What Is SD-Branch? | Architecture & Modern Role
SD-Branch is a branch network architecture that combines SD-WAN, LAN, Wi-Fi, and security functions into a single, centrally managed platform.
It was developed to simplify infrastructure at remote sites by reducing the number of standalone devices and management systems. The architecture is technically still used but is increasingly integrated into broader SASE deployments.
Why did SD-Branch emerge in the first place?
Branch environments became too complex. That's the short version.
IT teams were managing separate tools for WAN, LAN, Wi-Fi, and firewall functions. Each one required its own interface, deployment, and support model. And none of them were built to work together.
Meanwhile, branches kept multiplying. So did the devices inside them.
More users. More IoT endpoints. More cloud applications. All trying to connect from a location that usually had no IT staff on-site.
In other words:
The traditional branch stack didn't scale. It was expensive, hard to secure, and nearly impossible to manage across hundreds—or even thousands—of sites.
In the late 2010s and early 2020s, vendors began positioning SD‑Branch (software-defined branch) as the solution. It unified multiple networking and security functions into a single, remotely managed platform. And it allowed IT to roll out new sites faster, with more visibility and control.
That's what made it compelling. Not just the architecture. But the operational model behind it.
How is SD-Branch different from SD-WAN and SASE?
They're not interchangeable. But they're often confused.
SD-WAN is about WAN connectivity. It uses software-defined routing to connect sites, optimize application traffic, and move away from traditional MPLS.
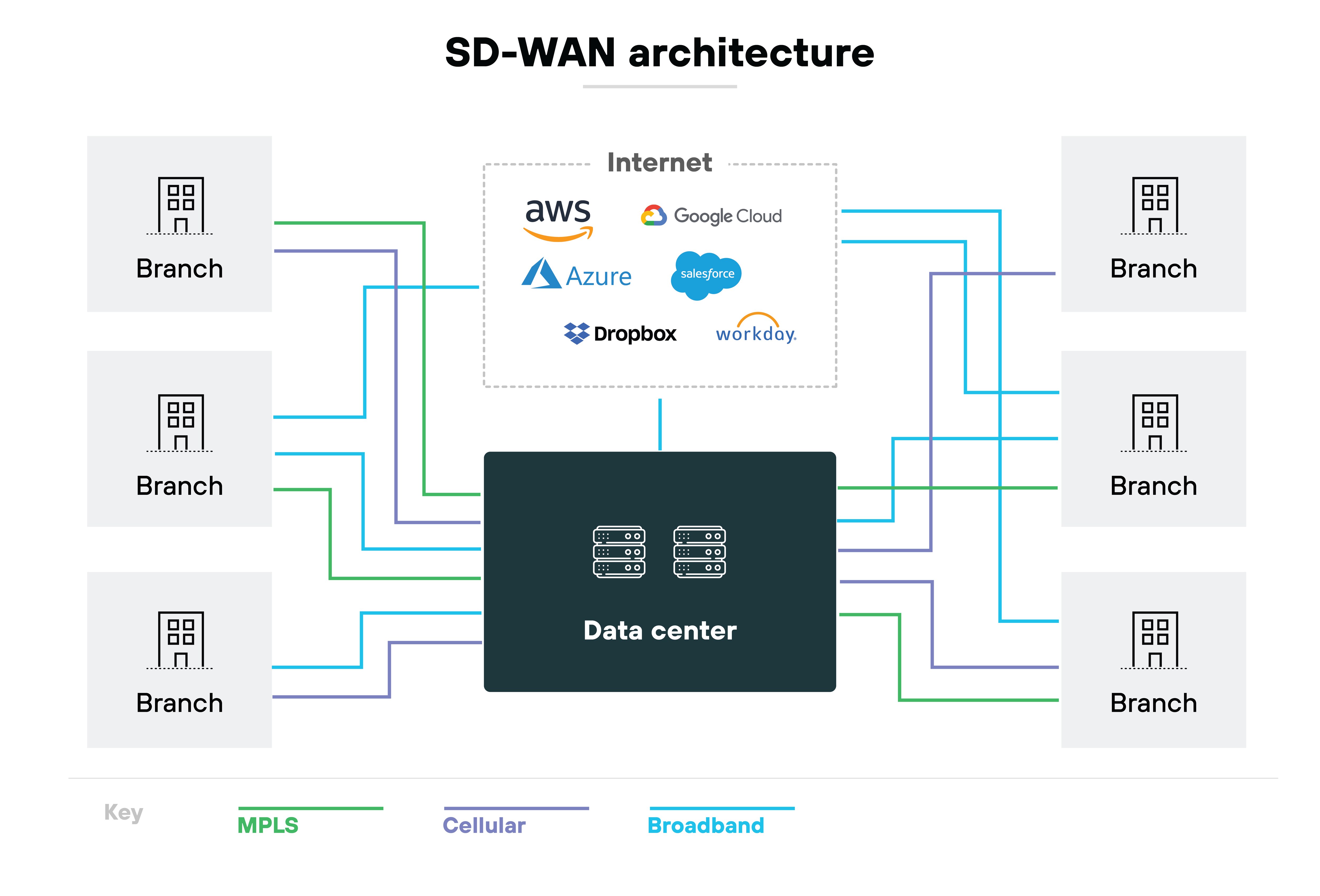
SD-Branch builds on that. It extends SD-WAN into the branch LAN, combining routing, switching, Wi-Fi, and security into one architecture. It's still on-premises. But it's centrally managed. And it's designed for branch locations that need hardware on-site.
