- 1. What qualifies as a PQC standard?
- 2. What is post-quantum cryptography (PQC)?
- 3. What PQC standards exist today?
- 4. How do global standards and policies differ on PQC?
- 5. What are the standard algorithms for PQC?
- 6. What is the role of hybrid cryptography in current standards?
- 7. What is the timeline for PQC adoption?
- 8. What should organizations do now to stay compliant?
- 9. PQC standards FAQs
- What qualifies as a PQC standard?
- What is post-quantum cryptography (PQC)?
- What PQC standards exist today?
- How do global standards and policies differ on PQC?
- What are the standard algorithms for PQC?
- What is the role of hybrid cryptography in current standards?
- What is the timeline for PQC adoption?
- What should organizations do now to stay compliant?
- PQC standards FAQs
A Complete Guide to Post-Quantum Cryptography Standards
- What qualifies as a PQC standard?
- What is post-quantum cryptography (PQC)?
- What PQC standards exist today?
- How do global standards and policies differ on PQC?
- What are the standard algorithms for PQC?
- What is the role of hybrid cryptography in current standards?
- What is the timeline for PQC adoption?
- What should organizations do now to stay compliant?
- PQC standards FAQs
PQC standards are formal documents that specify which post‑quantum algorithms are approved, how they must be implemented, and what requirements guide their use in real systems.
They include algorithm definitions, deployment instructions, validation criteria, and migration guidance. PQC standards also ensure organizations adopt quantum‑resistant cryptography in a consistent, compliant way.
What qualifies as a PQC standard?
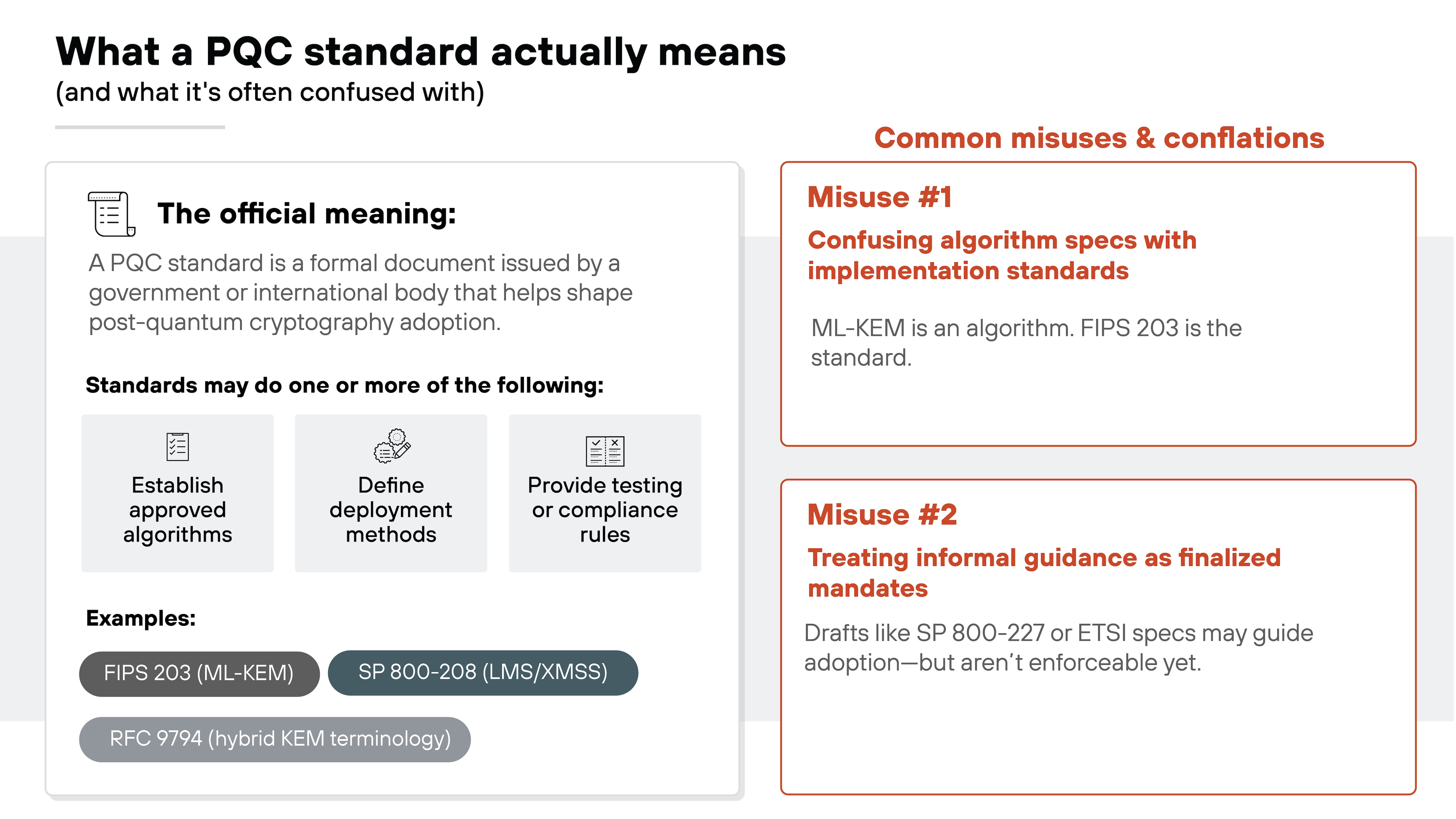
Not all post-quantum cryptography (PQC) guidance is created equal.
