- 1. Why is cryptographic agility critical for post-quantum migration?
- 2. How does cryptographic agility work in practice?
- 3. What are the key principles of crypto-agile design?
- 4. How do organizations measure crypto-agility maturity?
- 5. How does cryptographic agility support hybrid and quantum-safe systems?
- 6. What standards define cryptographic agility today?
- 7. How can enterprises start building crypto-agility now?
- 8. What's next for cryptographic agility?
- 9. Cryptographic agility FAQs
- Why is cryptographic agility critical for post-quantum migration?
- How does cryptographic agility work in practice?
- What are the key principles of crypto-agile design?
- How do organizations measure crypto-agility maturity?
- How does cryptographic agility support hybrid and quantum-safe systems?
- What standards define cryptographic agility today?
- How can enterprises start building crypto-agility now?
- What's next for cryptographic agility?
- Cryptographic agility FAQs
Cryptographic Agility: The Key to Quantum Readiness
- Why is cryptographic agility critical for post-quantum migration?
- How does cryptographic agility work in practice?
- What are the key principles of crypto-agile design?
- How do organizations measure crypto-agility maturity?
- How does cryptographic agility support hybrid and quantum-safe systems?
- What standards define cryptographic agility today?
- How can enterprises start building crypto-agility now?
- What's next for cryptographic agility?
- Cryptographic agility FAQs
Cryptographic agility is the capability of an information system to rapidly change or replace cryptographic algorithms, keys, and protocols without disrupting operations or security.
It enables systems to adapt to new cryptographic standards as threats evolve, including those introduced by quantum computing.
This adaptability is essential for quantum readiness because it allows organizations to transition to post-quantum cryptography before current encryption becomes vulnerable.
Why is cryptographic agility critical for post-quantum migration?
Quantum computing is changing what “secure” means. The math that underpins today's encryption won't hold once quantum algorithms mature. The risk isn't when that happens. It's how long current systems will take to adapt.
Here's why that's a problem:
Most cryptography is deeply embedded across networks, devices, and software stacks. Replacing it can take years. Which means migration to post-quantum cryptography will be a multi-decade effort that must start now, not when quantum computers arrive.
Cryptographic agility makes that possible.
It allows systems to replace algorithms, keys, and protocols without redesigning the underlying infrastructure. In other words, agility is what turns cryptography from a fixed feature into a flexible system property.
It also limits harvest-now-decrypt-later exposure.
By rotating or re-encrypting data with new algorithms before older ones break, organizations can prevent long-term data from becoming vulnerable. Which is essential to quantum security.
Without agility, even quantum-safe algorithms can't be deployed efficiently or at scale. Agility is what keeps encrypted ecosystems adaptable. So that when the cryptography changes, the systems built on it don't fall behind.
- What Is Post-Quantum Cryptography (PQC)? A Complete Guide
- 8 Quantum Computing Cybersecurity Risks [+ Protection Tips]
- Harvest Now, Decrypt Later (HNDL): The Quantum-Era Threat
How does cryptographic agility work in practice?
Cryptographic agility works by separating cryptography from the systems that use it.
In practice, that means encryption algorithms, keys, and protocols can change without touching the application code that relies on them.
