the Bar on Web Application and API Security.