A Complete Guide to SASE Architecture
SASE architecture is the structural design that defines how secure access service edge is implemented and operated.
It separates the control plane from the data plane, delivers networking and security functions through distributed points of presence, and applies single-pass inspection to traffic. Policies and visibility are managed through one control plane, creating consistency across all users, devices, and locations.
How does SASE architecture work?
SASE (secure access service edge) architecture works by converging networking and security into a unified cloud-based framework.
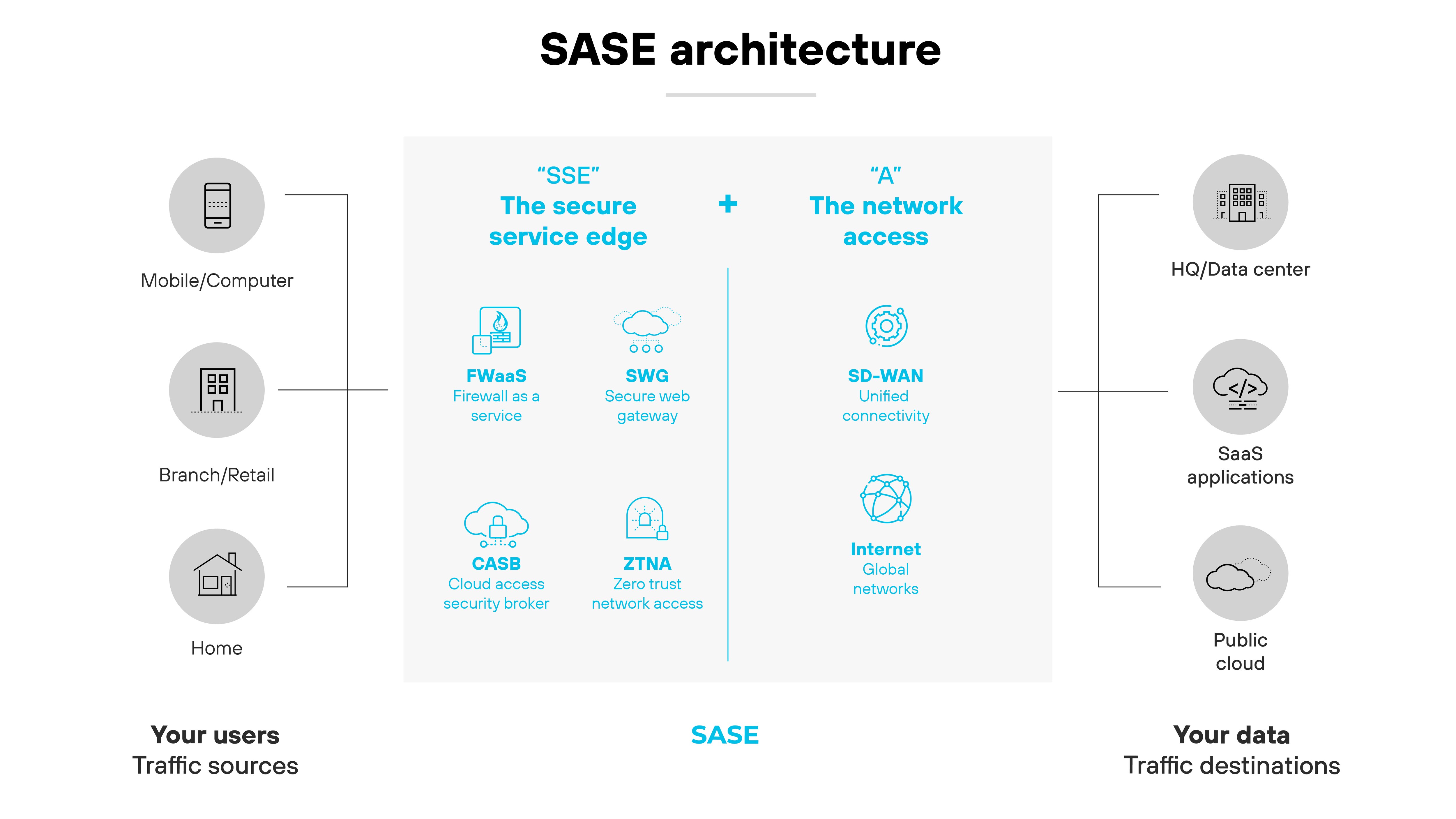
At its core, it brings together SD-WAN (software-defined wide area network) with security functions such as SWG (secure web gateway), CASB (cloud access security broker), ZTNA (zero-trust network access), and FWaaS (firewall as a service).