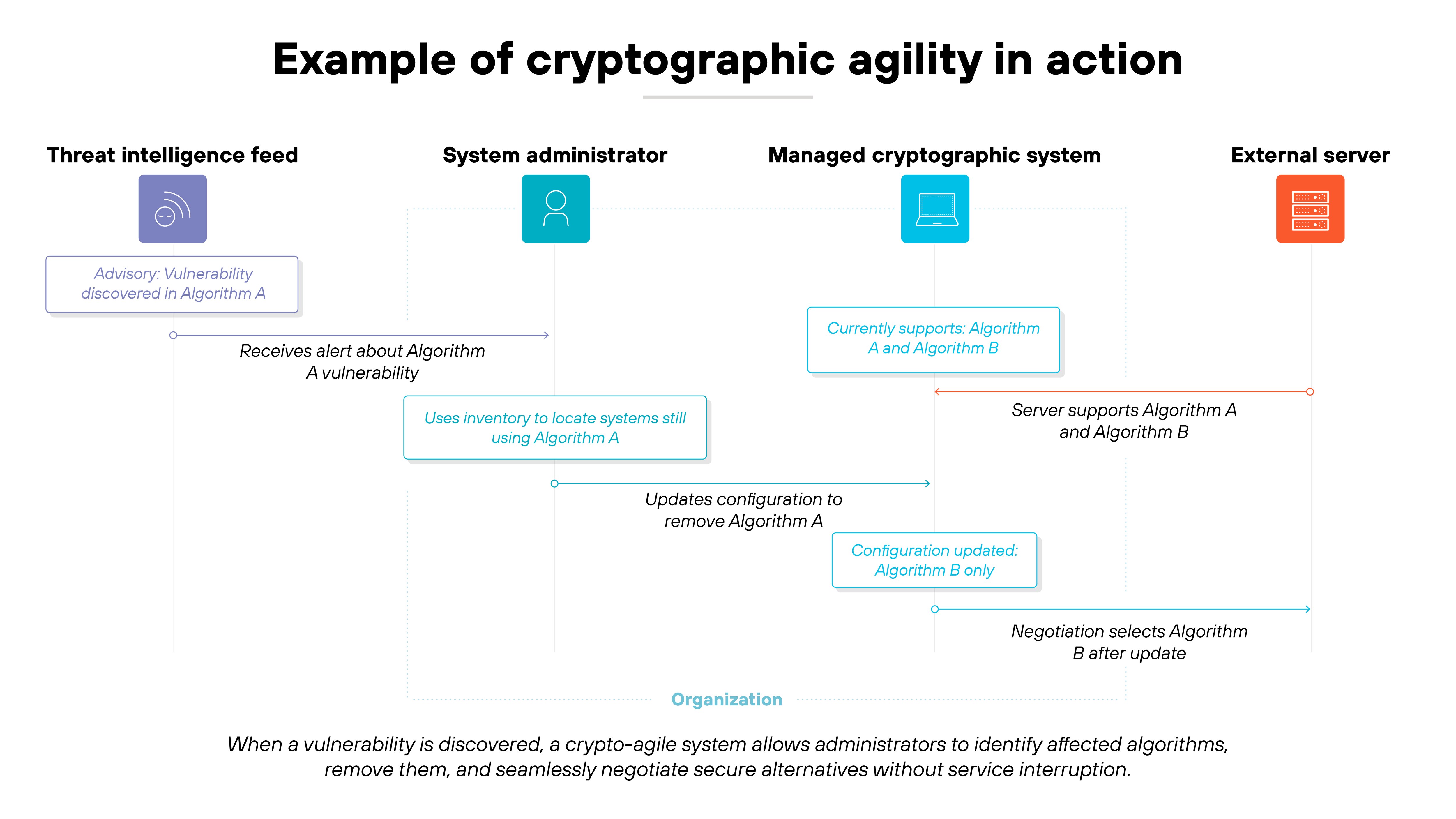
Here's how that happens:
-
Agile systems use modular crypto libraries.
Each algorithm is treated as a replaceable module instead of a hard-coded function. Which means updates can be made through configuration or policy rather than redesign.
-
Application interfaces are abstracted through APIs.
Those APIs define how data is encrypted, not which algorithm does it. So when new standards or post-quantum algorithms are introduced, the system can adopt them with minimal disruption.
-
At the protocol level, agility depends on negotiation.
Systems identify supported algorithms and select the strongest option both sides share. This process prevents downgrade attacks, where an attacker forces a weaker algorithm to gain access.
-
Key management is part of the same design.
Keys can be rotated, revoked, or reissued automatically across different cryptographic schemes.
The result is a security framework that can evolve alongside new cryptographic requirements without breaking trust or uptime.
What are the key principles of crypto-agile design?