SASE is different. It delivers those same network and security services from the cloud. Instead of managing local firewalls or Wi-Fi controllers, SASE centralizes policy in a unified cloud fabric. That's what allows it to support hybrid work, direct-to-app traffic, and zero trust at scale.
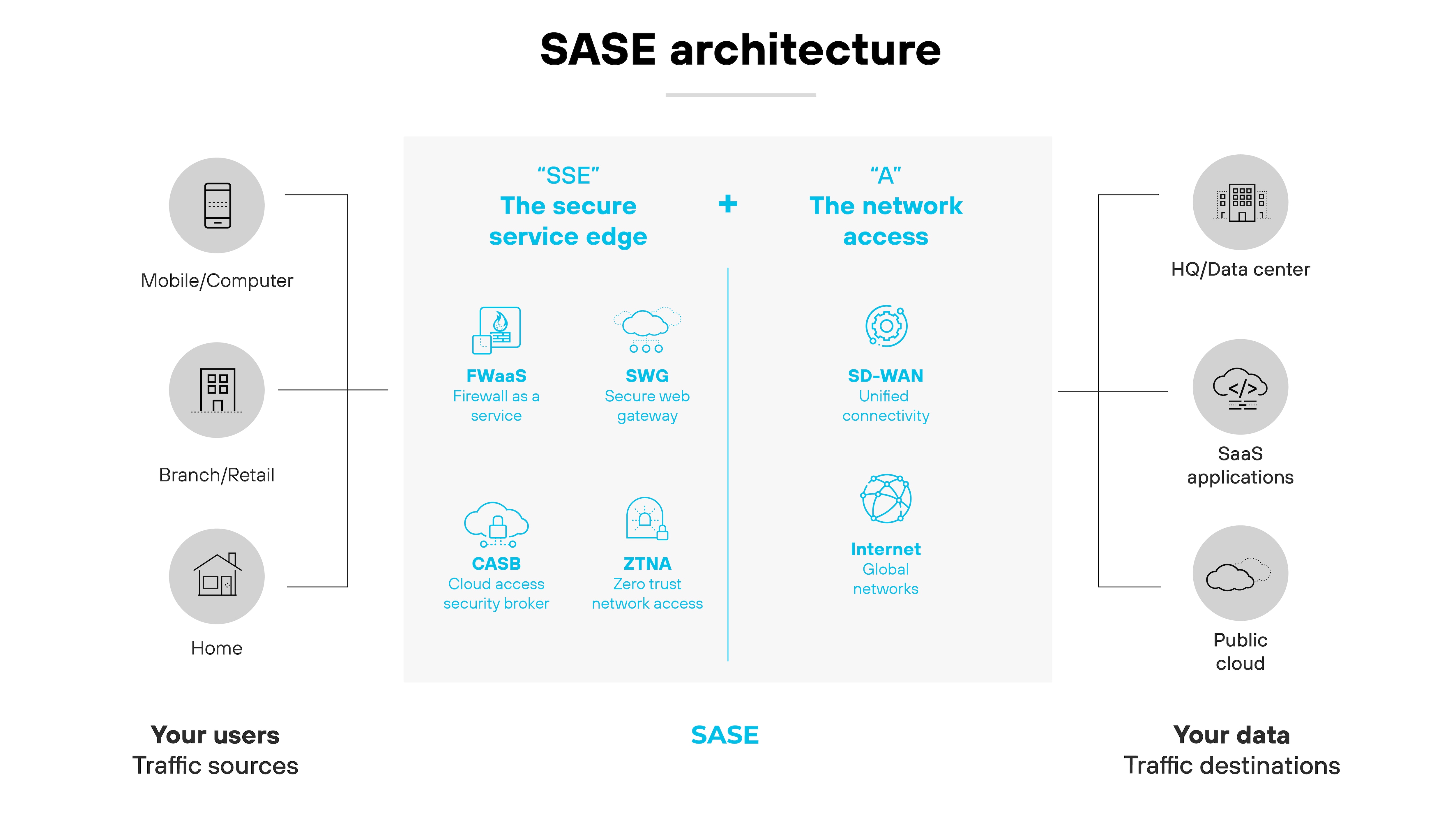
Essentially:
SD-WAN is a foundation. SD-Branch is a way to extend it across the branch. SASE is where things are going—especially as cloud-first becomes the norm.
