Quantum Readiness: What It Means and How to Achieve It
Quantum readiness is organizational preparedness to transition from current cryptographic systems to post-quantum security. It involves understanding where cryptography is used, assessing which data and systems are most at risk, and planning migration to quantum-resistant algorithms.
Achieving quantum readiness requires coordinated action across governance, risk management, technology, and vendor ecosystems to ensure encryption can be replaced safely and on time.
Why does quantum readiness matter now?
Quantum computers powerful enough to break today's encryption don't exist yet. But attackers aren't waiting.
They're already collecting sensitive data in what's known as harvest-now-decrypt-later attacks.
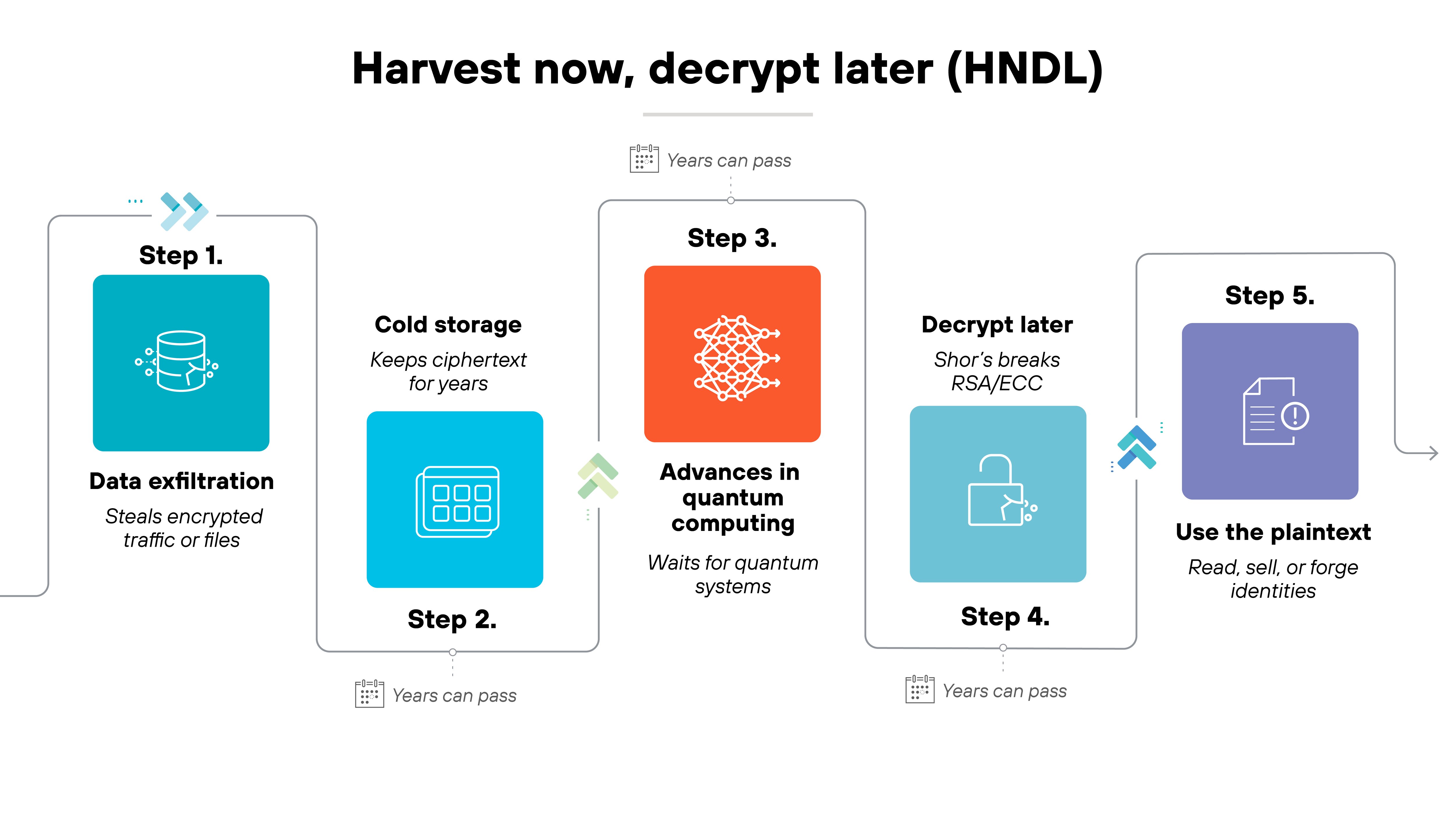
Once a large-scale quantum computer becomes available, that stored data could be decrypted instantly.