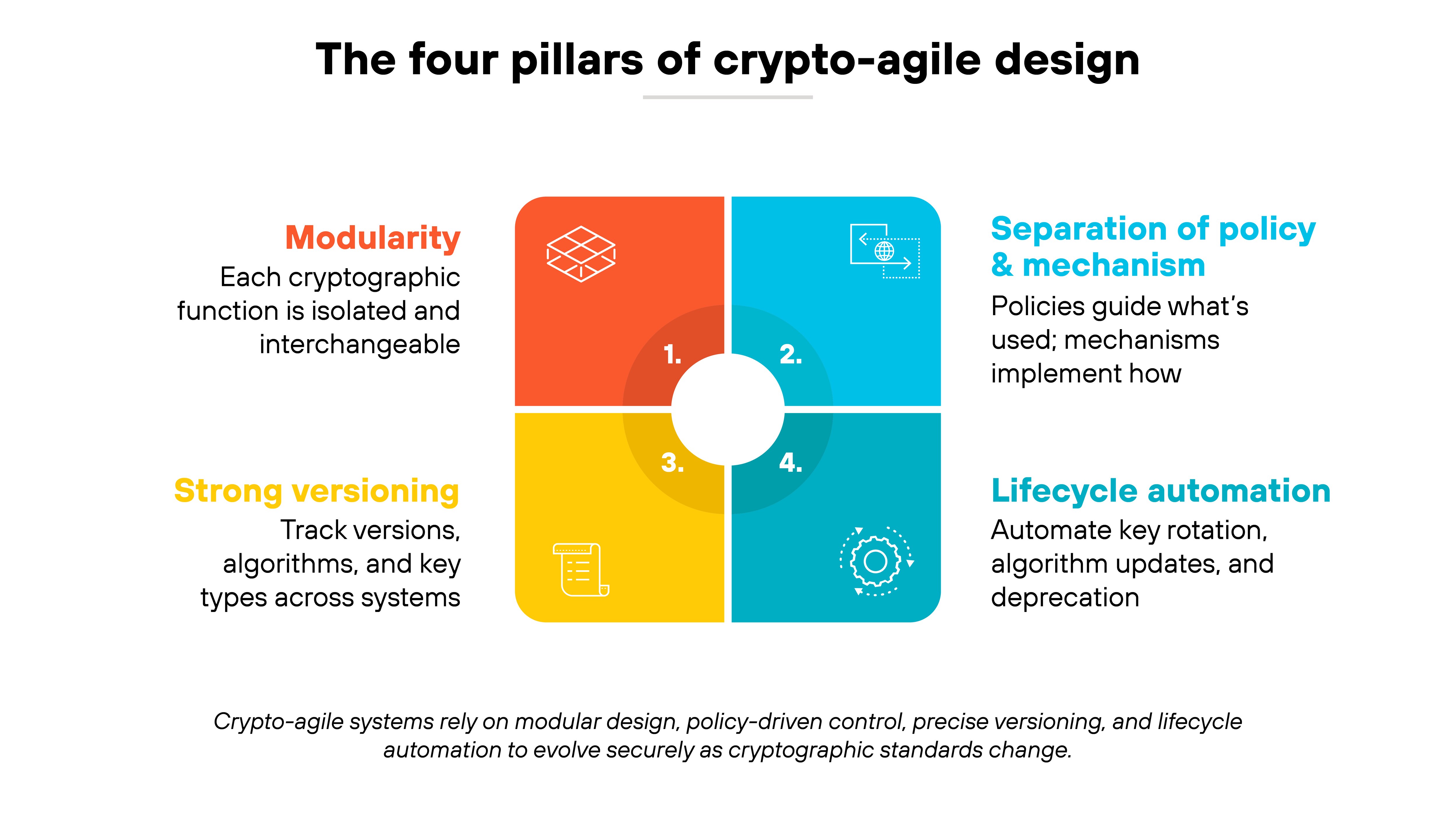
Cryptographic agility isn't a single feature. It's a design philosophy that makes encryption adaptable instead of static.
And building for agility means thinking ahead to how systems will change, not just how they run today.
Each crypto-agile system follows a few core principles that guide how algorithms are integrated, governed, and replaced. These principles create the structure that allows cryptography to evolve safely as new standards emerge.
Here's how that translates into practice:
Modularity
A crypto-agile system is built from interchangeable parts.
Each cryptographic function—like encryption, hashing, or key exchange—is isolated from the rest of the application. So new algorithms can be added or old ones removed without breaking functionality.
Modularity also makes testing and validation easier because each component can be updated independently.
Separation of policy and mechanism
Policy defines what the system should use. Mechanism defines how it's used.
Keeping them separate ensures that algorithm changes are driven by governance, not code rewrites. This principle makes it possible to apply organization-wide cryptographic standards consistently across different systems and vendors.
Strong versioning
Cryptographic components must track what version, algorithm, and key type they use. Why? Because clarity prevents accidental reuse or unsupported combinations. Versioning helps organizations know exactly what's deployed and where updates are needed.