Here are the practical differences:
| Comparison of SD-WAN, SD-Branch, and SASE |
|---|
| SD-WAN | SD-Branch | SASE | |
|---|---|---|---|
| Focus | WAN connectivity | LAN/WAN/security convergence | Cloud-delivered networking + security |
| Deployment | On-premises | On-premises | Cloud-based |
| Scope | Routing, traffic mgmt | LAN, Wi-Fi, routing, firewall | ZTNA, SWG, CASB, FWaaS, SD-WAN |
| Management | WAN-centric | Centralized, branch-focused | Unified cloud control plane |
Important:
These aren't mutually exclusive. Organizations often move from SD-WAN to SD-Branch and then evolve toward SASE.
- What Is SD-WAN Architecture? [Components, Types, Importance]
- Types of SD-WAN Deployment Models: A Complete Guide
- SD-WAN vs. SASE: Where One Ends and the Other Begins
What does a modern SD-Branch architecture include?
At its core, SD-Branch is a physical architecture. It replaces disconnected devices with a unified, centrally managed stack.
That stack usually starts with the SD-WAN appliance.
It connects the branch to cloud and data center resources. It also steers traffic based on application performance.
But SD-Branch goes further. It pulls in LAN and WLAN infrastructure.
Switches, access points, and PoE-connected devices all fall under the same control plane. Which includes IP phones, badge readers, cameras, and IoT endpoints.
That's because those are now attack surfaces. And legacy management tools can't isolate or secure them at scale.
That's where centralized orchestration comes in.
Modern SD-Branch designs use a single cloud-based console for configuration, policy, and device health. In some platforms, this includes API frameworks. These allow third-party services—like LTE failover or identity management—to plug into the branch stack without new hardware.
Zero-touch provisioning is also key.
It allows IT teams to drop-ship devices and have them automatically onboard into the correct security posture.
The result is an architecture that scales. And one that reflects how branches actually operate today: device-heavy, distributed, and resource-constrained.
Is SD-Branch still relevant today?
Yes. But mostly as a deployment pattern, not a category.
You'll still see “SD-Branch” used in vendor collateral. And some RFPs still call for it by name. But in practice, the term is fading. What's left behind is the architecture.
Basically, organizations still deploy SD-Branch. They just don't always call it that.
The approach remains useful for enterprises with physical branch locations. Especially those that need on-site gear, policy consistency, and unified management across LAN, WAN, and security.
It also still appears in product ecosystems. Some solutions support SD-Branch-like bundles that combine networking and security at the branch. Others enable the same model through centralized orchestration and zero-touch provisioning.
However:
The trend is moving toward cloud-delivered security and networking. SASE has absorbed much of what SD-Branch set out to do. It replaces on-site enforcement with cloud-native policy control.
That means SD-Branch is still relevant. Just less as a concept and more as a deployment footprint inside a broader transformation.
Should I still use SD-Branch or move to something else?