These elements are delivered as integrated services rather than separate point products. The architecture is less about individual features and more about how they're combined and delivered as one system.
SASE architecture separates the control plane from the data plane. The control plane manages policy and orchestration. The data plane enforces those policies as traffic flows.
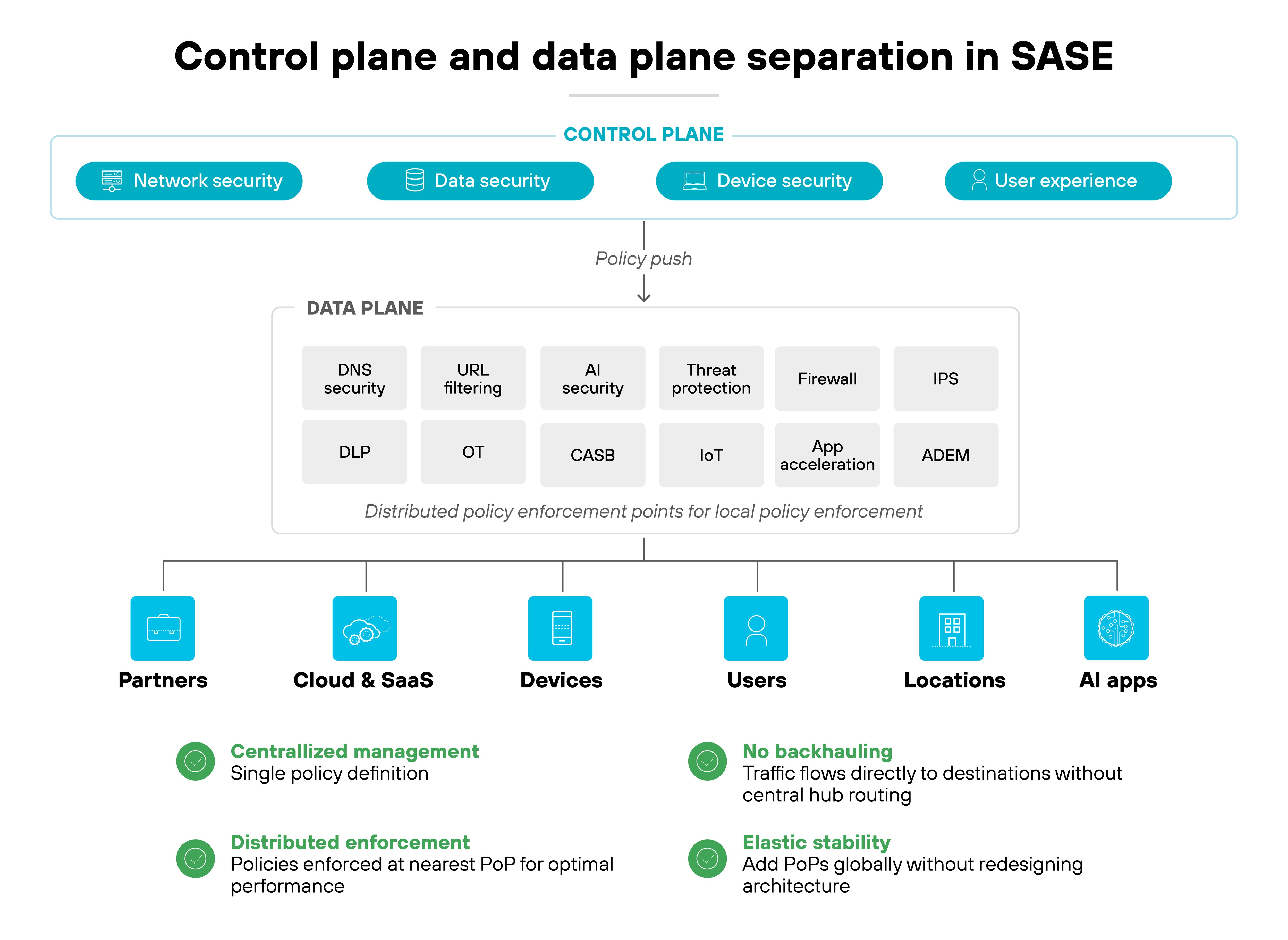
The split allows policies to be managed centrally while enforcement happens as close to users and applications as possible. Which means organizations can scale and maintain consistency without forcing all traffic back through a single choke point.