It also supports backward compatibility during phased transitions.
Lifecycle automation
Agility depends on automation.
Key generation, rotation, and retirement must happen on schedule and at scale. Automated lifecycle management reduces the risk of outdated or weak algorithms staying in use.
It also provides the audit trail needed to verify compliance and maintain trust across changing cryptographic environments.
How do organizations measure crypto-agility maturity?
Measuring crypto-agility starts with understanding how flexible a system actually is.
It's not about whether algorithms can be replaced. It's about how quickly and safely those changes happen at scale.
To help organizations benchmark that capability, researchers at Hochschule Darmstadt developed the Crypto-Agility Maturity Model (CAMM). It defines five levels of maturity, from 0 to 4, each describing how well an organization can identify, manage, and update its cryptographic assets.
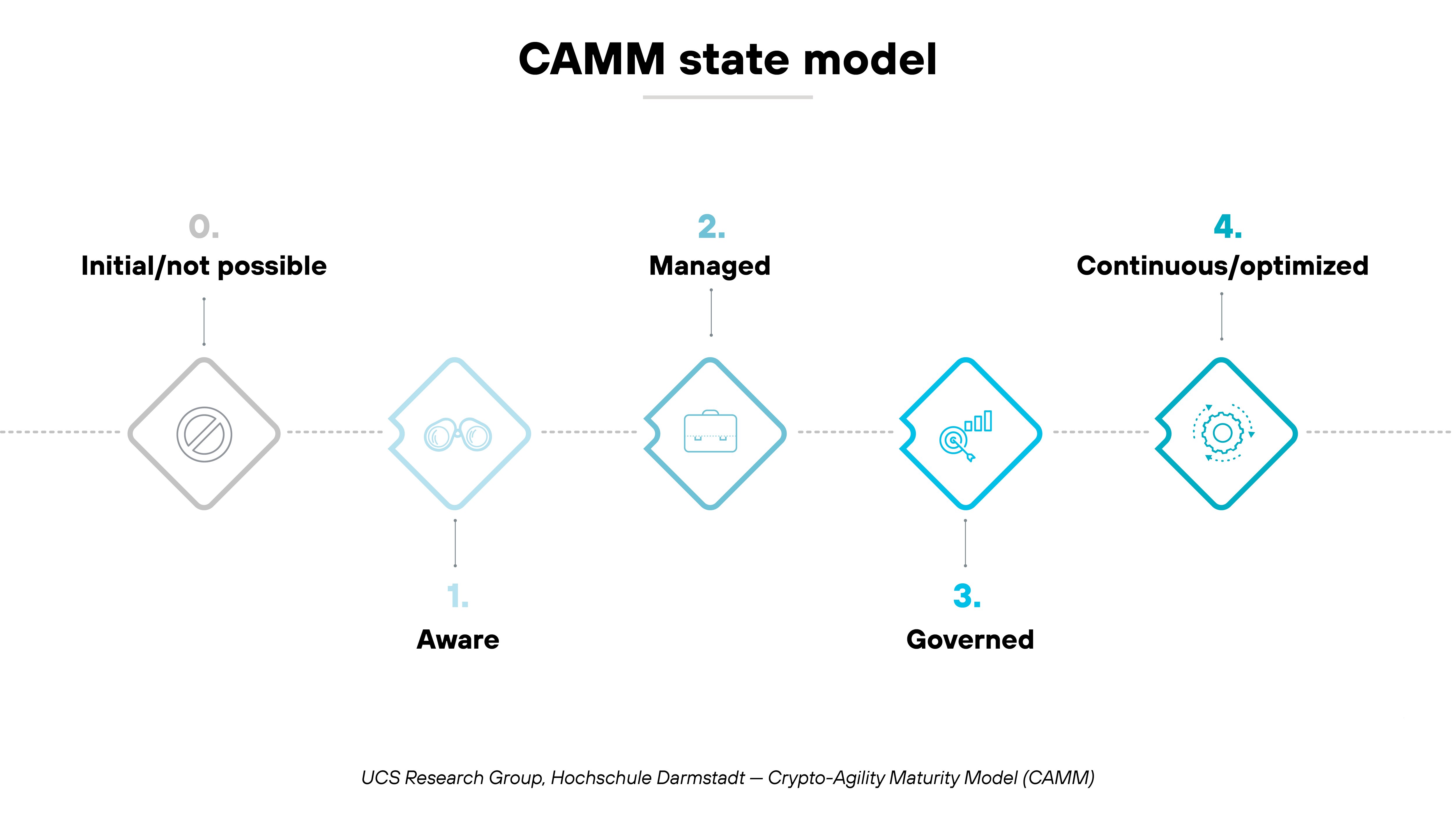
- At Level 0, cryptography is unmanaged. Algorithms and keys are hard-coded, and no central inventory exists.