Which means organizations need to act before the threat materializes. They need to get quantum ready.
But migration to post-quantum cryptography takes time.
Experts broadly agree that migration will take years of discovery, testing, and coordination. Most organizations still lack a full inventory of where encryption is used across their environments.
However, government policy is already pushing the timeline forward.
In the United States, National Security Memorandum 10 sets a 2035 goal for full migration to post-quantum cryptography, with early milestones already underway. That's not far off for complex infrastructure that still depends on legacy cryptography.
Ultimately:
Quantum readiness isn't a theoretical exercise.
It's part of a broader secure-by-design modernization effort. One that ensures today's systems can adapt safely to tomorrow's cryptographic standards.
- What Is Post-Quantum Cryptography (PQC)? A Complete Guide
- 8 Quantum Computing Cybersecurity Risks [+ Protection Tips]
- Harvest Now, Decrypt Later (HNDL): The Quantum-Era Threat
Breaking down the five pillars of quantum readiness
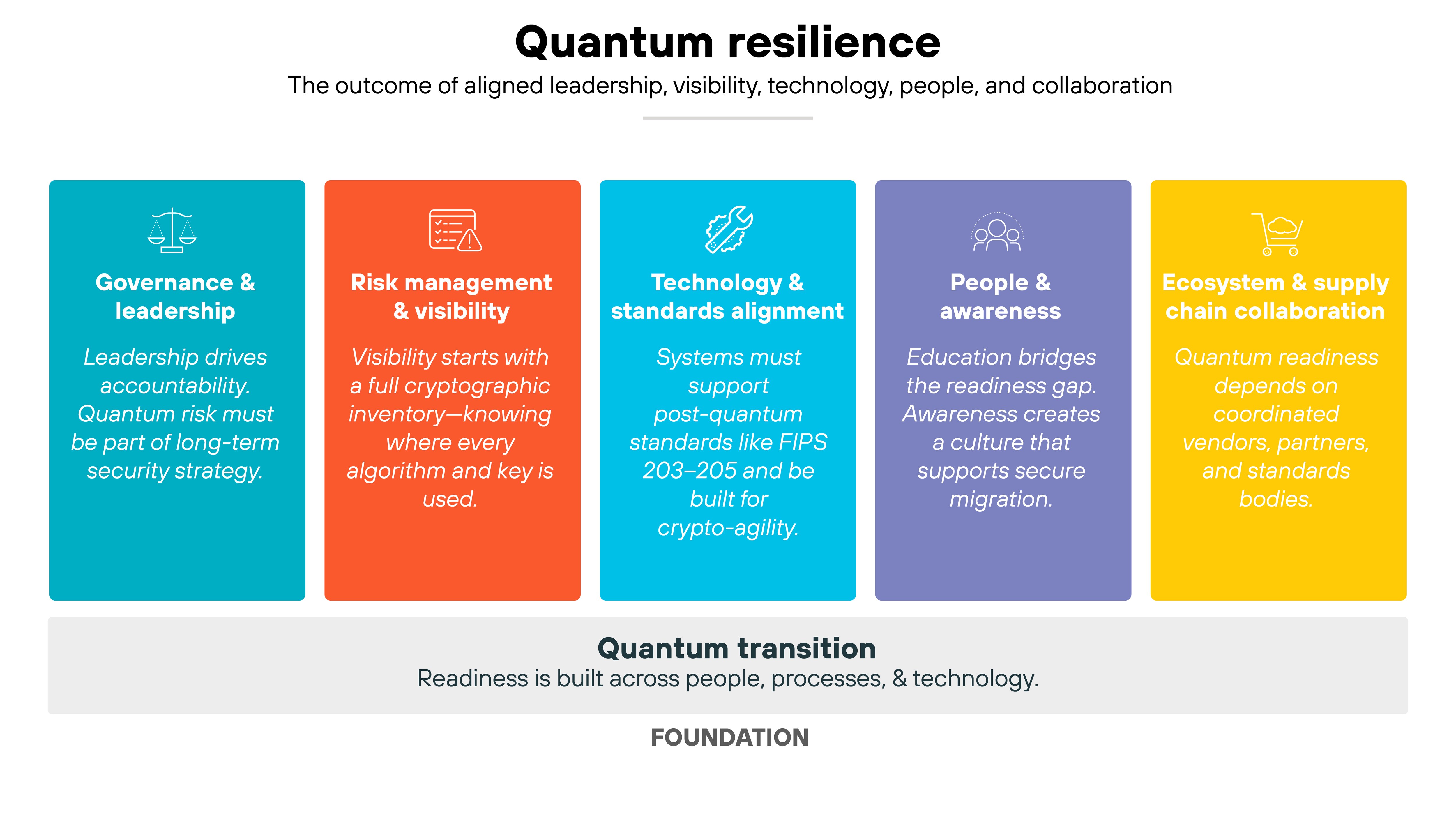
Quantum readiness isn't achieved through one project or policy. It's built across every part of an organization.
Experts across government, standards organizations, and the private sector describe readiness as a combination of leadership, visibility, technology, people, and collaboration. Together, these areas form the five pillars of a resilient quantum transition.
Let's look at how each one contributes to building true quantum readiness.
Pillar 1: Governance and leadership
Quantum readiness starts with leadership.
Executive ownership ensures quantum risk isn't treated as a side project. It becomes a part of long-term security strategy.
Why?
Because decisions about post-quantum migration affect every system, vendor, and compliance requirement.
A clear governance model defines who is accountable for the transition and how progress will be measured. That includes building a quantum readiness roadmap. Which is a structured plan for inventory, testing, and implementation.
It also means integrating quantum risk into existing governance frameworks.
Ultimately, without leadership and accountability, readiness remains a concept instead of a capability.
Pillar 2: Risk management and visibility
