-
What is Security Misconfiguration?
- API8:2023 - Security Misconfiguration Explained
- Understanding Security Misconfiguration in API Security
- How Security Misconfiguration Manifests in Real-World APIs
- The Business Impact of Security Misconfiguration
- Identifying Security Misconfiguration in Your APIs
- Preventing Security Misconfiguration: Best Practices
- Security Misconfiguration FAQs
-
What Is Broken Object Level Authorization?
- API1:2023 - Broken Object Level Authorization Explained
- Understanding Object-Level Authorization in API Security
- How Broken Object Level Authorization Manifests in Real-World APIs
- The Business Impact of Broken Object Level Authorization
- Identifying Broken Object Level Authorization in Your APIs
- Preventing Broken Object Level Authorization: Best Practices
- Broken Object Level Authorization FAQs
- What Is API Security?
-
What Is Server Side Request Forgery?
- API7:2023 - Server Side Request Forgery Explained
- Understanding Server Side Request Forgery in API Security
- How Server Side Request Forgery Manifests in Real-World APIs
- The Business Impact of Server Side Request Forgery
- Identifying Server Side Request Forgery in Your APIs
- Preventing Server Side Request Forgery: Best Practices
- Server Side Request Forgery FAQs
-
What Is Unrestricted Resource Consumption?
- API4:2023 - Unrestricted Resource Consumption Explained
- Understanding Unrestricted Resource Consumption in API Security
- How Unrestricted Resource Consumption Manifests in Real-World APIs
- The Business Impact of Unrestricted Resource Consumption
- Identifying Unrestricted Resource Consumption in Your APIs
- Preventing Unrestricted Resource Consumption: Best Practices
- Unrestricted Resource Consumption FAQs
-
What Is Unrestricted Access to Sensitive Business Flows?
- API6:2023 - Unrestricted Access to Sensitive Business Flows Explained
- Understanding Unrestricted Access to Sensitive Business Flows in API Security
- How Unrestricted Access to Sensitive Business Flows Manifests in Real-World APIs
- The Business Impact of Unrestricted Access to Sensitive Business Flows
- Identifying Unrestricted Access to Sensitive Business Flows in Your APIs
- Preventing Unrestricted Access to Sensitive Business Flows: Best Practices
- Unrestricted Access to Sensitive Business Flows FAQs
-
What Is Broken Object Property Level Authorization?
- API3:2023 - Broken Object Property Level Authorization Explained
- Understanding Broken Object Property Level Authorization
- How Broken Object Property Level Authorization Manifests in Real-World APIs
- The Business Impact of Broken Object Property Level Authorization
- Identifying Broken Object Property Level Authorization in Your APIs
- Preventing Broken Object Property Level Authorization: Best Practices
- Broken Object Property Level Authorization FAQs
- API Security Checklist for Modern Application Teams
-
API Security Monitoring
- What to Monitor: Traffic, Sessions, Anomalies, Threats
- Services and Tools for Monitoring APIs
- Response Mechanisms: Threat Detection, Response, Remediation for APIs
- Ensuring the Best API Security Posture with Monitoring and Continuous Improvement
- Building a Monitoring-Driven API Security Lifecycle
- API Security Monitoring FAQs
- What Is API Endpoint Security
-
What Is Improper Inventory Management?
- API9:2023 - Improper Inventory Management Explained
- Understanding Improper Inventory Management in API Security
- How Improper Inventory Management Manifests in Real-World APIs
- The Business Impact of Improper Inventory Management
- Identifying Improper Inventory Management in Your APIs
- Preventing Improper Inventory Management: Best Practices
- Improper Inventory Management FAQs
-
Cloud API Security: Strategy for the DevOps Era
- The Role of API Keys and Secrets in Cloud APIs — Risks and Misuses
- The Gateway Layer in Cloud APIs: Why a Web API Security Gateway Is Critical
- Monitoring and Protecting APIs in Real Time in Cloud/DevOps Contexts
- Strategy Checklist: Best Practices for Cloud API Security in DevOps
- Conclusion: Bridging DevOps Velocity with Secure API Posture
- Cloud API Security FAQs
-
What Is Broken Authentication?