Some documents define algorithms. Others explain how to use them. Others still provide migration timelines or validation requirements.
So when we talk about standards, what are we really referring to?
In post-quantum cryptography, standards are formal documents issued by government or international bodies.
They serve one or more purposes:
- Establish approved algorithms
- Define how to deploy those algorithms in real systems
- Provide testing rules, compliance frameworks, or policy mandates for national security systems
They all count as standards because they formally shape how organizations adopt and implement PQC.
What is post-quantum cryptography (PQC)?
Post-quantum cryptography is about preparing for what happens when quantum computers can break today's encryption. Not just in theory—but in practice.
PQC refers to cryptographic systems that are designed to resist attacks from cryptographically relevant quantum computers. In other words, systems that can't be broken by algorithms like Shor's once quantum hardware scales.
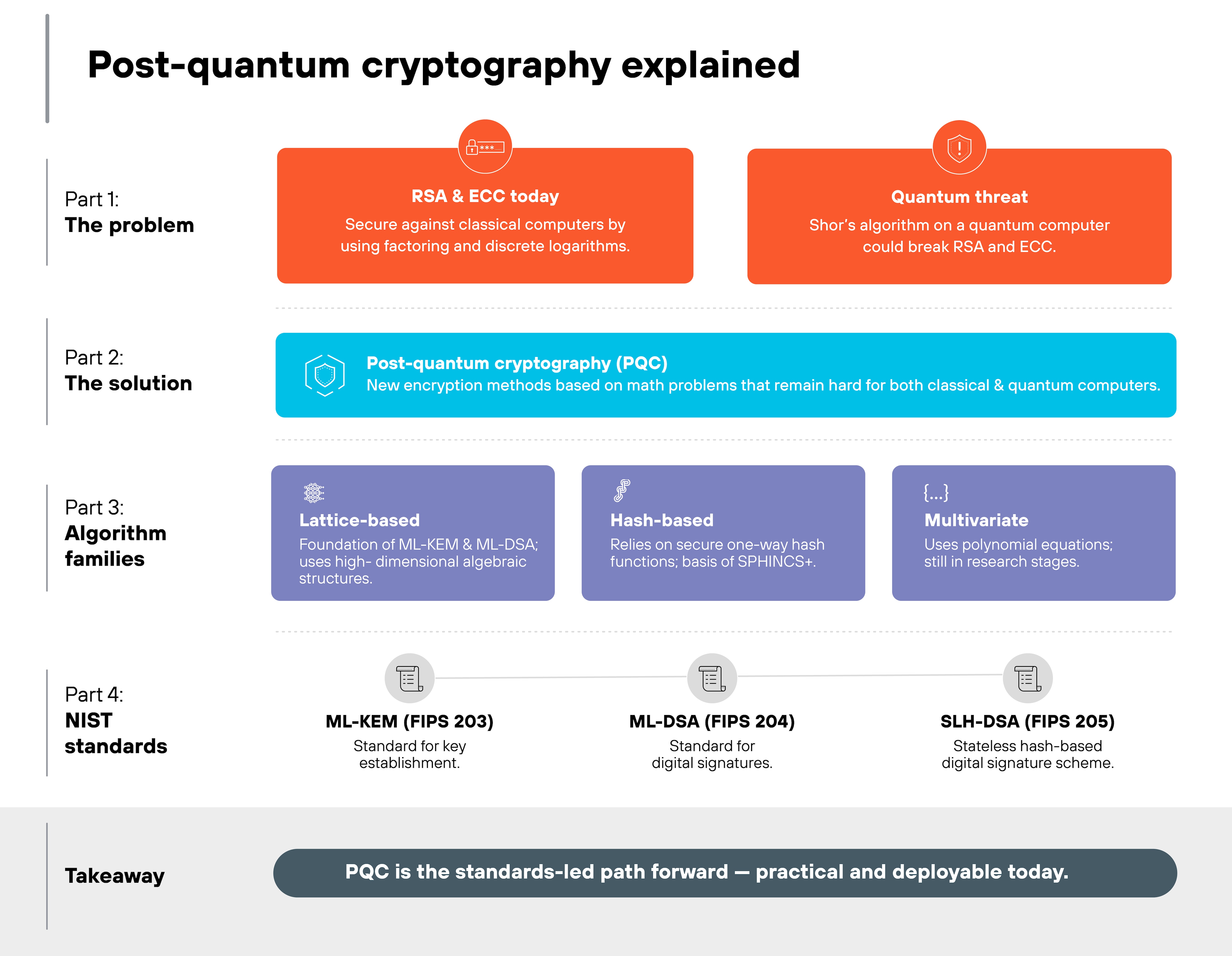
That definition spans three layers:
- Algorithms
- Standards that formally approve them
- Frameworks that guide implementation and compliance
The goal of PQC is simple. Replace vulnerable algorithms before attackers can decrypt what's encrypted today. That's why migration has already started.
- What Is Post-Quantum Cryptography (PQC)? A Complete Guide
- Harvest Now, Decrypt Later (HNDL): The Quantum-Era Threat
- What Is Quantum Key Distribution (QKD)? Overview
What PQC standards exist today?
Post-quantum cryptography doesn't rely on just one standard. It's a full ecosystem.
Again, different documents serve different roles. Some define algorithms, others enable migration, and others shape protocol integration or validation pathways.
