For the modern enterprise, the browser is no longer just an application but the new operating system of work. With 85% of modern business activity happening within the browser, it is where your data lives, where your employees collaborate and where your revenue is generated.
However, this shift has introduced a challenging new reality for security teams. While the browser has become the primary workspace, it remains a massive blind spot for traditional security operations center (SOC) teams. In fact, for eXtended Detection and Response (XDR) and network monitoring, the browser is effectively a “black box,” viewed as nothing more than a process that obscures the dynamic world inside.
Browser Intelligence Deficit Creates Security Gaps
While organizations have invested in XDR to secure the operating system (OS) and network tools for traffic insights, these solutions typically treat the browser as a single, opaque process. This fragmented view leaves SOC teams blind to high-fidelity in-browser data. As a result, critical actions such as handling sensitive data, downloading rogue extensions, or falling for phishing attacks go undetected. These behaviors, including copying and pasting or taking screenshots of sensitive information, remain entirely invisible to security teams.
The stakes are incredibly high: 95% of organizations have experienced an attack originating in the browser. Without "opening the box," SOCs are missing the primary attack vector in their XDR and network analysis strategy.
Unlock Full Threat Intelligence with Prisma Browser
When threat teams lack visibility into browser data, they cannot identify the root cause of an attack. Forced to operate blindly, SOCs often rely on aggressive "nuclear options" like total endpoint isolation to ensure safety. While this stops the threat, it also halts operations, unnecessarily disrupting business for issues that could have been easily managed.
With Prisma Browser™, there is a substantial opportunity to improve SOC security and operations. Prisma Browser delivers enterprise-grade security against phishing, data leakage and AI-generated attacks in the browser without disrupting the user’s workflow or performance. By delivering the context that was once a blind spot, Prisma Browser provides a comprehensive view of every event, allowing your team to use high-fidelity telemetry, root cause analysis (RCA) and enforce granular control.
Correlate the Unseen with High-Fidelity Telemetry
Instead of generic network traffic, opening the black box reveals EDR-level events within the browser to feed the XDR engine, including impactful extension actions, clipboard access, mouse and keyboard events, and cookie access. SOCs can now detect complex threats such as paste jacking (copying code from a browser and pasting it into a terminal), sending private/sensitive data, taking over accounts, and sensitive data exfiltration.
Dismiss False Positives with Root Cause Analysis (RCA)
With visual evidence, you can see the full causal chain across the XDR landscape, enabling faster remediation from the user clicking a link to the exploit executing in memory. For example, a large upload alert can be immediately dismissed if the SOC can see the upload destination is a sanctioned site and the data is benign, rather than blocking a user unnecessarily.
Remediate Surgically and Enforce Granular Control
With deep browser visibility, response can be granular and automated to block a specific malicious extension or access to a sensitive site, block the upload/download of specific content, or isolate the browser instance without locking the user out of their entire machine. Block access to sensitive sites or isolate the browser instance itself, without touching the underlying OS.
Which Browser Would You Choose?
Let’s look at two scenarios where data exfiltration happens via a rogue extension with and without Prisma Browser.
Data Exfiltration via a Rogue Extension Without Prisma Browser
An executive’s browser starts uploading data to an unsanctioned server. The SOC sees a massive upload from the browser process. Lacking context, the SOC assumes a total endpoint compromise.
- Action: The laptop is isolated. The executive is locked out during a critical negotiation.
- Result: The threat is contained, but business continuity is shattered.
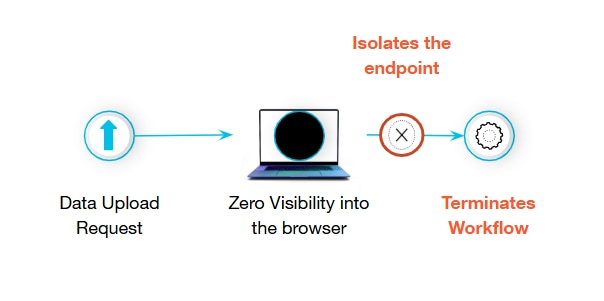
Figure 1: Zero visibility into what’s happening in the browser.
Data Exfiltration via a Rogue Extension with Prisma Browser
What could the organization have done better? By integrating Prisma Browser with their SOC, the "black box" is opened. The SOC gets rich insights into all activity that took place in the browser. They trace the root cause: it wasn't the user or the OS. It was a specific browser extension that caused data exfiltration.
- New Action: The SOC uses precise response capabilities. They surgically block the ability to upload data to unsanctioned destinations until further notice.
- New Result: The executive continues working without interruption. The threat is neutralized instantly.
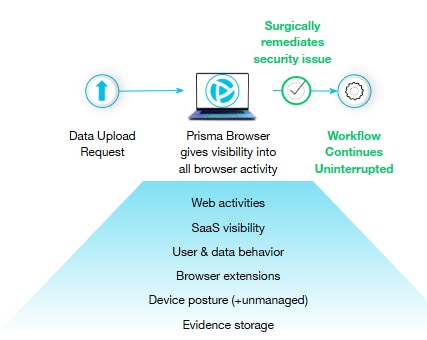
Figure 2: SOCs get rich browser insights to surgically remediate the security issue.
Empower Your SOC with Better Detection Without Disrupting Work
For too long, SOC teams have been forced to compromise on visibility, relying on isolated network and endpoint events to piece together a fragmented picture. This blind spot has forced threat intelligence teams to disrupt the very operations they aim to protect, using aggressive isolation tactics to manage risks they couldn't fully see. However, by connecting XDR and network insights with deep browser events, organizations can finally uncover the full attack path.
With Prisma Browser, you are doing more than just closing a security gap; you are opening a path to business continuity. By shedding light on the "black box," you can finally empower your SOC to stop the attacker without stopping the business.
Don't let your primary workspace remain your biggest blind spot. Schedule a demo today to see how the SOC team can leverage Prisma Browser to be their biggest vantage point.