- API2:2023 - Broken Authentication Explained
- Understanding Broken Authentication in API Security
- How Broken Authentication Manifests in Real-World APIs
- The Business Impact of Broken Authentication
- Identifying Broken Authentication in Your APIs
- Preventing Broken Authentication: Best Practices
- Broken Authentication FAQs
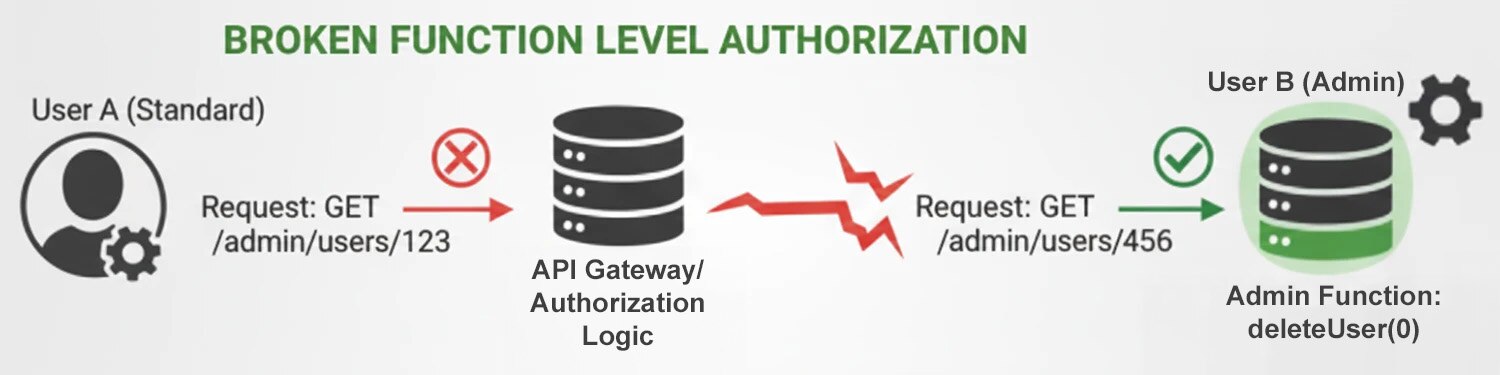
What Is Broken Function Level Authorization?
Broken function level authorization (BFLA), a critical OWASP Top 10 API risk, occurs when regular users gain access to administrative or restricted functions. In cloud environments, where privileged operations are distributed across numerous microservices, these authorization gaps allow attackers to escalate privileges, leak sensitive data, and bypass production system controls.
API5:2023 - Broken Function Level Authorization Explained
Function-level authorization failures allow users to execute privileged operations beyond their intended scope. Cloud APIs intensify this risk, as microservice architectures often fragment authorization logic across dozens of independent services. By systematically probing HTTP methods and endpoint paths, attackers can uncover administrative functions left exposed by inconsistent security policies. Also known as API5:2023 on OWASP’s top 10 list, BFLA elevates standard user access into a powerful admin tool and potentially the most direct route to total system compromise.
Controlling Endpoint Access
Function-level authorization determines which users can invoke specific API endpoints based on their assigned roles or privileges. A standard user accessing /api/users/{id} to view their own profile exercises proper authorization. An endpoint like /api/admin/users/delete requires elevated privileges that block regular account holders from execution.
The authorization layer sits between authentication and business logic. Authentication confirms identity. Authorization decides what that identity can do.
Function-Level Versus Object-Level Authorization
Function-level authorization governs access to entire endpoints or operations. Object-level authorization controls access to specific data instances. You're dealing with function-level issues when a regular user calls /api/admin/reports/generate and receives data. You're facing object-level problems when User A retrieves User B's records through /api/users/456/profile.
Function-level flaws expose operations. Object-level flaws expose data belonging to other entities. Both involve improper access, but they target different architectural layers.
Vertical Privilege Escalation
Security professionals call this vulnerability vertical access control failure or privilege escalation. Users move vertically up the permission hierarchy to claim administrator, moderator, or system-level capabilities. Unlike horizontal escalation, where user A accesses user B's equivalent-privilege resources, vertical movement grants powers exceeding the user's designated role.
API Complexity Factors
RESTful architectures expose operations through HTTP methods and URL patterns rather than form submissions or page loads. Developers scatter functionality across GET, POST, PUT, DELETE, and PATCH verbs, hitting hundreds of endpoints. Each verb-endpoint combination needs explicit authorization logic.
Traditional web applications centralize admin functions in dedicated interfaces protected by session checks. Modern cloud APIs distribute privileged operations across microservices where teams work independently. Authorization logic fragments. Gaps appear.
The URL Path Illusion
Teams assume /api/admins/ paths require admin rights, while /api/users/ paths stay public. The endpoint organization doesn't enforce security boundaries. Developers frequently place administrative functions under user-facing paths for architectural reasons. The route /api/users/export might dump the entire user database. Path structure offers zero security guarantees without enforcement code.
Understanding Broken Function Level Authorization in API Security
API functions represent discrete operations that manipulate system state or retrieve information. Authorization at the function level decides who executes those operations based on assigned privileges.