Cloud-native points of presence (PoPs) extend these enforcement capabilities worldwide.
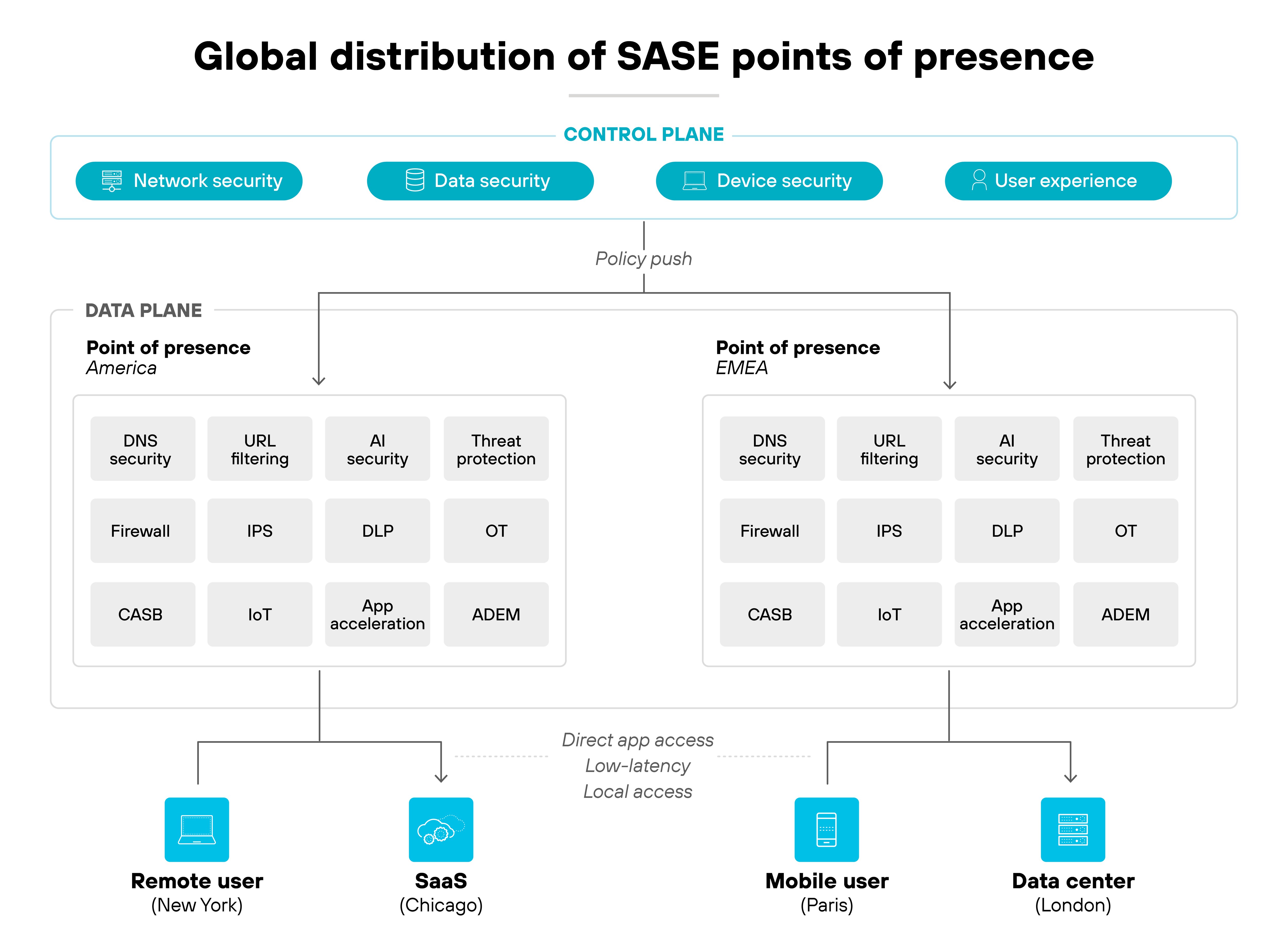
SASE vendors deploy PoPs in metro areas across multiple continents. That way, traffic can be inspected and secured near the source. This avoids unnecessary backhauling and improves user experience. Some vendors also allow organizations to select where inspection happens to meet performance or compliance needs.
