Boyne Resorts had a legacy SIEM that overloaded its security team with false positives while making it difficult and expensive to integrate data sources. Needing to gain visibility across its distributed environment and achieve best-in-class threat intelligence, the company implemented Palo Alto Networks Cortex XSIAM and Unit 42 Managed Detection and Response (MDR).

Founded in 1947, Boyne Resorts is a collection of mountain and lakeside resorts, golf resorts, ski areas, and attractions across the United States and Canada. The company is headquartered in Michigan, where it first began, and now owns and operates 14 properties that span from British Columbia to Maine. With a team of over 11,000 employees and a track record of growth and innovation, the company requires a comprehensive approach to cybersecurity.
An underachieving SIEM puts a thriving company at risk
Boyne’s security operations team works in a central location and is responsible for maintaining visibility into potential threats and exposures across the company’s distributed networks and device fleet.
The team was grappling with a legacy security information and event management (SIEM) system that presented challenges on multiple fronts. Although it was only ingesting a small amount of data, the SIEM produced a high false positive rate and few quality insights. In addition, the cost of adding more data sources was prohibitive.
As Mike Dembek, network architect for Boyne, explains: “Log collection was a huge weak point for us. Our SIEM was expensive and it was difficult to integrate sources.” He adds, “We were hunting down alerts that weren’t accurate. It was a hodgepodge of stuff that wasn’t correlated together.”
A third party managed the SIEM, yet even with this additional support, alert volume was immense. While Boyne needed relevant insights gathered across more data points, Dembek knew that simply adding more sources to the SIEM would result in a higher price tag and even more noise.
Strengthening security across thousands of company devices and reams of valuable data required more than its SIEM could provide—so Boyne made the transition to Palo Alto Networks Cortex XSIAM. The company also partnered with Palo Alto Networks Unit 42® for ongoing MDR services and a Unit 42 Retainer.
The team sees potential for total SOC transformation
Boyne’s small, dedicated security team aimed to replace its legacy SOC with one that delivered the quality and rigor the business demands. The team wasn’t willing to settle for small improvements. Best-in-class was the goal.
To accomplish that, the team needed solutions that would:
- Ingest significantly more data sources—without an exorbitant price tag
- Provide minimal false positives to reduce alert fatigue and wasted time
- Deliver more value, insights, and intelligence across the board
- Effectively control risk and improve Boyne’s security posture
- Offer 24/7 coverage to extend the company’s in-house team
Ultimately, the team wanted to expand visibility and deepen its analytics capabilities without the need to add more headcount. Tall order? Definitely. Doable? With Cortex XSIAM and Unit 42 MDR, absolutely.
"With XSIAM, we have more visibility and faster investigations. Seamless data onboarding and automation setup are gamechangers.”"
Mike Dembek, Network Architect, Boyne Resorts
Moving from frustration to clarity and peace of mind
When Boyne adopted Cortex XSIAM, it got robust SIEM functionality—and a whole lot more. Cortex XSIAM delivers multiple capabilities in one platform, including SIEM; endpoint detection and response (EDR); network detection and response (NDR); identity threat detection and response (ITDR); security orchestration, automation, and response (SOAR); and more.
 While the security team was hesitant to add data sources to the prior SIEM due to the high cost and engineering difficulty involved, Cortex XSIAM enabled Boyne to add multiple new sources and increase the amount of data ingested by a factor of 70.
While the security team was hesitant to add data sources to the prior SIEM due to the high cost and engineering difficulty involved, Cortex XSIAM enabled Boyne to add multiple new sources and increase the amount of data ingested by a factor of 70.
Native parsing enabled by Cortex XSIAM makes data onboarding easier. Boyne is now able to capture data across devices, clouds, identities, web apps, system configurations, and more—all in one centralized platform.
Less noise makes way for more insight
On top of greater visibility, the number of false positives plunged. Cortex XSIAM has a correlation engine that consolidates multiple alerts into a single incident, reducing duplicates and rework. Incidents requiring investigation fell from 80–100 to 35 per day, due to reductions in both the false positive rate and the number of duplicate incidents identified.
Boyne also gained new levels of control and customization. “Our prior SIEM didn’t have any alert tuning or custom alert capabilities,” recalls Kenny Hicks, lead security engineer. “The out-of-the-box correlation alerts are a big advantage with XSIAM. We can also create our own custom alerts if needed.”
With Cortex XSIAM, the team saw improvements in multiple areas:
- Data ingestion grew from 5 GB per day in the prior SIEM to 350 GB per day in Cortex XSIAM, providing greater visibility and protection.
- Data sources rose from 1 to 21, providing the ability to correlate events across various data sources.
- 65% reduction in open incidents from 80–100 to 35 per day, due to reductions in false positive rates and duplicate incidents.