- At Level 1, awareness begins. Teams start cataloging algorithms and dependencies but still change them manually.
- At Level 2, management processes emerge. Basic automation supports key rotation and algorithm updates.
- At Level 3, governance and tooling are standardized. Crypto changes follow formal policy with automated enforcement.
- At Level 4, agility is continuous. Cryptographic assets are fully inventoried, monitored, and automatically transitioned when standards evolve.
Why it matters:
Maturity determines how fast an organization can respond to new threats or standards without downtime or risk. It also ties into broader lifecycle management frameworks, where cryptographic health is treated as a measurable, improvable capability. Not a static control.
How does cryptographic agility support hybrid and quantum-safe systems?
Hybrid and quantum-safe systems are built to handle the transition between classical and post-quantum cryptography.
Hybrid models use both types of algorithms at once. So if one fails, the other keeps data secure. And quantum-safe systems take that further by ensuring every cryptographic process, from key exchange to signing, remains secure against quantum attacks.
Here's where agility fits in:
Cryptographic agility allows these systems to mix, match, and eventually replace algorithms without rebuilding the architecture.
It supports hybrid key-establishment methods that combine classical algorithms like RSA or ECC with post-quantum ones such as lattice-based schemes. The same goes for hybrid signatures, where two signature types are generated together for compatibility and assurance.
Agility also ensures coexistence during the long transition ahead.
It lets organizations update components independently, test new standards in parallel, and phase in post-quantum cryptography safely.
In essence, agility makes interoperability possible between old and new worlds of encryption. It bridges the gap until quantum-safe systems become the norm.