Defining Functions in API Architecture
Functions map to specific endpoint-method combinations. The endpoint /api/users paired with GET retrieves user lists. Paired with POST, the same endpoint creates new user accounts. Paired with DELETE, it removes accounts from the system.
Each HTTP verb exposes a distinct function requiring separate authorization logic. Developers building RESTful services often protect GET operations while leaving PUT, PATCH, or DELETE exposed. An attacker changes the verb from GET to DELETE and executes unauthorized deletions.
The path /api/reports/monthly might serve different functions depending on query parameters. Adding ?action=generate creates reports. Adding ?action=delete removes them. Query strings and request bodies introduce additional function variations that need protection.
Role Hierarchies and Group-Based Access
Organizations structure permissions through hierarchical roles. Administrators possess system-wide privileges. Department managers access resources within their organizational units. Standard users operate with limited read-write capabilities scoped to their own data.
Group-based access control assigns users to collections like billing, support, or engineering. Members inherit the group's permission set. A billing API endpoint processing refunds should execute only for users in the billing group, regardless of their role level.
Cloud environments complicate role management. Service accounts, API keys, machine identities, and federated users all need function-level restrictions. A Lambda function invoking internal APIs requires different permissions than a mobile app client accessing the same backend.
Entry Points and Method-Based Exposure
Every exposed endpoint presents an attack surface. APIs publish hundreds or thousands of routes across multiple services. Each route accepts multiple HTTP methods. Teams struggle to audit whether every endpoint-method pair enforces appropriate authorization.
Developers place administrative functions alongside user-facing operations for architectural convenience. The route /api/accounts/bulk-update sits next to /api/accounts/profile because both manipulate account data. One requires admin privileges, the other doesn't. Code reviewers miss the distinction.
Deny by Default Architecture
Secure systems block all access unless code explicitly grants permission. “Deny by default” means new endpoints start locked. Developers must write authorization rules that open specific functions to specific roles.
Permit by default architectures allow access unless code explicitly blocks it. Adding a new endpoint automatically inherits permissive access. Developers forget to add restrictions. Privilege escalation vulnerabilities appear.
Function Layer Versus Data Layer Authorization
Function-level checks occur before business logic executes. The system asks, Can this role invoke this operation? Data-level checks occur during business logic execution. The system asks, Does this user own this specific resource?
An API enforcing function-level authorization on /api/documents/delete verifies admin privileges before executing any deletion logic. An API enforcing data-level authorization allows the delete function to run but restricts which document IDs the user can target. Both layers need protection.
How Broken Function Level Authorization Manifests in Real-World APIs
Authorization failures emerge when endpoints execute privileged operations without verifying the caller's role. Attackers exploit predictable API patterns to discover and invoke functions beyond their permission scope.
Regular Users Invoking Administrative Endpoints
Administrative operations frequently live at predictable paths. Teams deploy user management functions to /api/admin/users/export or /api/v1/system/settings/update. Attackers enumerate these paths using wordlists containing common administrative terms like "admin," "manage," "settings," "export," and "bulk."
Mobile applications and single-page web apps leak endpoint structures through bundled JavaScript. Decompiling an APK file or reading minified frontend code reveals the complete API surface, including administrative routes that the UI hides from regular users. An attacker extracts the path /api/admin/reports/financial from the mobile app's source code and requests it directly with their standard user token.
HTTP Method Manipulation
REST conventions map CRUD operations to HTTP verbs. GET retrieves, POST creates, PUT replaces, PATCH modifies, DELETE removes. Developers protect read operations with authentication but forget to restrict write operations at the same endpoint.
An authenticated user queries GET /api/subscriptions/premium and receives subscription details. Changing the method to DELETE /api/subscriptions/premium while keeping the same authorization token successfully cancels the premium tier. The endpoint verified identity but ignored role requirements for destructive operations.
OPTIONS requests expose supported methods for each endpoint. Sending OPTIONS /api/users/profile returns "Allow: GET, PUT, DELETE, PATCH" in response headers. Attackers know which verbs to test for authorization gaps.
Cross-Group Function Access
Multitenant platforms segregate users into organizational groups, departments, or teams. The billing group accesses /api/billing/invoices while the support group accesses /api/support/tickets. Authorization logic should restrict billing endpoints to billing group members.
Weak implementations verify group membership for the default UI workflow but skip checks when users directly request cross-group endpoints. A support representative discovers /api/billing/refunds/process through API documentation and successfully processes refunds despite belonging to the wrong functional group.