Knowing what exists, and what stage each standard is in, helps determine readiness and plan compliant adoption.
Here's how today's key PQC standards break down:
| Post-quantum cryptography (PQC) standards at a glance |
|---|
| Standard name | Governing body | Focus | Status | Use case focus |
|---|---|---|---|---|
| FIPS 203 | NIST | Key encapsulation (ML-KEM) | Final | General-purpose key exchange |
| FIPS 204 | NIST | Digital signatures (ML-DSA) | Final | General-purpose authentication |
| FIPS 205 | NIST | Stateless hash-based signatures (SLH-DSA) | Final | Fallback digital signature use |
| FIPS 206 | NIST | FN-DSA (Falcon) | Initial public draft in development | Compact lattice-based signatures (good for constrained environments) |
| SP 800-208 | NIST | Stateful hash-based signatures (LMS, XMSS) | Final | Firmware and software signing |
| SP 1800-38 | NIST (NCCoE) | Migration to PQC | Preliminary draft / ongoing NCCoE project | Practical migration guidelines |
| SP 800-56C Rev. 2 | NIST | Key derivation for key-establishment schemes (can combine multiple shared secrets) | Final | General key derivation for classical and hybrid key exchange |
| SP 800-227 | NIST | Recommendations for key-encapsulation mechanisms (including ML-KEM and future KEMs) | Final | KEM selection, parameter sets, and transition considerations |
| ISO/IEC 23837-1:2023 | ISO/IEC | Security requirements and evaluation methods for QKD modules | Final | Assurance for QKD deployments within a broader quantum-safe architecture |
| ETSI TS 103 744 | ETSI | Hybrid key exchange constructions | Final | European guidance on migration strategies |
| RFC 9794 | IETF | Terminology for post-quantum/traditional schemes | Informational (final) | Shared language for hybrid schemes |
How do global standards and policies differ on PQC?