Organizations can't manage what they can't see. That's why cryptographic visibility is central to quantum readiness.
Leading agencies and standards bodies recommend starting with a complete cryptographic inventory.
This process identifies where quantum-vulnerable algorithms are used across IT and OT environments. Every place data is encrypted, signed, or verified must be mapped and prioritized.
Risk assessment follows.
Teams evaluate which assets protect long-life or mission-critical data. AKA information that must remain confidential for decades. And that insight helps determine which systems to migrate first and where temporary safeguards, like segmentation, may be needed.
Good visibility also supports crypto-agility.
When algorithms change, organizations with clear inventories can adapt faster and more safely.
Pillar 3: Technology and standards alignment
Technology readiness means ensuring systems can support emerging post-quantum standards and algorithms.
NIST has already finalized the first three post-quantum standards: ML-KEM (FIPS 203), ML-DSA (FIPS 204), and SLH-DSA (FIPS 205).
Here's why that matters:
Systems and products must be built or updated to use those algorithms once finalized. And that includes testing hybrid cryptographic models that combine classical and quantum-resistant methods.
Crypto-agility—the ability to swap algorithms without re-architecting entire systems—is also essential. Building that capability often requires modernizing infrastructure and decoupling cryptographic functions from applications.
In practice, technology alignment ensures that when PQC standards are released, organizations can integrate them quickly, securely, and with minimal disruption.
Pillar 4: People and awareness
Quantum readiness isn't only a technical problem. It's also a people challenge.
Research consistently shows that awareness and skills are among the biggest readiness gaps. Few employees understand quantum risk or how it affects their work.
Fortunately, organizations can change that by raising awareness across teams.
Training should explain quantum risk in practical terms. Not theoretical physics. It should also help engineers, developers, and risk managers recognize where cryptography is used in their systems.
On the leadership side, C-suite and security executives need enough understanding to allocate resources and set priorities.
Readiness starts with education. And culture follows awareness.