SASE also uses a single-pass inspection model.
Traffic is decrypted once, inspected against multiple security policies, and then re-encrypted. That inspection covers malware, sensitive data, and access controls.
Unified management is core to SASE architecture design.
Instead of switching between multiple consoles, administrators use a single control plane to define and enforce policies across all services. That includes visibility, troubleshooting, reporting, and advanced analytics. The goal is to simplify operations and reduce the chance of configuration errors that occur when managing separate tools.
- SD-WAN vs. SASE: Where One Ends and the Other Begins
- SD-WAN vs. SASE vs. SSE: What Are the Differences?
INTERACTIVE WALKTHROUGH
See firsthand how Prisma SASE components work together.
Launch experience
How is a SASE architecture deployed?
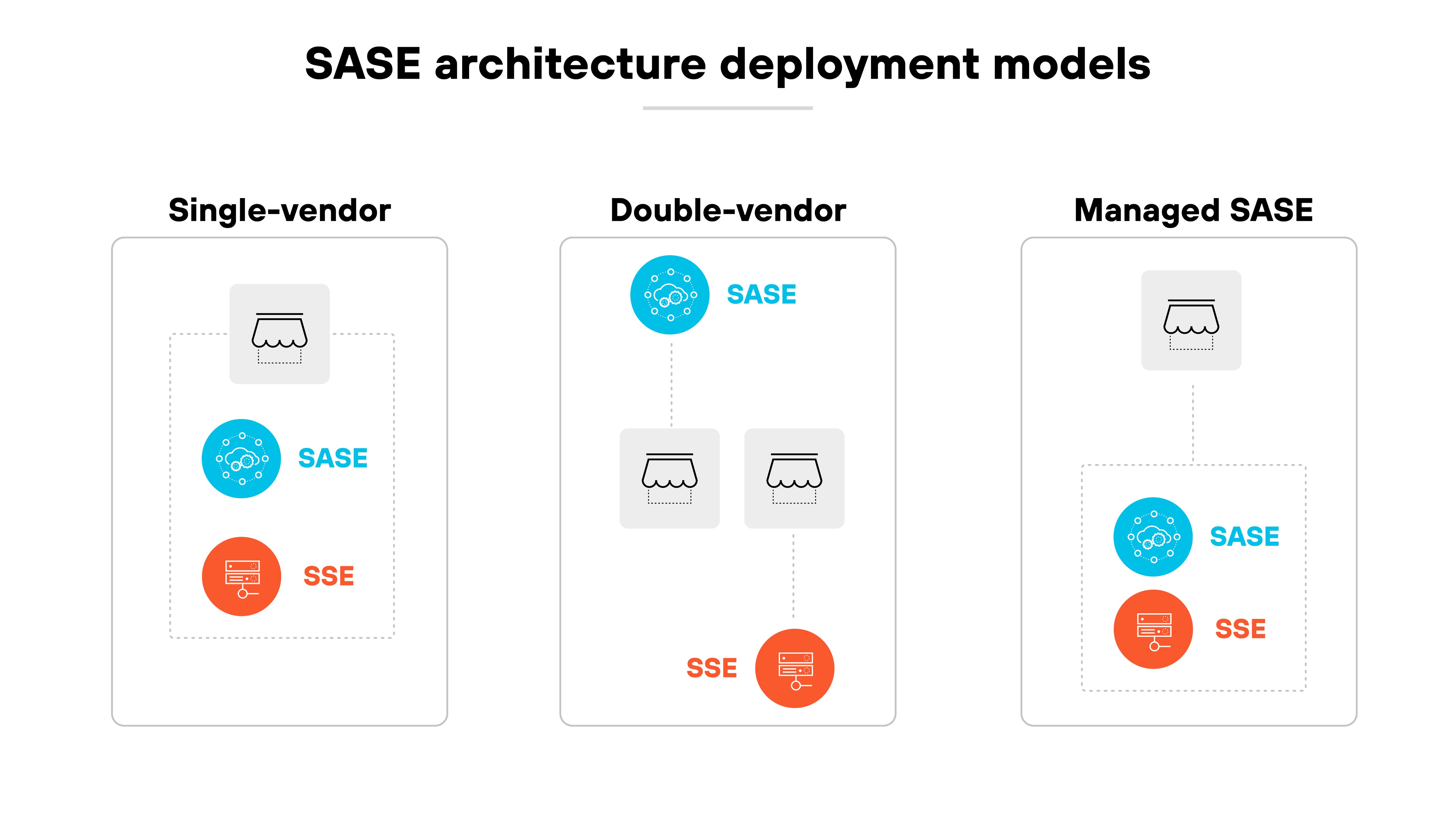
The three most common ways to deploy SASE architecture are:
- Single-vendor
- Dual-vendor
- Managed SASE
Each reflects how organizations choose to consume the architecture rather than differences in the technology itself.
