-
- Cybersecurity Automation Explained
- Cybersecurity Automation Use Cases: Four Key Areas
- How Cybersecurity Automation Works
- Benefits of Automating Your Security Operations
- The Critical Role of Human Oversight
- Challenges and Best Practices for Implementation
- How Automation Stops the Attack Lifecycle
- Cybersecurity Automation FAQs
Table of contents
-
What Is Cybersecurity? Why It Matters & Core Concepts
- Why Cybersecurity Matters: An Enterprise Risk
- Key Principles of a Layered Defense
- Core Domains of Cybersecurity (Types of Security)
- Understanding the Threat Landscape
- Industry-Specific Cybersecurity Challenges
- The Dual Role of AI
- The Acceleration of AI-Driven Threats
- Cybersecurity Best Practices
- Cybersecurity Frameworks and Standards
- The Cybersecurity Workforce
- Cybersecurity FAQs
- What Is Cybersecurity for Small Businesses?
-
What Is Cybersecurity Platformization?
- Cybersecurity Platform Consolidation: An Overview
- Benefits of Security Tool Consolidation
- How AI Enhances Cybersecurity Consolidation
- Selecting the Right Consolidation Strategy
- Aligning Investments with Business Goals
- Challenges in Platformization
- Future Trends in Cybersecurity Platform Consolidation
- Cybersecurity Platformization FAQs
-
What Is a Cybersecurity Risk Assessment?
- Cybersecurity Risk Assessment Explained
- Why Is Cyber Risk Assessment Important?
- Common Cybersecurity Risks and Threats
- Different Approaches to Cyber Risk
- How to Perform a Cybersecurity Risk Assessment
- Determine the Scope of the Assessment
- Cybersecurity Risk Assessment Benefits
- Cyber Risk Assessment FAQs
4 Ways Cybersecurity Automation Should Be Used
4 min. read
Table of contents
Implementing cybersecurity automation provides immediate benefits across key security functions. The most impactful use cases involve leveraging automation to improve the efficiency and effectiveness of:
- Threat detection and incident response
- Vulnerability management
- Compliance and governance
- Threat intelligence
These use cases help security teams operate at machine speed to counter modern, automated attacks. Automation handles high-volume, repetitive tasks, freeing up human analysts to focus on more complex, strategic challenges that require expert judgment.
Key Points
-
Faster Response: Automation enables organizations to detect and respond to threats in real time, reducing the time attackers have to cause damage. -
Increased Efficiency: By automating repetitive, mundane tasks, security teams are freed up to focus on more strategic and complex challenges. -
Reduced Human Error: Automated systems perform tasks consistently and continuously, eliminating the risk of human error in critical security operations. -
Proactive Defense: Automation helps organizations move from a reactive security stance to a proactive one, identifying and mitigating vulnerabilities before they can be exploited. -
Enhanced Compliance: Automated tools streamline compliance management by continuously monitoring systems and generating reports that demonstrate adherence to regulations.
Cybersecurity Automation Explained
Cybersecurity automation involves using programmatic solutions—often powered by AI and machine learning—to automate repeatable, human-driven tasks. Instead of security analysts manually sifting through thousands of logs or responding to every alert, automation tools can handle the initial, labor-intensive work. This includes actions such as:
- Blocking a known malicious IP address
- Quarantining an infected file
- Performing a geolocation lookup on a suspicious login
The goal is to accelerate the security workflow by handling high-volume, low-complexity tasks instantly, allowing human experts to focus their energy on the most critical threats that require nuanced decision-making.
Automation is not a single tool but a strategic approach that integrates with an organization's existing security infrastructure. It works by establishing predefined rules and playbooks—automated workflows that trigger specific actions when certain conditions are met.
For example, if a security information and event management (SIEM) system flags an event, an automated playbook can be activated to perform a series of steps: collecting additional data, enriching the threat intelligence, and even taking immediate containment actions. This reduces the mean time to detect (MTTD) and mean time to respond (MTTR) to an incident.
Cybersecurity Automation Use Cases: Four Key Areas
Manual processes cannot keep up with the volume and speed of modern attacks. By automating the following four key functions, organizations can:
- Improve their overall security posture
- Reduce the risk of human error
- Free up their human experts to focus on complex, strategic challenges
- Shift from a reactive to a proactive security posture
1. Threat Detection and Incident Response
Automating threat detection and incident response is a critical use case for any security team. When an alert is generated, automation can instantly perform a series of actions—known as playbooks—to investigate and neutralize the threat.
These playbooks can automatically enrich an alert with data from various sources, such as a user's identity, the asset's vulnerability status, and real-time threat intelligence. This automated process allows for instant containment actions, such as isolating a compromised endpoint or blocking a malicious IP address, dramatically reducing the time an attacker has to move laterally through a network.