What standards define cryptographic agility today?
Cryptographic agility isn't defined by a single framework. It's shaped by a network of standards that describe how algorithms should be managed, tested, and transitioned across systems.
Together, these standards give organizations a roadmap for building crypto-agile infrastructure.
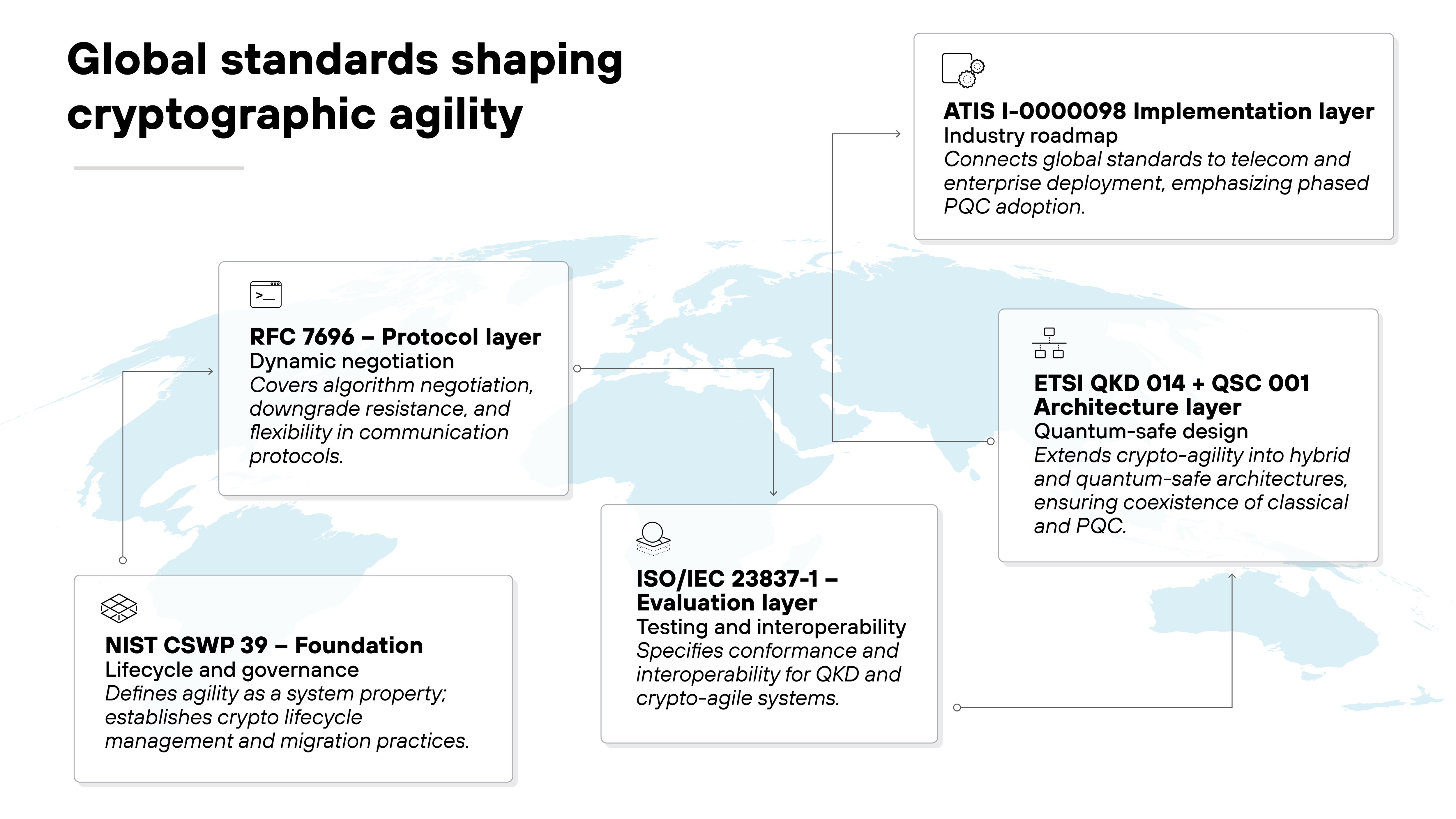
The foundation comes from NIST CSWP 39, which outlines best practices for cryptographic lifecycle management and agility planning. It defines agility as a property that allows systems to evolve securely as algorithms change.
RFC 7696 complements it at the protocol level. It describes how communication protocols can negotiate algorithms dynamically and resist downgrade attacks.
ISO/IEC 23837-1 adds an evaluation layer. It defines methods for testing and certifying interoperability between different QKD and crypto-agile systems.
ETSI QKD 014 and ETSI QSC 001 extend this work into quantum-safe architectures, specifying how classical and quantum technologies can coexist securely.
Finally, ATIS I-0000098 connects these global efforts to real-world deployment. It offers an industry roadmap for implementing quantum-resilient and crypto-agile networks.
Ultimately, the standards community is converging. NIST, ISO, ETSI, and ATIS are aligning their guidance so organizations worldwide can migrate toward post-quantum security in a coordinated, interoperable way.
How can enterprises start building crypto-agility now?
Cryptographic agility isn't something that can be added overnight. It has to be built deliberately across people, processes, and technology.
Most organizations already rely on dozens of cryptographic components scattered across systems and vendors. The goal now is to bring that landscape under control and make it adaptable before the post-quantum transition begins.