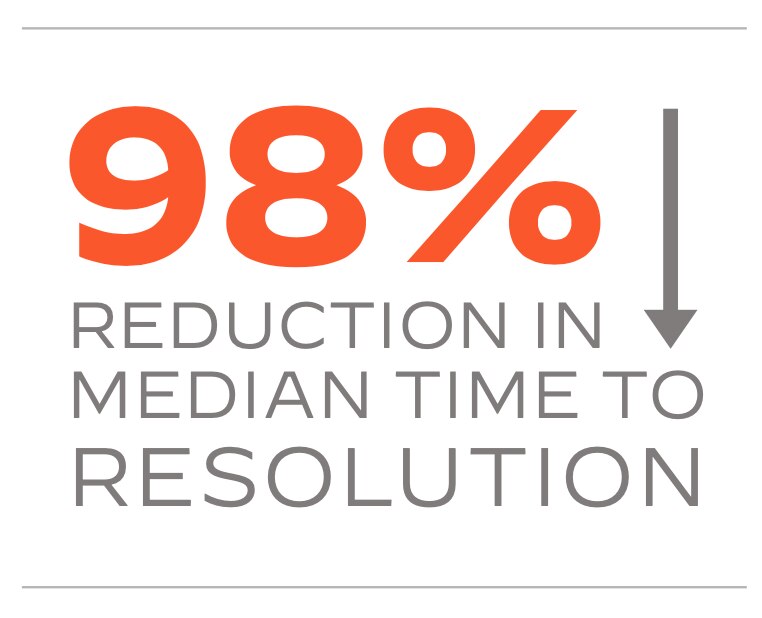
- 98% reduction in median time to resolution from 2–3 days to 1.7 hours.
- 95% reduction in vendors and tools from 20+ tools and dashboards needed for investigations to 1.
- SIEM comanagement was no longer needed, as the company was able to take management in-house.
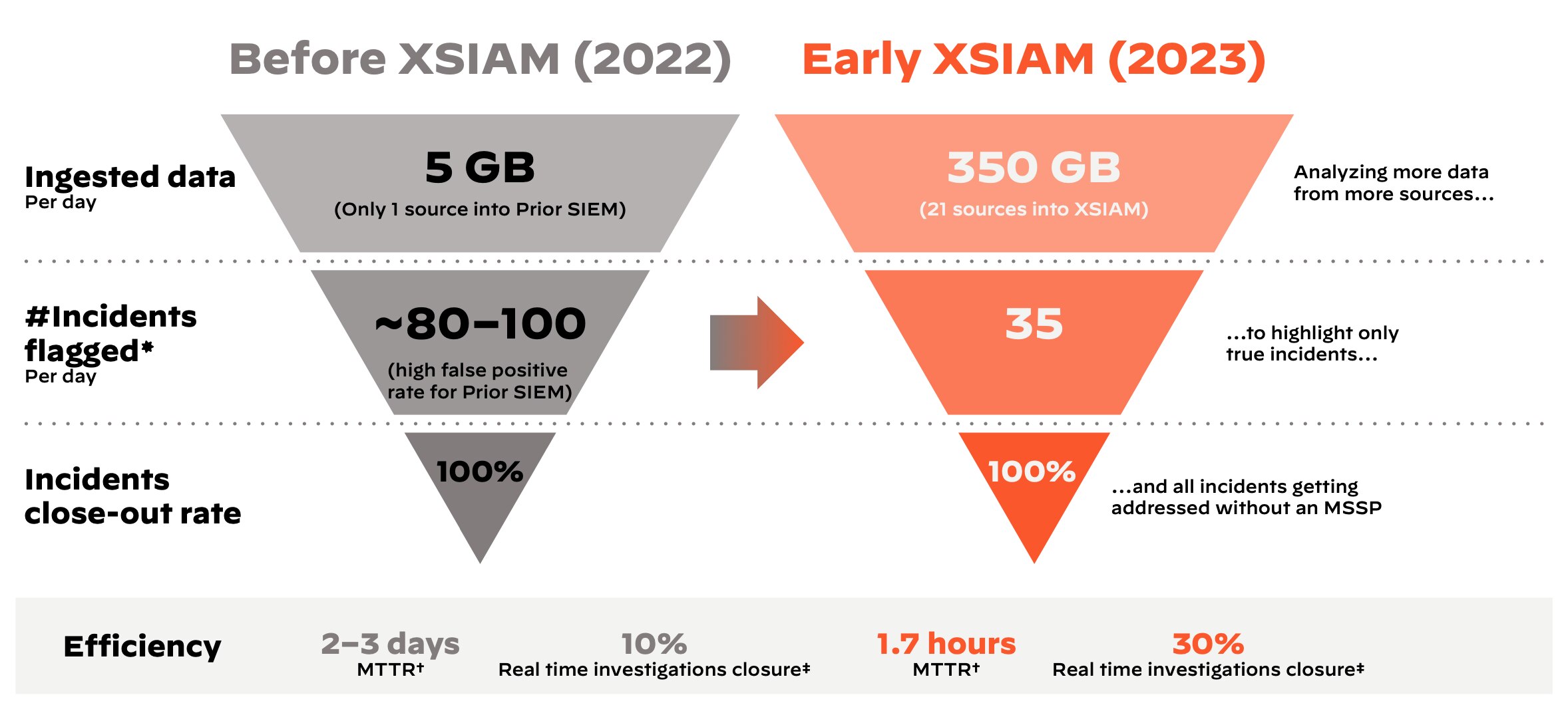
†MTTR = Median time to resolution (time from alert to case resolution)
‡Real-time investigations closure = Incidents remediated in less than 60 minutes after detection
Making sure security never stops
Boyne security leaders didn’t only want to strengthen the company’s security posture. They also wanted to have a 24/7 SOC—without expanding their team.
