This post is also available in: 日本語 (Japanese)
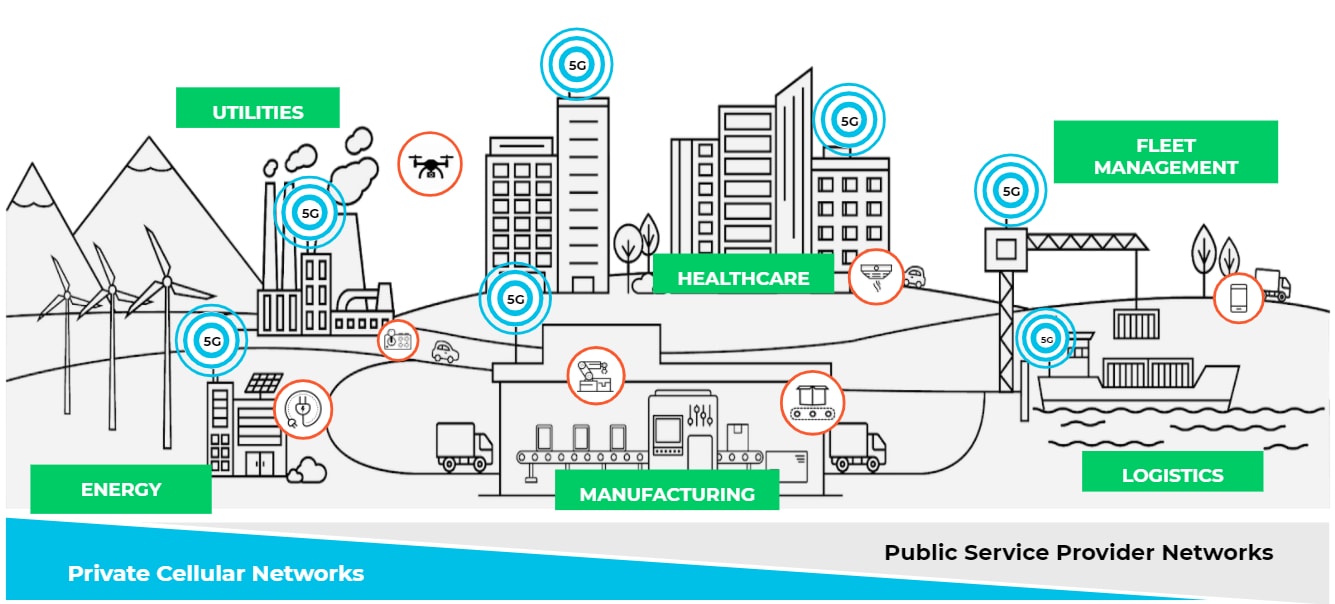
5G promises transformative mobility through enhanced mobile broadband experiences and industrial digitization. To safeguard these advances, we are announcing the industry’s first 5G-native security. We’re bringing our expertise in securing networks, clouds and devices to the 5G world, enabling service providers and enterprises to turn 5G networks into highly secure networks. In the process, we’re offering multiple industry firsts:
- Containerized 5G-native security. Much of the 5G infrastructure is being built with cloud-native architectures. Palo Alto Networks Containerized 5G security is designed to secure the highly distributed 5G networks, including edge clouds and across multi-vendor and multi-cloud environments.
- Realtime correlation of threats to 5G subscriber, 5G equipment. Realtime correlation of threats can help identify which subscriber, device or machine might be the target of an attack or where the root cause of threats might be. This can help in forensics and accelerated security event investigation.
- 5G network slice security. 5G networks allow service providers to offer a dedicated end-to-end piece of the network that gives enterprises the reliability and confidence to use 5G for their core business activities. Palo Alto Networks 5G-native security lets service providers offer secure versions of these slices to their customers as a new product.
With this release, we are helping service providers and enterprises protect their end-to-end 5G infrastructure across all layers and all key locations of the distributed, cloud native, multi-cloud 5G architectures.
This single platform for 5G security will help our customers:
- Gain context-driven security at scale to provide the most granular security for 5G infrastructure.
- Leverage industry-leading Palo Alto Networks security in enterprise 5G deployments.
- Enable service providers to upsell security offerings on top of connectivity to customers, to provide secure “as-a-service” offerings for 5G slice, enterprise 5G networks, and multi-access edge computing (MEC).
The Move From 4G to 5G Requires a New Approach to Security
5G networks enable new enterprise use cases, such as smart manufacturing, smart cities, remote medical access, self-driving cars and industrial-scale IoT networks with ultra-low latency, mission-critical reliability, and a higher degree of mobility. Service providers and enterprises need new solutions to protect their investments in this groundbreaking technology.
The traditional approach to security in 4G networks focused on securing perimeters. 5G networks will be built upon distributed clouds, and they will come with software-defined perimeters with multiple exposed interfaces. 5G network functions are containerized and will run on multiple cloud stacks. This makes the old perimeter protection model insufficient in light of massive growth in industry and internet of things (IoT) connectivity, as well as cloud services and edge computing. ML-powered NGFWs for 5G address these new 5G networking security challenges.