Not every country is adopting the same PQC roadmap.
Some focus on speed. Others prioritize flexibility, resilience, or local cryptographic independence.
That's why alignment is limited. And implementation looks different depending on where you operate.
Understanding those differences matters. Especially for organizations operating across regions or trying to deploy standards-compliant cryptography at scale.
Here's how the major standards bodies currently approach PQC:
| Global summary of PQC algorithms and policy guidance |
|---|
| Country/Agency | Recommended/Accepted KEMs | Recommended/Accepted signatures | Hybrid policy | Special notes |
|---|---|---|---|---|
| U.S. (NIST, CNSA 2.0) | ML-KEM-1024 | ML-DSA-87, LMS/XMSS | Hybrid key establishment allowed during transition; long-term goal is pure CNSA 2.0 PQC for NSS. | Pure PQC required by 2035 for NSS. |
| UK (NCSC) | ML-KEM-768 | ML-DSA-65, SLH-DSA, LMS/XMSS | Allowed as interim only. | Prefers pure PQC where feasible. |
| Germany (BSI) | ML-KEM-768/1024, FrodoKEM, McEliece | ML-DSA (3 & 5), SLH-DSA, LMS/XMSS | Recommended (except HBS). | Endorses multi-tree variants for long-term signatures. |
| France (ANSSI) | ML-KEM-768/1024, FrodoKEM | ML-DSA, SLH-DSA, FN-DSA, LMS/XMSS | Recommended. | Supports stateful and stateless hash-based signatures. |
| Netherlands (NLNCSA) | ML-KEM-1024, FrodoKEM, McEliece | ML-DSA, SLH-DSA, LMS/XMSS, HSS | Recommended. | Accepts wide range of hash-based and structured schemes. |
| Canada (CCCS) | ML-KEM | ML-DSA, SLH-DSA, LMS/HSS | Neutral. | No strong position on hybrid use. |
| Australia (ASD) | ML-KEM-768 (until 2029), ML-KEM-1024 | ML-DSA-65 (until 2029), ML-DSA-87 | Not recommended. | Favors pure PQC by 2030. |
| Korea | NTRU-HRSS, SMAUGT | HAETAE, AlMar | Not published. | National algorithm suite differs from NIST. |
| China | National PQC candidates under development | National PQC signature schemes under evaluation | Not publicly specified. | Continues domestic ECC (e.g., SM2) for classical crypto while developing separate PQC standards. |
| EU Commission | ML-KEM and others based on ETSI guidance | ML-DSA, SLH-DSA, LMS/XMSS | Recommended. | Encourages member states to adopt by 2030. |
Most countries now accept ML-KEM in some form, creating a de facto baseline for interoperability.
Signature algorithm preferences differ more widely. While some authorities endorse stateless schemes like SLH‑DSA, others mandate stateful options such as LMS or XMSS, which require strict state management to avoid key reuse.
Hybrid cryptography policies also differ. Some governments allow or recommend it as a temporary bridge. Others, like the U.S., discourage it in favor of fully post-quantum systems.
What are the standard algorithms for PQC?
Standards aren't just about guidance. They also name the specific cryptographic algorithms that meet post-quantum security requirements.
These are the building blocks. And each one is designed to resist attacks from cryptographically relevant quantum computers.
There are two core categories: key establishment and digital signatures.
Some algorithms are already standardized. Others are still in review or regionally accepted. And parameter sets matter because different use cases may call for different security levels.