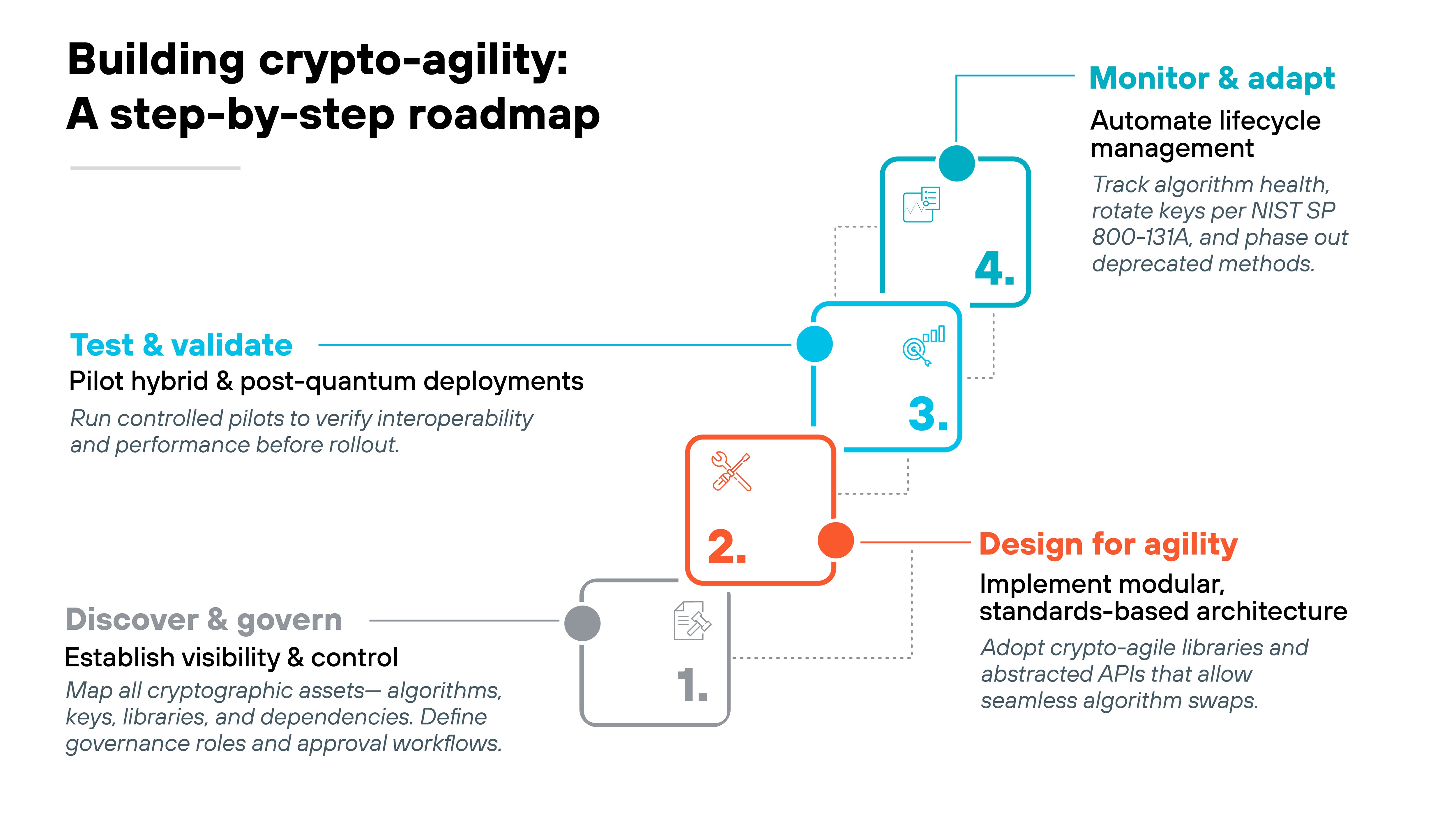
Here's how that process typically starts.
-
Building crypto-agility starts with visibility.
Organizations first need to understand where and how cryptography is used across their environment. That means creating an enterprise-wide inventory of algorithms, keys, libraries, and dependencies.
Governance frameworks should define ownership, review cycles, and approval processes for cryptographic changes.
-
Next comes implementation.
Agile cryptography depends on modular, standards-based libraries and APIs. Systems that abstract algorithm selection make it possible to switch to new methods—like post-quantum or hybrid schemes—without rewriting applications.
-
Then it's time to test.
Pilot environments allow teams to validate hybrid deployments that combine classical and post-quantum algorithms. These pilots help verify interoperability and performance before full production rollout.
-
Ongoing monitoring is the last piece.
Enterprises should track algorithm status and rotate keys according to NIST SP 800-131A guidance. That means retiring deprecated methods and re-encrypting sensitive data as standards evolve.
As demonstrated here, crypto-agility is built step by step.
Governance and visibility come first, followed by flexible design, controlled experimentation, and continuous algorithm management. Taken together, those actions lay the groundwork for a secure and quantum-ready future.
What's next for cryptographic agility?