In a single-vendor deployment, one provider delivers both networking and security services.
That means SD-WAN and the full security service edge (SSE) stack are integrated into a single platform. The appeal here is simplicity. Organizations gain one management plane, one data model, and one support contract.
And adoption is rising quickly.
A dual-vendor approach combines offerings from two providers—typically one for SD-WAN and one for SSE.
This is still the most common model in the market today. It allows organizations to pair an incumbent SD-WAN with a preferred security provider, or vice versa. The tradeoff is complexity. Integration between management planes and data planes is improving but not always seamless.
Then there's managed SASE. Here, a service provider designs, deploys, and operates the architecture on behalf of the enterprise.
This approach can reduce internal burden for organizations with limited staff or expertise. Market adoption has been slower than single-vendor or dual-vendor models. Most organizations still prefer direct control over configuration, visibility, and performance.
Each option comes with design tradeoffs:
- Single-vendor platforms simplify management but may not always match best-of-breed depth in every feature.
- Dual-vendor deployments provide flexibility but increase integration overhead.
- Managed services can speed time to adoption but may limit control and visibility.
Which path an organization chooses often depends on existing contracts, internal skills, and long-term IT strategy.
How is SASE architecture different from legacy models?
Legacy WAN and security architectures were built for centralized data centers and fixed offices. But SASE takes a different approach. It was designed for distributed users, cloud applications, and global networks.
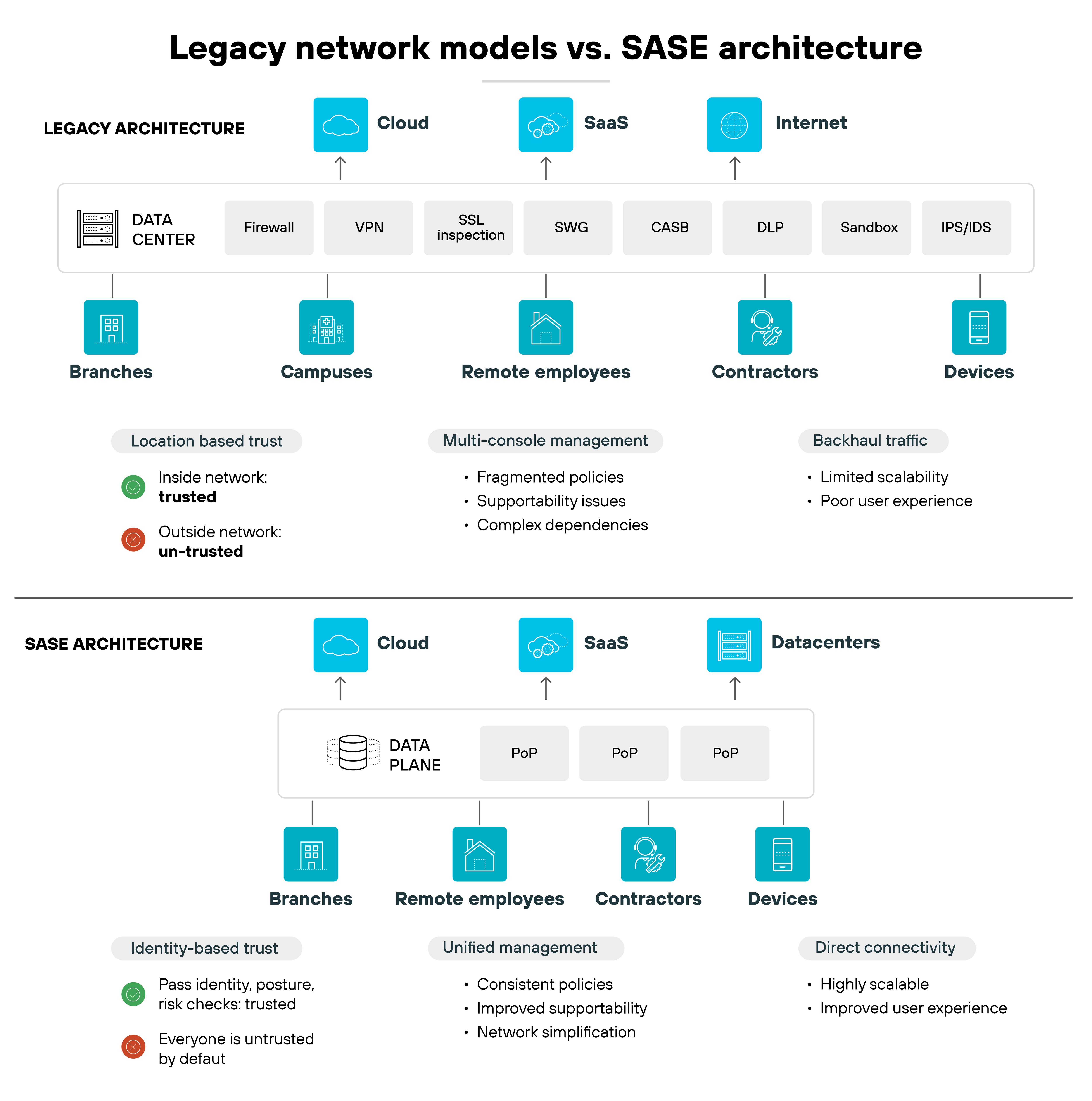
Legacy networks often followed a hub-and-spoke model.
All traffic was backhauled through a central site before reaching the internet or cloud. This created bottlenecks. SASE uses globally distributed points of presence (PoPs) to enforce policy closer to users. So traffic is secured near its source, avoiding unnecessary detours.
Earlier architectures also relied heavily on appliances.
Organizations stacked routers, firewalls, and web gateways in branch offices or headquarters. Scaling required adding more hardware. But SASE delivers these same functions as converged, cloud-native services. And that reduces the need for appliance sprawl and simplifies updates.