2. Vulnerability Management
Effective vulnerability management requires a continuous and proactive approach that can be significantly enhanced with automation. Automated tools can:
- Continuously scan systems for weaknesses and misconfigurations, prioritizing them based on factors like severity and potential exploitability.
- When a new vulnerability is discovered, automation can trigger a workflow to identify affected assets, create a patch-management ticket, and track its resolution.
This ensures that critical vulnerabilities are addressed promptly and systematically, reducing the organization's overall attack surface.
3. Compliance and Governance
Maintaining regulatory compliance is an ongoing challenge that can be simplified through automation. Automated systems can continuously monitor network activity and data access to ensure compliance with policies and frameworks like GDPR, HIPAA, or SOC 2.
These tools can automatically generate detailed reports and audit trails, providing irrefutable evidence of an organization's adherence to regulatory requirements. By automating these tasks, organizations can streamline the auditing process and free up security personnel from manual, time-consuming reporting tasks.
4. Threat Intelligence and Threat Hunting
Threat intelligence is the raw information and context that allows security teams to understand and anticipate new attacks. Automation plays a vital role by:
- Continuously collecting, aggregating, and analyzing vast amounts of threat data from global sources.
- Identify emerging attack patterns.
- Correlate indicators of compromise (IoCs) across different systems
- Update security controls in real time.
This allows security teams to proactively hunt for threats that have bypassed initial defenses, using a data-driven approach to identify and neutralize sophisticated attacks before they can cause significant damage.
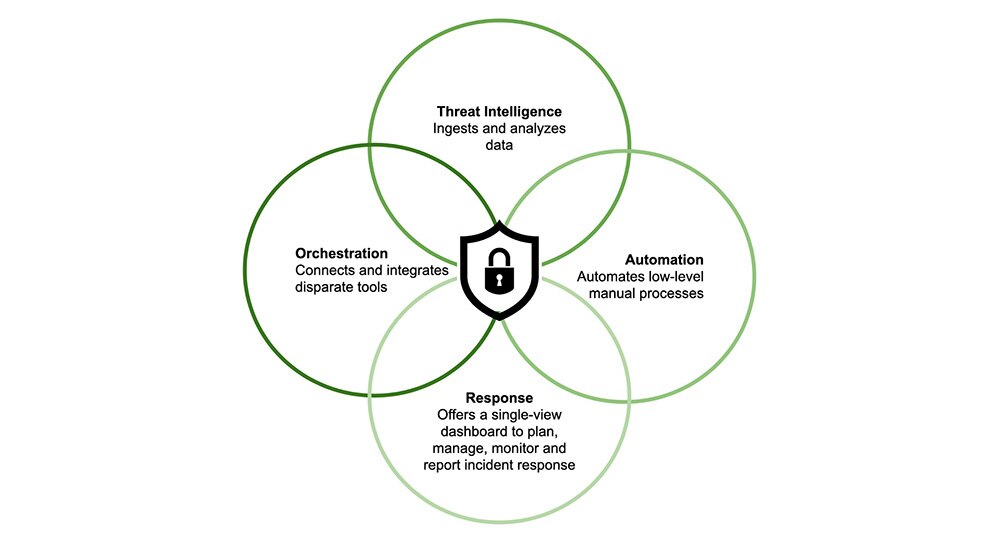
Figure 1: Elements of Security Orchestration, Automation and Response (SOAR)
How Cybersecurity Automation Works
Cybersecurity automation is not a magic bullet, but a sophisticated process that relies on key technologies working together seamlessly. The cornerstone of this approach is a technology known as security orchestration, automation, and response (SOAR).
A SOAR platform acts as a central hub, integrating various security tools, such as firewalls, endpoint detection and response (EDR) systems, and threat intelligence feeds, into a unified workflow. This integration allows information to be shared and actions to be taken automatically across the entire security stack.