Let's break them down.
| Standardized and proposed PQC algorithms by type and use |
|---|
| Algorithm | Type | Standard | Recommended use |
|---|---|---|---|
| ML-KEM | Key encapsulation | FIPS 203 | General-purpose key exchange |
| FrodoKEM | Key encapsulation | Not standardized by NIST | Regional use in EU; conservative fallback |
| Classic McEliece | Key encapsulation | Not standardized by NIST | Code-based alternative with large keys |
| HQC (planned) | Key encapsulation | NIST backup KEM (standard in development) | Future fallback option |
| ML-DSA | Signature | FIPS 204 | General-purpose digital signatures |
| SLH-DSA | Signature | FIPS 205 | Stateless fallback signature scheme |
| LMS/XMSS | Signature | SP 800-208 | Firmware signing; long-lived trust anchors |
| FN-DSA | Signature | Under evaluation | Potential future addition |
What is the role of hybrid cryptography in current standards?
Most organizations won't flip a switch and go fully post-quantum overnight.
That's where hybrid cryptography comes in.
Hybrid cryptography combines classical and post-quantum algorithms.
The goal is resilience: even if one algorithm is later broken, the other still provides security. That makes hybrids a useful transitional tool during migration.
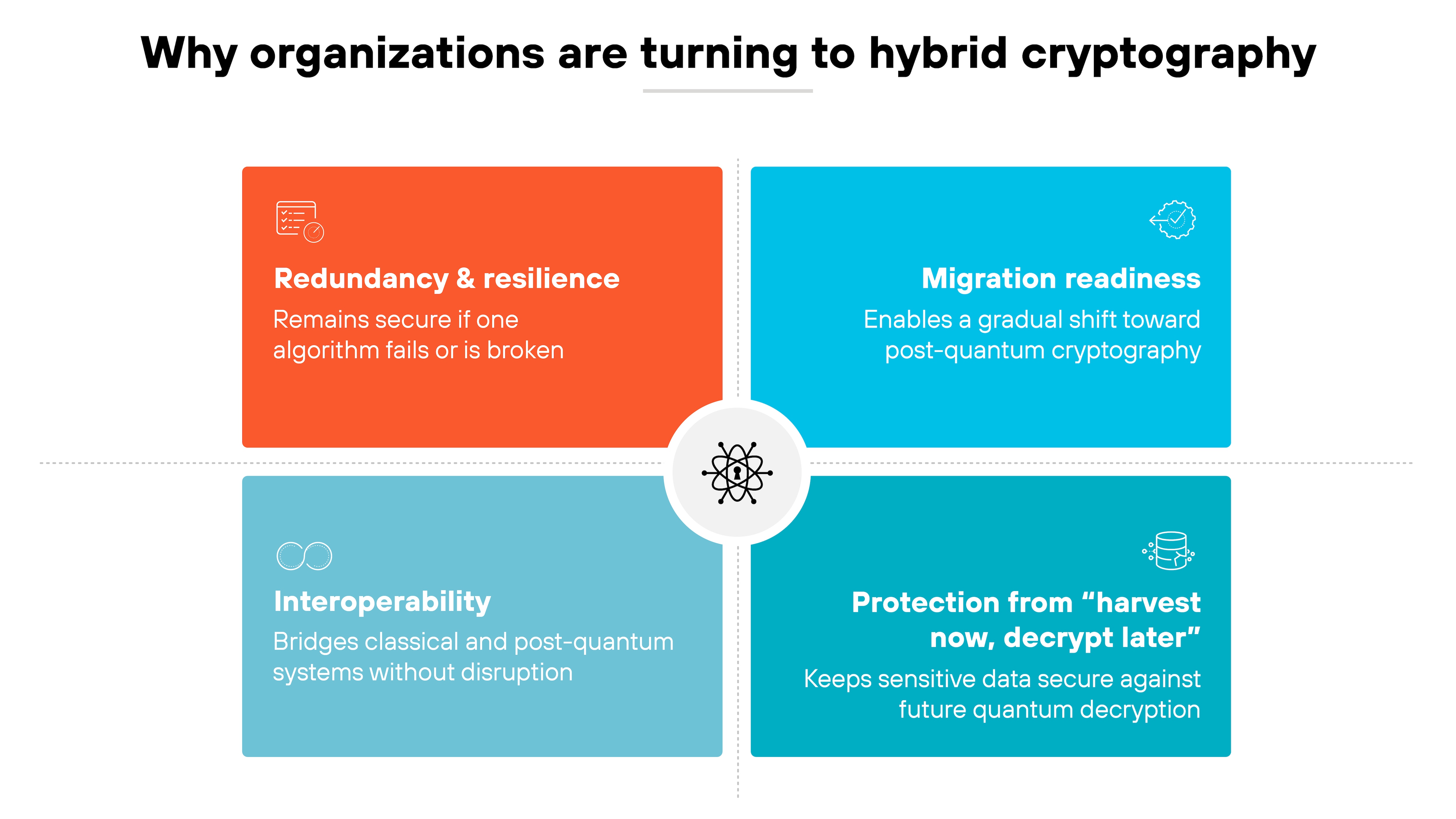
But regional policies vary:
- NIST permits hybrid key exchange using schemes like ML-KEM + X25519, but it doesn't yet support hybrid signatures.