Pillar 5: Ecosystem and supply chain collaboration
No organization operates alone. Quantum migration depends on vendors, service providers, and partners updating their own systems.
That's why collaboration is the fifth pillar.
Organizations should work with vendors to understand their post-quantum migration plans and ensure crypto-agility is built into contracts and procurement requirements.
Collaboration also extends to industry groups and standards bodies. Sharing lessons learned across ecosystems accelerates adoption and reduces duplication of effort.
The takeaway is this: Quantum security isn't achieved in isolation. It's built together, through coordination and shared accountability across the digital supply chain.
How to achieve quantum readiness in 6 steps
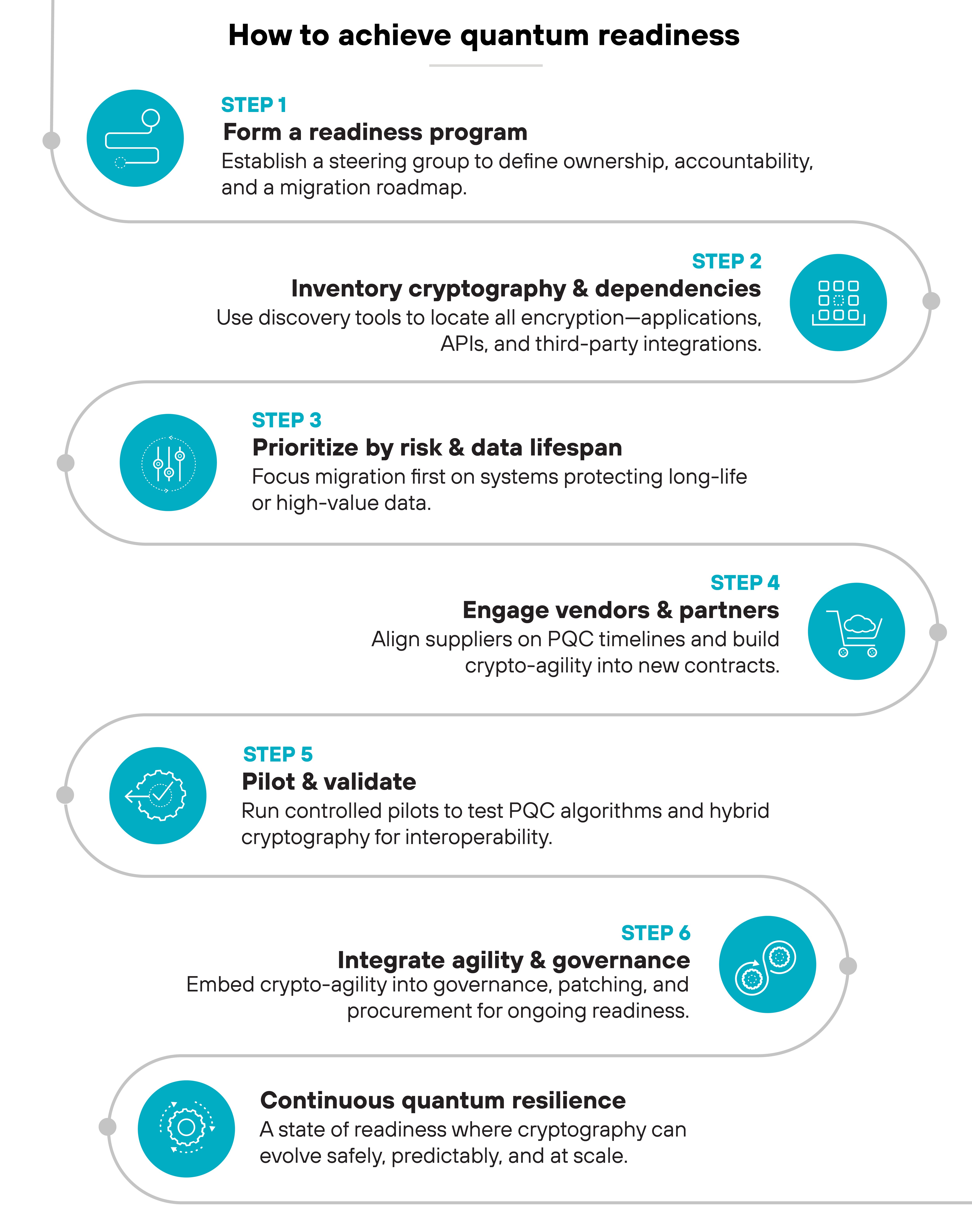
Turning quantum readiness into action requires more than awareness. It demands structured planning, coordination across teams, and time to execute safely.