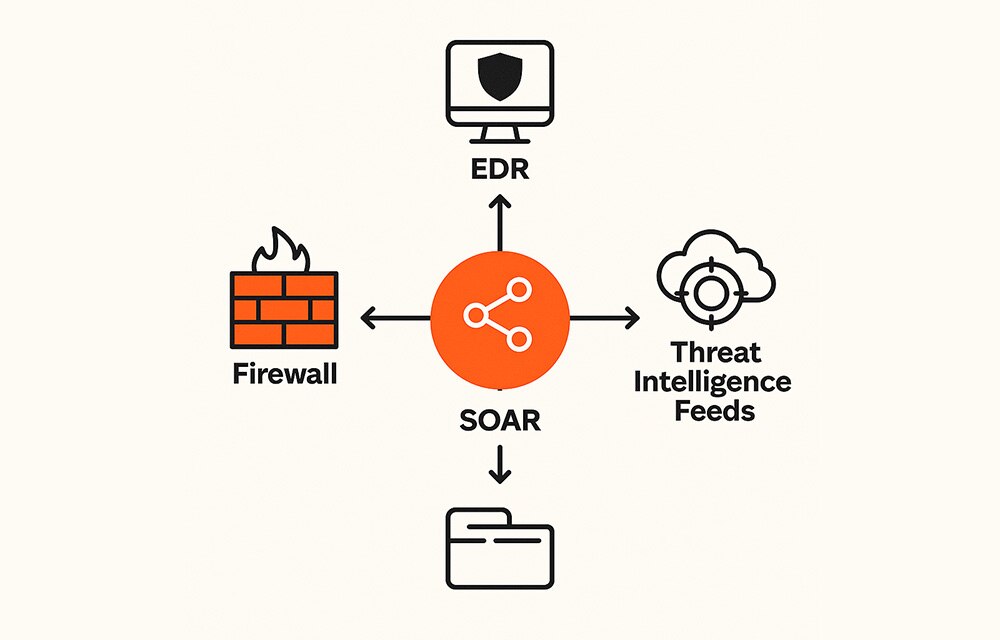
Figure 2: SOAR Platform Integration
A key component of SOAR platforms is the use of automated playbooks. A playbook is a set of predefined actions or workflows that are executed automatically when a specific security event or condition is met.
For instance, a playbook could be triggered by an alert from a SIEM system and automatically execute a sequence of actions—such as checking a user's identity, scanning a file for malware, and blocking a malicious IP address—without human intervention.
These playbooks can be simple or complex, but they are all designed to execute tasks consistently, at machine speed, and without the risk of human error. The use of AI and machine learning can further enhance these systems by helping them to analyze data, identify anomalies, and even learn from past incidents to make more intelligent decisions over time.
Benefits of Automating Your Security Operations
Automating security tasks provides significant advantages that extend beyond just technical efficiency. It fundamentally changes how security teams operate, improving their overall effectiveness and value to the organization. A considerable benefit is the ability to improve the speed and accuracy of threat detection and response, a key metric for cybersecurity effectiveness.
Reduces Alert Fatigue
Alert fatigue is a serious problem for security analysts. They are often inundated with thousands of security alerts daily, many of which are false positives or low-priority events. This constant stream of notifications can lead to burnout, and a critical alert can be missed in the noise.
Automation addresses this issue by acting as an intelligent filter. It can automatically triage, investigate, and close low-priority alerts, allowing analysts to focus on a smaller number of high-fidelity, actionable threats. This dramatically reduces the mental and emotional load on the team, ensuring they are always fresh and focused on what matters most.
Manual vs Automated Incident Response
Factor |
Manual Incident Response |
Automated Incident Response |
Time to Detect & Respond |
Often hours to days due to human analysis, manual log review, and sequential task execution. |
Minutes or seconds using automated monitoring, correlation, and predefined playbooks. |
Resource Requirements |
Requires significant human resources — analysts, investigators, and IT staff — working in shifts. |
Fewer human resources needed; automation handles repetitive tasks, freeing analysts to focus on high-level decision-making. |
Accuracy & Consistency |
Prone to human error and inconsistent processes, especially under high alert volumes. |
Consistent and repeatable actions with minimal error; machine learning can improve detection accuracy over time. |
Scalability |
Limited by staff availability and skill level; difficult to scale during major incidents. |
Easily scales to handle spikes in alerts or incidents without proportional increase in staff. |
Cost Over Time |
Higher operational costs due to labor hours, overtime, and training. |
Higher initial investment, but lower long-term operational costs through efficiency gains. |
Adaptability |
Slower to adapt to new threats; relies on manual updates to procedures. |
Rapid adaptation with automated updates, threat intelligence feeds, and continuous learning models. |
Improves the Speed and Accuracy of Threat Detection
The speed of a cyber attack can be measured in minutes, while manual incident response can take hours or even days. Automation closes this gap. By automating the investigation and response to an incident, organizations can reduce their mean time to detect (MTTD) and mean time to respond (MTTR) to a threat.
Automated playbooks can execute actions instantly, such as isolating a compromised device or blocking a malicious domain, limiting the scope of an attack almost as soon as it is detected.
A recent Unit 42 report revealed that the average time for attackers to achieve their objectives—from initial compromise to a full-scale attack—has fallen to less than 10 hours, underscoring the necessity of real-time automated defenses.