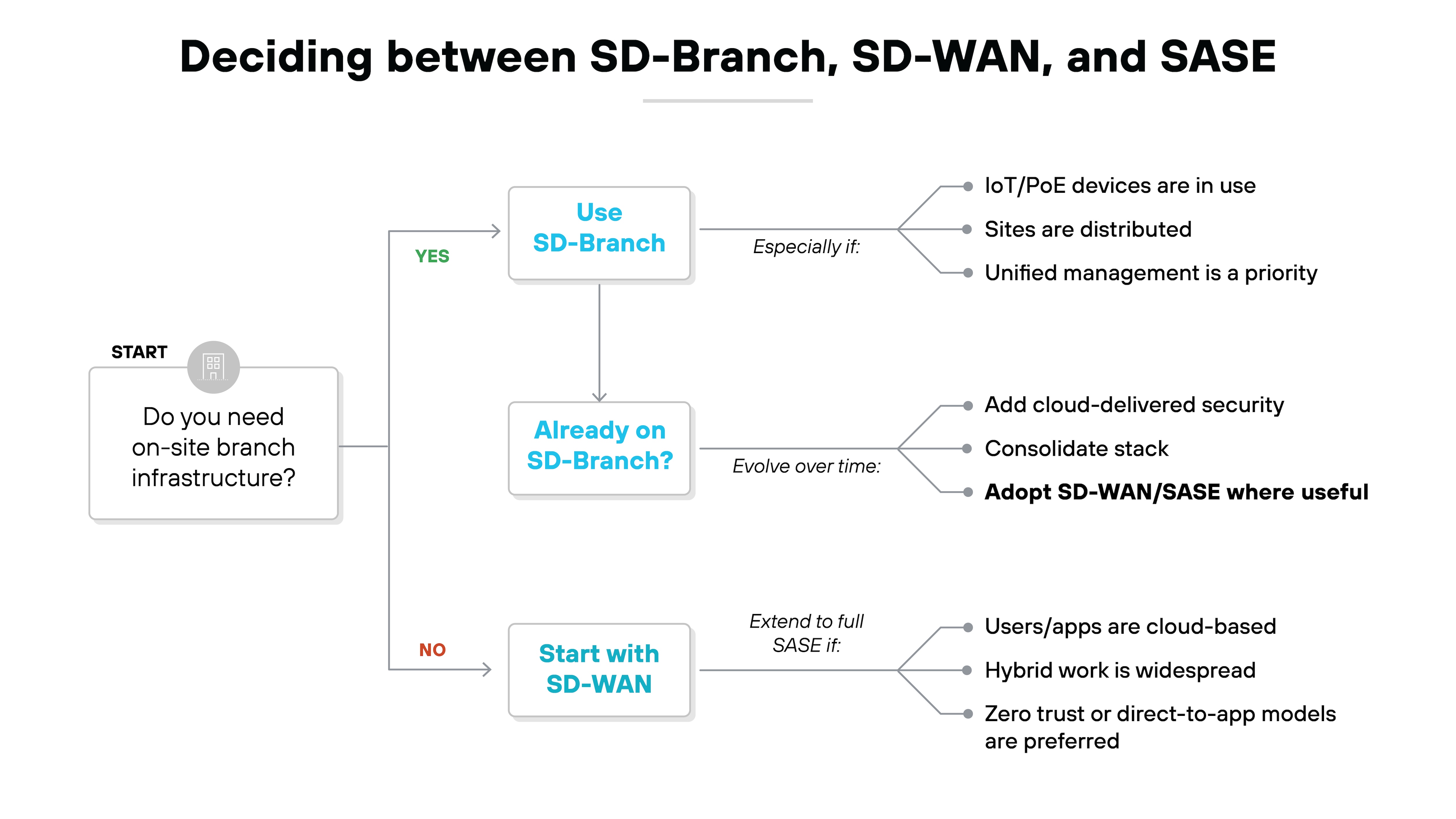
That depends on the environment.
SD-Branch still makes sense when physical infrastructure is non-negotiable.
For example: retail sites, healthcare clinics, or distributed operations with IoT-heavy footprints. If branches need local routing, Wi-Fi, segmentation, and enforcement—managed from a central platform—then SD-Branch is still a solid fit.
But not every organization needs on-prem hardware.
If the goal is to reduce branch infrastructure entirely, SD-Branch may be overkill. Especially if users and apps are already cloud-based.
In that case, it may make more sense to start with SD-WAN and extend into full SASE.
Here's why:
SASE moves most policy enforcement to the cloud. It protects branch users, mobile users, and remote sites without relying on multiple discrete security appliances at each branch. It also simplifies policy deployment and routing for hybrid workforces.
Important:
If SD-Branch is already in place, there's no need to rip and replace.
Many organizations evolve from it over time. That includes adopting cloud-delivered security, simplifying the branch stack, or consolidating around a unified management layer.
SD-WAN and SASE are the tools that enable that. They meet organizations where they are. And help take them where they're going.