After implementing Cortex XSIAM, they engaged Palo Alto Networks Unit 42 to provide MDR services to augment the team’s efforts and provide coverage, 24/7, year-round. Working with Unit 42 MDR allows the company to leverage Unit 42’s world-class threat intelligence and extensive expertise in both security and Cortex products. Ultimately, this provides complete visibility and faster response across distributed networks and systems.
“We’ve been impressed by the MDR team’s willingness to help,” says Hicks. “Working with them has been very successful, giving us early access to new XSIAM feature sets and making us more efficient.”
The Unit 42 MDR service is integrated with Cortex XSIAM, giving Boyne a single user interface to review investigations and determine next steps, saving the small team time it used to spend juggling disconnected systems and allowing it to focus on more strategic priorities.
“The MDR team handles our investigations, forwarding any alerts, and shares a detailed report that helps us make quicker, more accurate decisions on those incidents,” explains Hicks. “This saves our team a huge amount of time.”
With continuous monitoring, proactive threat hunting, and other components of the MDR service, Boyne security analysts can be confident that even when they don’t have eyes on their environment, a trusted partner does.
A proactive stance positions the company for the future
The new approach delivers far more functionality and reduces the workload on Boyne’s security team. Cortex XSIAM was built to enable advanced automation, allowing the team to accomplish far more with less.
“With XSIAM,” Dembek reports, “we are stitching network and endpoint protection together, seeing the entire causality chain.”Hicks adds, “XSIAM makes automation easy. The ability to easily ingest data and create playbooks with minimal coding drastically reduces the effort required to set up automation.”
Between transforming its SOC with Cortex XSIAM and retaining Unit 42 MDR services, Boyne now has:
- Greater visibility into potential threats and issues. By increasing the number of data sources and total data ingested with Cortex XSIAM, and with proactive threat hunting from Unit 42 MDR, Boyne can see far more than it could before.
- High-quality alerts and improved detection. With custom alerts and alert tuning enabled by Cortex XSIAM, the team is receiving better-quality information.
- Materially better AI and analytics capabilities. Thanks to custom out-of-the-box analytics that come with Cortex XSIAM, the company is are able to do a great deal more with network and endpoint data.
- Better productivity and efficiency across the security team. With high-maturity automation, multiple playbooks, plus investigation insights, expertise, and 24/7 continuous monitoring from Unit 42 MDR, the team can get more done in less time.
- A best-in-class level of threat intelligence. With several feeds coming into Cortex XSIAM that enrich alerts and analytics, Boyne has extensive insight into potential threat actors and risks.
World-class incident response on speed dial
The company is also now better prepared for the future. With its Unit 42 Retainer, Boyne will continue to take a proactive stance to its protection, while experts well-versed in its environment are on speed dial to respond quickly to a major incident—should one occur. Next, the Boyne team plans on using its retainer credits toward a Unit 42 Tabletop Exercise to improve its incident response processes and grow its effectiveness around real-world security scenarios and the latest threats.
The security team is very happy with how well all of its Palo Alto Networks products and services work together to improve the company’s security posture.
By partnering with Palo Alto Networks, Boyne is now better equipped to meet whatever challenges the future holds and keep the company secure as it continues to innovate and grow.
"The Unit 42 Retainer played perfectly with our MDR and SIEM services. The MDR team’s ability to transition directly to the Unit 42 team during an incident response scenario is exactly what we wanted.”"
Kenny Hicks, Lead Security Engineer, Boyne Resorts
Learn more about Cortex XSIAM, Unit 42 MDR, and the Unit 42 Retainer on our website.