In 4G networks, the device-level attack surface was focused predominantly on a few device types, such as smartphones and LTE routers. With 5G, however, billions of IoT devices loom large on the threat horizon. IoT is the low-hanging fruit for attackers who are likely to leverage 5G speeds. Unit 42 – the threat research arm of Palo Alto Networks – has reported that 98% of all IoT traffic is unencrypted, exposing personal and confidential data on the network.
Network slicing in 5G paves the way for new business services that can realize the true potential of 5G capabilities. Network slicing allows dedicating a set of network resources to an enterprise. But this means 5G network slices will require custom security posture and dynamic security.
The Palo Alto Networks Comprehensive Approach
Any 5G security platform must now encompass all traffic (data, control and signaling planes), protect networks and provide a safe environment for enterprise users and service provider customers. That’s why our approach to 5G security is based on:
- Context-driven security at scale for granular visibility and control across all layers (signaling, data, control and application layer), and at all key locations of a 5G network for comprehensive protection.
- Security automation leverages Kubernetes-native orchestration and integration with open APIs for operational simplicity. Powered by machine learning (ML), automated cloud-delivered threat intelligence enables teams to defend against adversaries operating at 5G speeds – as well as prevent known and unknown threats in realtime across 5G networks on a global scale.
- 5G service innovation by providing security capabilities and tools to enable “as-a-service” offerings for 5G slice security, Enterprise 5G security and MEC security.
This approach is designed to provide enterprises and service providers with:
- Reduced risk by incorporating a Zero Trust approach – Protect end-to-end 5G infrastructure across all layers and all key locations of the distributed, cloud native, multi-cloud 5G architecture.
- A high degree of automation – Service providers can manage security with less effort due to automated, context-driven security at scale, offering the most granular 5G security and leveraging unique identifiers of 5G subscribers, 5G equipment and 5G slices.
- Accelerated adoption of transformative 5G use cases with lower total cost of ownership (TCO) – Enterprises can now extend the industry-leading Palo Alto Networks 5G security solution into their mobile networks.
- A path to new revenue streams – Capitalize on the 5G opportunity by providing a path to new revenue streams based on secure connectivity.
Comprehensive 5G Security Is Now Available
Service providers can gain full visibility and security control across all layers and all key locations of their 5G networks with Palo Alto Networks Next-Generation Firewalls.
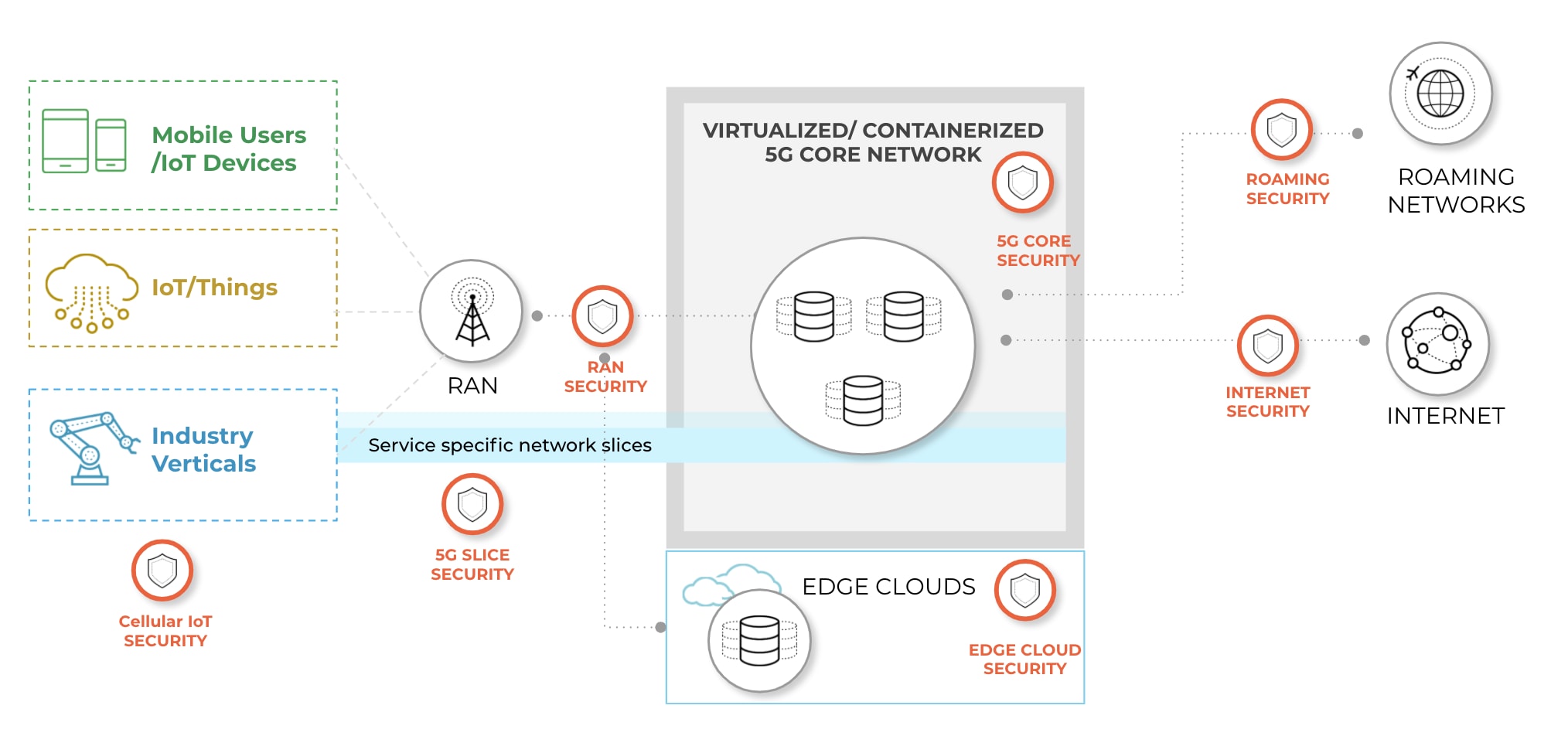
Enterprises can deploy Palo Alto Networks Next-Generation Firewalls directly inside their mobile networks for full visibility and control on the 5G service layer and user data traffic.
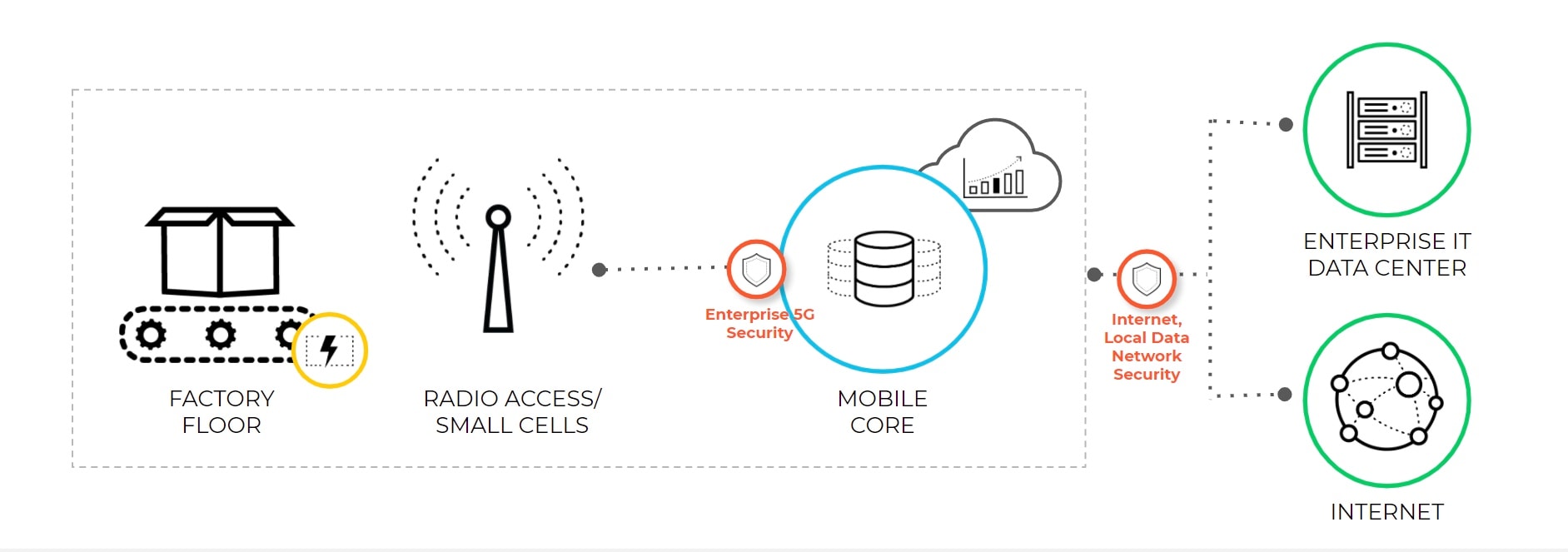
5G security capabilities are available on the following Palo Alto Networks next-generation firewalls: PA-5200 Series and PA-7000 Series hardware models as well as all VM-Series software models running PAN-OS 10.0+. Security Services can be added based on use case requirements. 5G security capabilities will be available on CN-Series containerized firewalls soon. This means that if you already use our Palo Alto Networks next-generation firewalls, you can continue to use the same platform inside your public 5G or private 5G network.
Learn how to get started securing your 5G investments with the new Palo Alto Networks comprehensive 5G security solution.