Maintaining the integrity of critical systems is paramount for security managers, including the IT infrastructure and sensitive business data, like financial records or intellectual property. Unauthorized or accidental changes to operating systems and application files, or any other critical information, can signal a breach, or worse, open the door for malicious actors to compromise your environment. That's where file integrity monitoring (FIM) comes in.
Achieving Security and Compliance with FIM
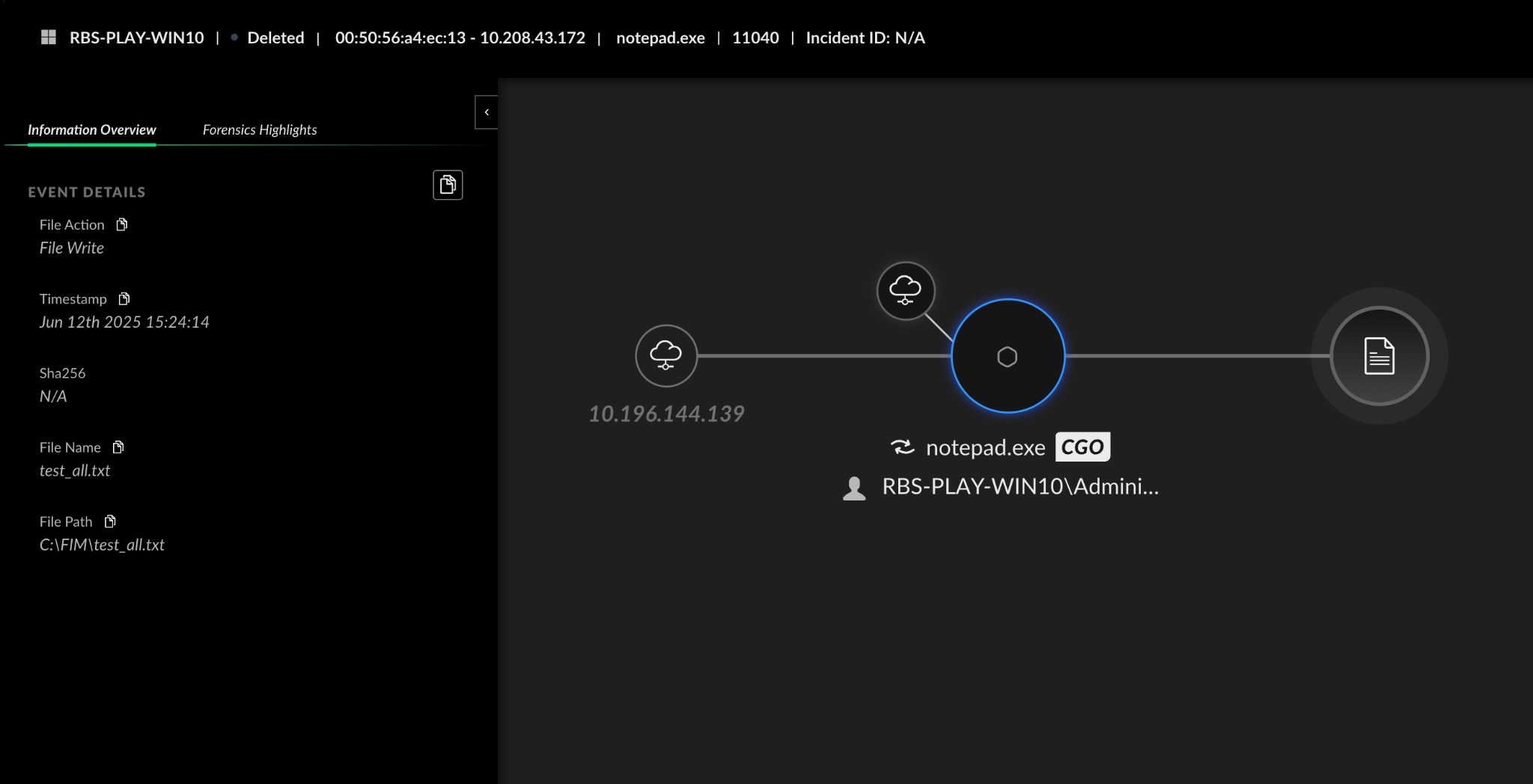
FIM continuously monitors file events in the operating system for unauthorized alterations, whether to content, attributes, or even deletion, and sends real-time alerts when an event occurs.
But FIM isn't just about security; it's a critical component for compliance. Regulatory frameworks like PCI DSS (Requirement 11.5), SOX (Section 404), NERC CIP, FISMA, and HIPAA all mandate FIM to ensure the security and trustworthiness of systems. Beyond compliance, FIM is invaluable for robust change management, helping you monitor for unauthorized alterations, identify attempts to hide evidence of changes, and maintain a clear audit trail.
Why an Integrated FIM Matters
FIM within Cortex offers immediate value for our customers. You'll experience simplified administration and a unified security view, all from a single platform and agent. This means no more deploying and managing separate FIM solutions with their own platforms, agents, and event forwarding methods. Instead, our FIM integrates seamlessly with your existing Cortex deployment, reducing agent sprawl and providing a holistic view of your security posture.
By combining FIM with Cortex's rich endpoint and workload data, you gain full visibility into file changes and their broader security implications. Even if you're new to FIM or looking to replace an existing solution, implementation is straightforward – no extra installations required, just policy configuration.

Key Capabilities
Primarily designed for servers and containerized environments, FIM ensures the integrity of your critical data and applications. Here's what makes it stand out:
- Enhanced Security & Compliance: FIM strengthens your security posture and helps meet compliance by monitoring sensitive files. It replaces the need for additional FIM tools, streamlining your security stack.
- Real-Time Monitoring: Unlike agentless solutions that offer only point-in-time snapshots, Cortex continuously tracks and alerts on every single change to a file in real-time.
- Rich, Actionable Data: FIM events are enriched with detailed XDR data, creating a complete causality chain for investigations. Quickly monitor daily activity via table search or conduct in-depth analysis using XQL.
- Flexible Policy Management: Configure FIM with user-defined policies, rules, and rule groups. Out-of-the-box rules are available for easy setup. For containers, specify image names for precise control. Rules are organized hierarchically for simplicity and flexibility.
- Comprehensive OS Support: FIM supports Windows and Linux, including Kubernetes containerized environments.
- Detailed Event Tracking: Monitor file and folder activity including creation, deletion, content, attribute, and permission changes using pre-built or custom rules. This data seamlessly integrates with XDR data for enhanced insights and behavioral indicators of compromise (BIOC) support.
- Unified Investigation Experience: Gain a complete investigation experience by understanding FIM events through a unified view with a full causality chain.
- Optimized Performance: While FIM can impact agent resources, we've implemented safeguards to prevent event overflow and ensure efficient monitoring.
Elevate Your Security Posture with FIM
File integrity monitoring is no longer a siloed solution or just another data feed; it's a fundamental requirement for a strong runtime security and regulatory compliance. With FIM as part of the Cortex platform, you gain an integrated and easy-to-manage solution that helps you detect unauthorized changes, maintain compliance, and strengthen your overall cyber defenses.
The FIM module is now generally available out of the box for all Cortex Cloud runtime customers. This will also be made available later as an add-on module to Cortex XDR and Cortex XSIAM. Please visit the Cortex webpage to learn more.