Simplifies Compliance and Auditing
Manual compliance checks and auditing processes are resource-intensive and prone to error. With automation, organizations can maintain a continuous state of compliance.
Automated systems can:
- Constantly monitor for policy violations
- Collect audit logs
- Generate reports on demand
This simplifies the auditing process, as all the necessary documentation is automatically collected and organized. Furthermore, automation ensures that compliance policies are consistently enforced across the organization, eliminating the inconsistencies that often arise from manual checks.
The Critical Role of Human Oversight
While automation is essential for keeping pace with modern threats, it cannot operate effectively without human expertise and oversight. Automated systems require skilled cybersecurity professionals to tune algorithms, investigate complex incidents, and make critical decisions that machines cannot handle alone.
Human analysts play vital roles in validating automated detections, reducing false positives, and conducting in-depth threat hunting that goes beyond algorithmic capabilities. They provide the contextual understanding needed to distinguish between legitimate business activities and genuine threats, especially in complex enterprise environments where normal behavior varies significantly.
Additionally, automated systems must be continuously monitored and adjusted by security experts who understand both the technology and the evolving threat landscape. This includes fine-tuning detection rules, updating threat models, and ensuring that automation enhances rather than replaces human judgment in security operations.
The most effective cybersecurity programs combine the speed and scale of automation with the critical thinking and adaptability that only human expertise can provide.
Challenges and Best Practices for Implementation
While the benefits of cybersecurity automation are clear, successful implementation requires a thoughtful and strategic approach. Organizations often face challenges related to integration, defining clear goals, and ensuring their teams are prepared for the transition. By following a few best practices, you can overcome these obstacles and maximize your return on investment.
The Importance of Defining Clear Goals
The first step in any automation initiative is to define what you want to achieve. Not every security task is a good candidate for automation. It is best to start by identifying repetitive, high-volume tasks that are prone to human error, such as threat enrichment or low-level alert triage.
Automating these tasks first will provide an immediate return on investment and build a foundation for more complex automation projects down the line. It is crucial to set measurable goals, such as reducing alert volume by a specific percentage or decreasing the mean time to respond to a particular type of incident.
Integrating with Existing Tools
A significant challenge for organizations is integrating new automation tools with their existing security infrastructure. An automation platform is only as effective as its ability to communicate with the rest of the security stack.
The solution is to choose a platform that offers a wide range of integrations with various security tools, including firewalls, EDR platforms, and threat intelligence feeds. The goal is to create a seamless, cohesive security ecosystem where data can flow freely and actions can be taken automatically across different systems.
Upskilling Your Team
Automation does not replace security teams; it empowers them. It frees analysts from tedious, manual tasks, allowing them to focus on more strategic and analytical work, such as threat hunting, policy development, and complex incident analysis.
As part of an automation initiative, organizations must invest in upskilling their teams. Training security professionals to build, manage, and optimize automated playbooks is essential to the long-term success of the program. This ensures that the team can get the most out of the technology while continuing to grow their professional skills.
How Automation Stops the Attack Lifecycle
Attackers use automation to move fast and deploy new threats at breakneck speeds. The only way to keep up and defend against these threats efficiently is to employ automation as part of your cybersecurity efforts.
A next-generation security platform powered by artificial intelligence rapidly analyzes data, turning unknown threats into known threats, creating an attack DNA, and automatically creating as well as enforcing a complete set of protections throughout the organization to stop the attack lifecycle.
Cybersecurity Automation FAQs
No, while both can enhance an organization’s security posture, they are different concepts. Managed security services are typically third-party services that handle security operations for an organization. Automation, on the other hand, is a technology that an organization can use internally to automate its own security tasks.
Automation is highly effective at reducing false positives. Automated playbooks can be designed to perform an initial investigation of an alert—such as checking for known benign indicators or correlating with other events—before escalating it to a human analyst. This filters out a significant number of false positives, ensuring that analysts only spend time on legitimate threats.
Yes. In fact, small businesses with limited security staff can benefit the most from automation. By automating repetitive and time-consuming tasks, a small team can achieve the efficiency of a much larger one. This allows them to manage their security posture without a significant increase in headcount.
No, automation does not replace human security professionals. It augments them by handling repetitive, low-level tasks, freeing humans to focus on high-value activities like strategic analysis, advanced threat hunting, and responding to complex, novel threats that require human judgment.
These are distinct but complementary technologies. A Security Information and Event Management (SIEM) system is used for logging and monitoring events from across a network. Endpoint Detection and Response (EDR) focuses specifically on protecting endpoints like computers and servers. A SOAR platform integrates these and other security tools to automate workflows and coordinate responses to threats.