The steps that follow outline a practical path for organizations to move from preparation to implementation.
Step 1: Form a readiness program
Start by creating a dedicated steering group.
Include leaders from security, IT, procurement, and legal. Their first job is to define scope and ownership. And that means someone has to be accountable for the migration roadmap.
This team coordinates risk assessments, vendor discussions, and project timelines. It also reports progress to senior leadership and integrates readiness goals into broader modernization efforts.
Step 2: Inventory cryptography and dependencies
Next, find out where cryptography lives.
That includes applications, APIs, devices, and third-party integrations.
Using discovery tools to identify algorithms, key types, and encryption dependencies. The result should be a complete inventory. One that connects systems, data classifications, and business functions.
Because without visibility, it's impossible to plan a safe transition to post-quantum cryptography.
Step 3: Prioritize by risk and data lifespan
Not all data is equal. Again, some information—like health records, trade secrets, or classified data—must stay confidential for decades.
Prioritize these assets first. Map them against current cryptographic protections to determine where quantum risk is highest.
The bottom line: focus early migration on systems that protect long-life or high-value data.
Step 4: Engage vendors and partners
Quantum migration extends beyond internal systems. It depends on suppliers adopting post-quantum standards too.
Ask vendors for their PQC timelines and migration plans.
For new contracts, include crypto-agility requirements. That ensures future updates can replace algorithms as standards evolve.
Step 5: Pilot and validate
Before scaling, test.
Use pilot projects to evaluate draft PQC algorithms, hybrid models, and integration performance.
This phase validates interoperability and identifies any latency or compatibility issues early. It's safer. And more efficient.
Step 6: Integrate agility and governance
Finally, make quantum readiness continuous.
Update procurement and patching policies to require crypto-agility. Add quantum risk metrics to governance frameworks and annual audits.
The goal: to ensure encryption can be replaced safely, predictably, and at scale. Without starting from zero every time standards change.
EBOOK: NAVIGATING THE QUANTUM SHIFT - A PRACTICAL ROADMAP