- Meanwhile, other authorities—especially in Europe—recommend hybrid adoption as a practical interim step. Some even encourage hybrid TLS deployments now.
Here's how different regions approach hybrid cryptography:
| Regional positions on hybrid cryptography |
|---|
| Region | Policy stance |
|---|---|
| U.S. (CNSA 2.0) | Allowed for key exchange only; discouraged for signatures |
| UK (NCSC) | Permitted as interim for both KEM and signatures |
| EU (ETSI, EU Commission) | Recommended during migration |
| Germany (BSI) | Endorsed with caution |
| France (ANSSI) | Supports both hybrid KEM and signatures |
| Canada (CCCS) | Neutral stance |
| Australia (ASD) | Discourages hybrid long-term use |
Hybrid crypto is a bridge. Not a destination. The goal remains full PQC adoption. But in the meantime, it helps reduce risk, preserve interoperability, and give implementers time to transition.
What is the timeline for PQC adoption?
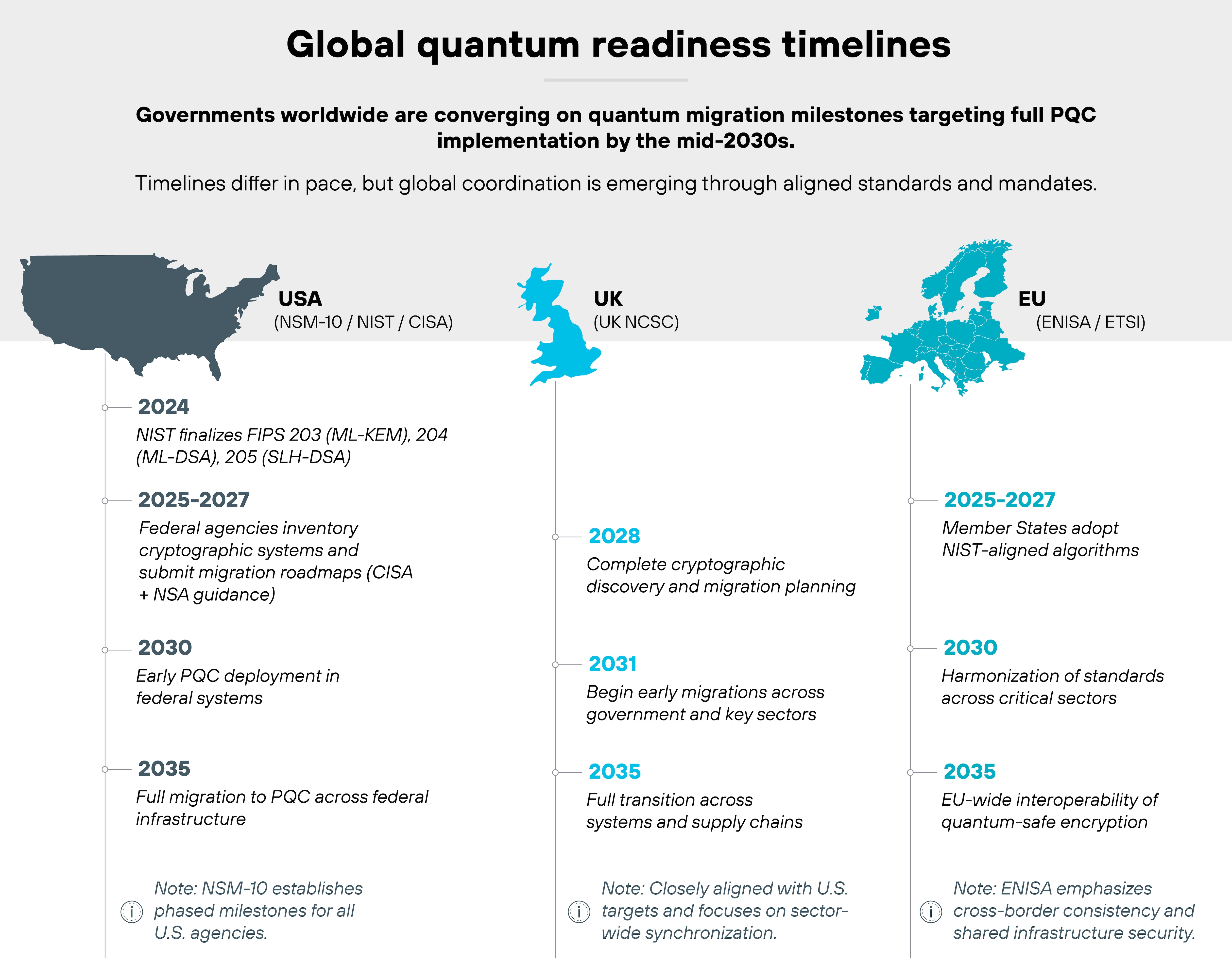
PQC adoption isn't theoretical anymore. It's underway.
Standards are only part of the equation. Timelines drive urgency. And while some deadlines are fixed, others are only guidelines.
Understanding who's mandating what, and when, is key to staying ahead of compliance risk.
| PQC standardization and migration timeline |
|---|
| Milestone | Year | Who |