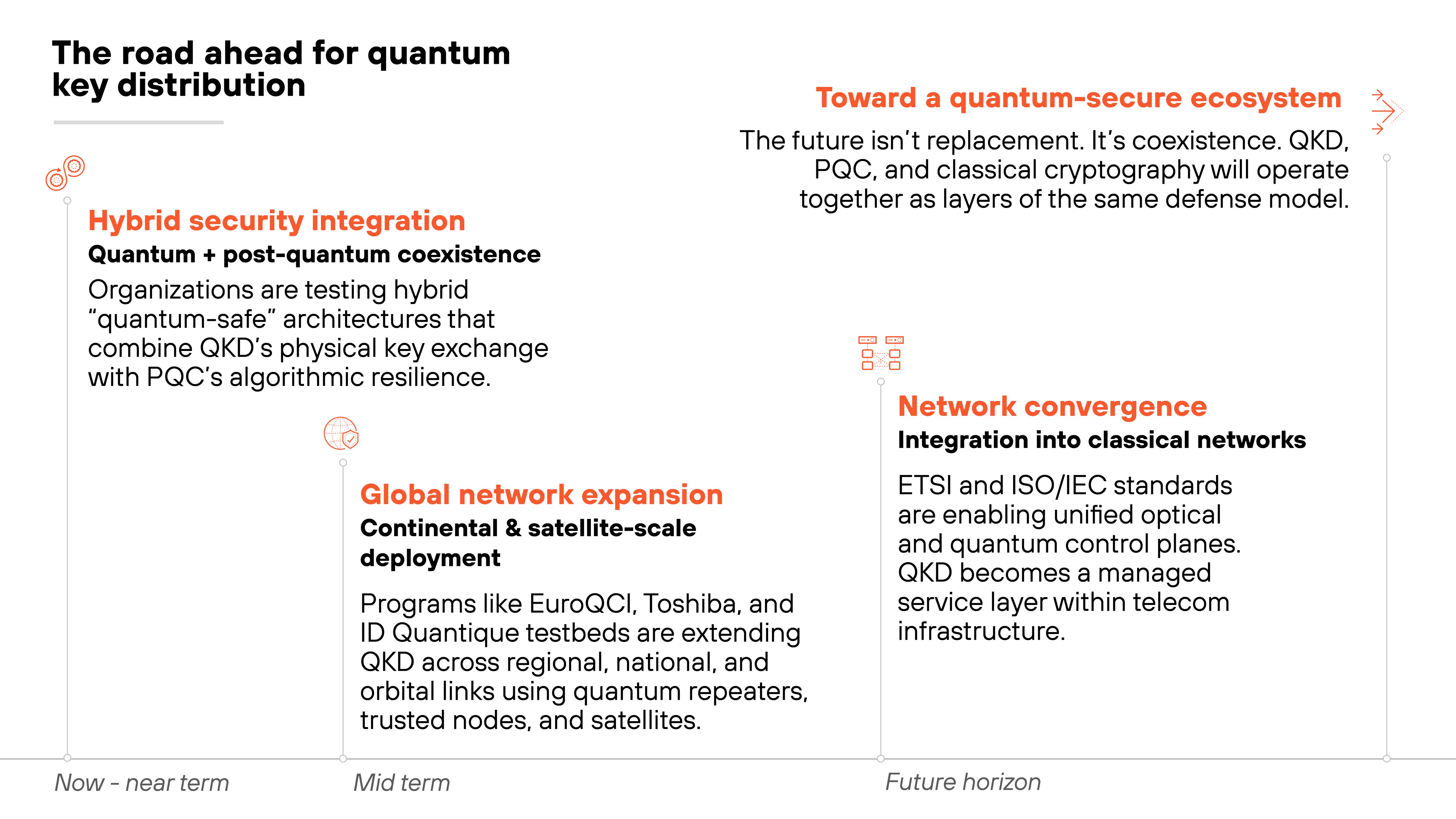
Cryptographic agility is moving from concept to standard practice.
The next phase is about system-level integration.
Where agility becomes built into platforms, protocols, and supply chains instead of added on later.
NIST's upcoming drafts will formalize this shift.
They focus on continuous cryptographic lifecycle management. Not just algorithm replacement. Which means systems will need to monitor, validate, and adapt automatically as standards evolve.
At the same time, post-quantum cryptography is nearing finalization.
Once those algorithms are standardized, agility will determine how smoothly they enter real-world products and infrastructure.
What it comes down to is this:
The future of cryptographic agility lies in convergence. Automation, governance, and interoperability are merging into one ecosystem. Where cryptography changes safely, predictably, and at scale.
As cryptographic standards evolve, agility will be the difference between organizations that adapt in time—and those that don't.