Learn what quantum risk means for your organization and how to prepare in practice.
Download eBookHow do timelines and mandates line up globally?
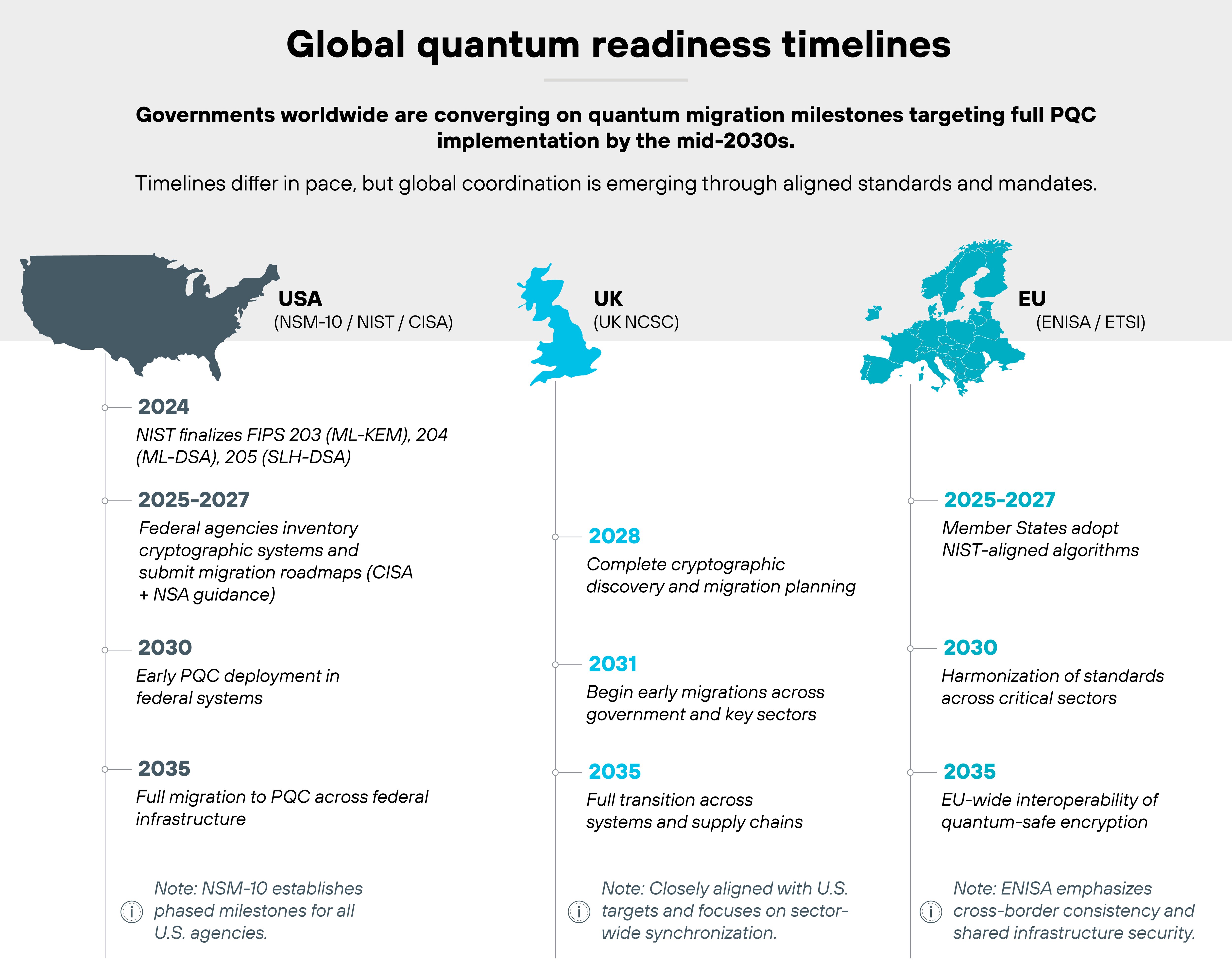
Quantum readiness is now guided by formal standards and clear migration timelines. Governments are moving from planning to execution.
As noted earlier, the United States National Security Memorandum-10 directs all federal agencies to complete migration to post-quantum cryptography by 2035.
The milestones are already in motion. We broke down how NIST finalized its first three standards in 2024, and agencies are now inventorying cryptographic systems, identifying high-value assets, and reporting progress through coordinated NIST, CISA, and NSA programs.
The United Kingdom has outlined similar milestones through the UK NCSC. By 2028, organizations should complete cryptographic discovery and migration planning. Early migrations should follow by 2031, with full implementation across systems and supply chains by 2035.
Across the European Union, ENISA and ETSI are aligning Member State adoption with these same standards. Their focus is on interoperability—ensuring that quantum-safe encryption works seamlessly across borders and within shared infrastructure.
In short: timelines now differ only in detail, not direction. The world is coalescing around a synchronized transition to post-quantum cryptography by the mid-2030s, anchored by common standards and coordinated national mandates.
What's next on the quantum readiness journey?
Quantum readiness doesn't end when migration begins. It evolves as new algorithms, standards, and attack models emerge.
As NIST, ISO, and national standards bodies advance post-quantum cryptography, organizations must treat readiness as continuous. Not a one-time replacement.
The next stage is cryptographic lifecycle management.
That means monitoring algorithm changes, automating key management, and verifying that systems remain compliant as standards evolve. It also requires coordination—across industries, vendors, and governments—to ensure consistent implementation worldwide.
The key point: automation and governance will determine the difference between being ready once and staying ready.
Organizations that embed agility into their processes now will adapt smoothly as quantum-safe technologies scale. Those that wait will face a steeper, riskier transition when quantum attacks become practical.