|---|---|---|
| First PQC algorithms selected for standardization | 2022 | NIST |
| First FIPS finalized (203–205) | 2024 | NIST |
| CNSA 2.0 migration begins | 2025 | NSA |
| Final NIST KEM recommendations (SP 800-227) | 2025–2026 | NIST |
| Hybrid TLS deployment expands | 2025+ | Global (IETF, vendors) |
| Recommended deprecation of classical PKC | 2030 | NIST, ASD |
| Classical algorithms disallowed in NSS | 2035 | CNSA 2.0 |
The U.S. has the clearest deadlines.
CNSA 2.0 sets a hard requirement: pure post-quantum algorithms must be in place by 2035 for national security systems. The initial migration is already underway for key exchange and firmware signing.
Australia follows a similar path. ASD recommends eliminating classical public-key crypto by 2030.
Europe is moving, but less rigidly. ETSI encourages hybrid adoption and full PQC integration by 2035, but doesn't enforce exact cutoff dates
What should organizations do now to stay compliant?
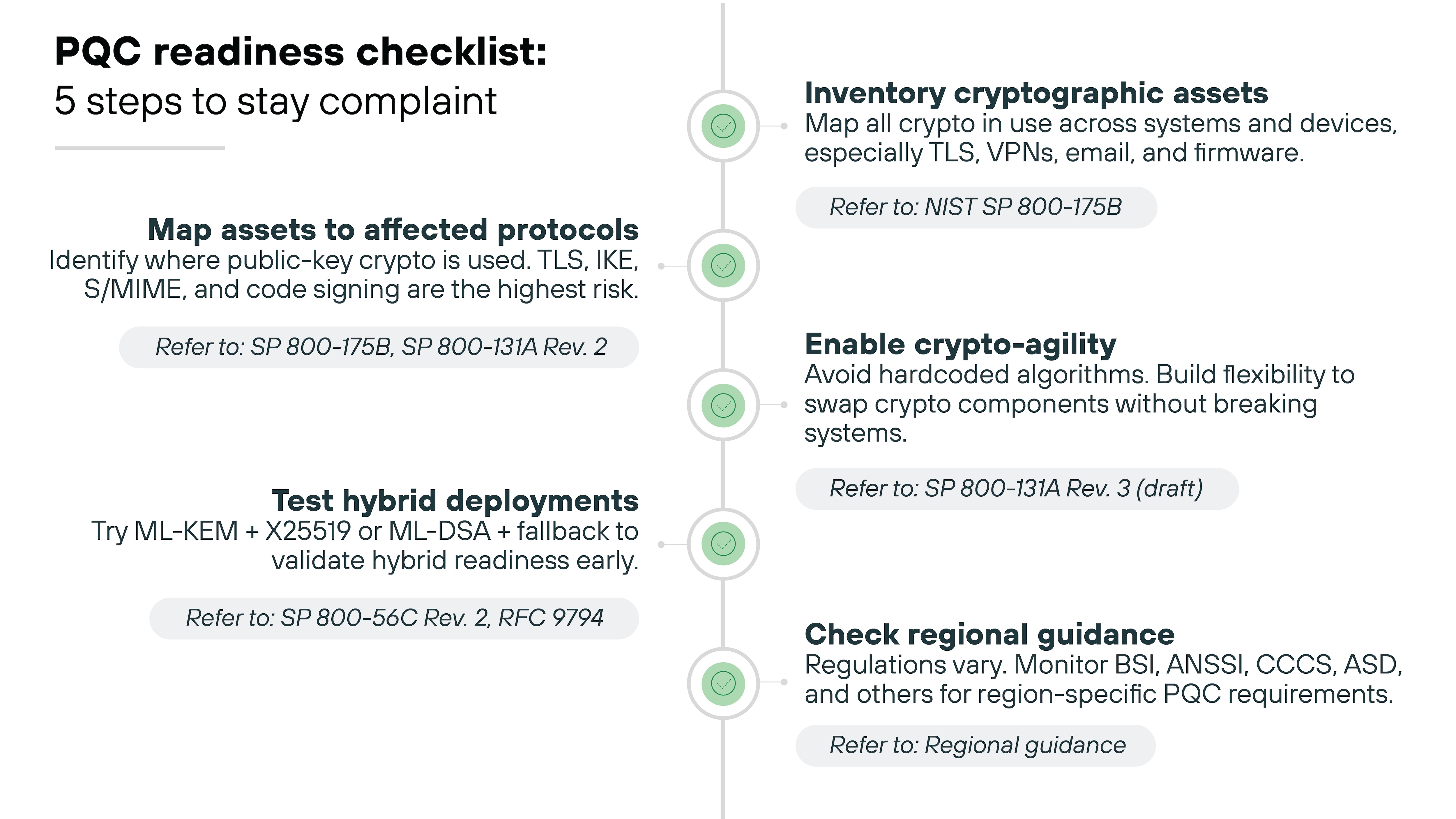
Standards are finalized. Timelines are published.
Which means: the pressure is on. Organizations need to act before migration bottlenecks, audit gaps, or vendor lag create risk exposure.
Here's what to prioritize now:
Inventory your cryptographic assets