Trust was once tied to being “inside the network.”
Anyone on the corporate LAN was often considered trusted. That model breaks down in a cloud-first world. SASE applies zero-trust principles everywhere. Access is based on user identity, device posture, and context, not physical location.
Management is another difference.
Traditional environments forced administrators to use multiple consoles for SD-WAN, firewalls, and cloud security tools. Policies had to be duplicated across systems. SASE replaces this with a unified control plane. Administrators define policies once, and they're applied consistently across all services.
In short:
Legacy models were location-bound, appliance-heavy, and fragmented. SASE is cloud-native, identity-driven, and unified. The result is an architecture better suited for today's distributed work and application environments.
How does SASE architecture apply in practice?
SASE architecture enables several real-world applications by design, with the most common including:
- Securing branch locations
- Applying zero trust everywhere
- Supporting remote users
- Consolidating multiple functions into a unified framework
Let's dive into each in a bit more detail.
Secure branch modernization happens when branches connect directly to nearby points of presence (PoPs). Networking and security functions are delivered from the cloud, and policies are enforced consistently through a single control plane. This reduces the need for complex branch infrastructure while maintaining uniform protection.
Zero-trust SASE applies identity- and context-based checks across the environment. The control plane evaluates users, devices, and sessions in real time, while enforcement happens at distributed PoPs. So the same access policies follow users wherever they connect.
“Coffee shop” networking describes how remote or mobile users get the same level of inspection as if they were on campus. Traffic is secured close to its source, and single-pass inspection ensures it is decrypted and checked once before moving on. This helps balance security with predictable performance.
Foundational consolidation comes from unifying SD-WAN and the security service edge into one architecture. Administrators manage policies, visibility, and reporting through a single console. The result is lower operational overhead and fewer opportunities for misconfiguration across tools.