You can't replace what you haven't mapped. Start by identifying all systems, protocols, and libraries that use cryptography. Especially in TLS endpoints, VPNs, email systems, and embedded firmware.
Refer to: NIST SP 800-175B
Map assets to affected protocols
Focus on the protocols most at risk: TLS, IKE, S/MIME, and code signing. These depend on public-key cryptography, which quantum computers will break first.
Refer to: NIST SP 800-175B, SP 800-131A Rev. 2
Enable crypto-agility wherever possible
Hardcoded algorithms will slow your migration. Design systems to support swapping cryptographic components without rewriting application logic.
Refer to: NIST SP 800-131A Rev. 3 (draft)
Start testing ML-KEM and ML-DSA in hybrid deployments
Don't wait for production deadlines. Hybrid combinations like ML-KEM + X25519 or ML-DSA with fallback can help validate early compatibility.
Refer to: SP 800-56C Rev. 2, RFC 9794
Monitor your local authority's guidance
Each country's path looks different. Check BSI, ANSSI, CCCS, ASD, and others for region-specific requirements that may go beyond NIST.
Refer to: Regional guidance (BSI, ANSSI, ASD, CCCS, etc.)
Staying compliant with PQC standards isn't just about paperwork. It's about building resilience before timelines harden and options disappear.
- Quantum Readiness: What It Means and How to Achieve It
- Cryptographic Agility: The Key to Quantum Readiness