Endpoint Discovery Through Pattern Recognition
API versioning and resource naming follow predictable conventions. Finding /api/v1/users/profile suggests /api/v1/users/list exists. Discovering /api/reports/monthly implies /api/reports/yearly might work. Teams expose /api/products/export for product managers but fail to protect the parallel /api/customers/export endpoint with equivalent authorization.
Attackers iterate through resource names, HTTP verbs, and common action suffixes. They test /api/users/delete, /api/accounts/disable, /api/settings/reset, and /api/data/export against their low-privilege tokens. Automated scanners generate thousands of variations within minutes.
Mixed Administrative and User Functions
Microservices consolidate related operations in a single service boundary. The user service handles profile updates, password resets, role assignments, and account deletions. Developers protect role assignments with admin checks but forget to apply the same rigor to bulk operations at /api/users/bulk-delete. Path proximity creates a false sense of consistent protection.
The Business Impact of Broken Function Level Authorization
Function-level authorization failures grant attackers administrative control over cloud infrastructure, customer data, and critical business operations. The vulnerability transforms authenticated low-privilege users into system administrators.
Complete System Compromise
Admin-level access lets attackers reconfigure authentication systems, modify authorization rules, and create backdoor accounts. An attacker gaining administrative endpoint access can promote their own account to superuser status, disable security logging, and establish persistent access mechanisms that survive password resets and security audits.
Cloud environments amplify the damage. Administrative APIs control infrastructure provisioning, network configurations, and cross-service permissions. Compromising AWS, Azure, or GCP management APIs through broken function authorization grants control over compute resources, storage buckets, databases, and serverless functions across the environment.
Data Exposure and Exfiltration
Administrative functions frequently include bulk export capabilities designed for legitimate backup and migration workflows. Endpoints like /api/users/export, /api/transactions/download, or /api/customers/report return complete datasets in single requests. Attackers invoke these functions for data exfiltration, often successfully extracting millions of customer records, financial transactions, or proprietary business data within seconds.
Multitenant platforms suffer cascading exposure. Breaching one tenant's administrative functions can reveal data from other tenants if the authorization layer fails to properly scope administrative access to organizational boundaries.
Operational Destruction
Write operations under administrative paths modify or delete production data at scale. Bulk deletion endpoints remove customer accounts, transaction histories, or critical configurations. Update operations, change pricing structures, disable security features, or modify access control policies.
Infrastructure management APIs offer destructive capabilities. Unauthorized calls to /api/infrastructure/terminate or /api/databases/drop destroy live production systems. Recovery requires restoring from backups, assuming backup systems remain uncompromised.
Compliance and Regulatory Failures
SOC 2 Type II audits mandate role-based access controls with documented enforcement mechanisms. Function-level authorization gaps fail control objectives around logical access and change management. ISO 27001 certification requires demonstrable access restriction based on business need and role assignment. GDPR mandates access controls protecting personal data from unauthorized processing.
Audit findings trigger remediation requirements, delayed certifications, and customer contract violations. Enterprise customers demand evidence of access control maturity before signing agreements or renewing contracts.
Identifying Broken Function Level Authorization in Your APIs
Security teams discover function-level authorization gaps through systematic testing that maps every endpoint-method-role combination. Manual exploration combined with automated scanning reveals unprotected privileged operations.
Manual Endpoint Enumeration
Start with comprehensive API documentation. OpenAPI specifications, Swagger files, and internal wikis list exposed endpoints, supported HTTP methods, and expected parameters. Teams often document administrative endpoints alongside public routes, revealing the complete attack surface.
Test each endpoint with multiple HTTP verbs regardless of documented support. Send GET, POST, PUT, PATCH, DELETE, and OPTIONS requests to every discovered path. An endpoint documented as GET-only might accept DELETE requests that skip authorization checks. Record which verbs return successful responses versus 405 Method Not Allowed errors.
Create test accounts representing every role in your system. You need standard users, premium users, group members, department managers, and administrators. Log authentication tokens for each role. Execute identical API requests using different role tokens to identify privilege boundaries.
Cross-Role Authorization Testing
Build a matrix-mapping roles to endpoints. Rows represent user types. Columns represent API paths. Fill each cell by attempting the request with that role's credentials. Mark cells green for authorized access, red for properly blocked access, and yellow for unexpected authorization grants.
A complete matrix reveals authorization gaps immediately. If the "standard user" row shows green cells for /api/admin/users/export or /api/billing/refunds/process, you've found a broken function authorization. Yellow cells indicate authorization logic exists but behaves unexpectedly for specific role combinations.
Automated Discovery and Scanning
Feed your API specification into authorization testing frameworks like OWASP ZAP, Burp Suite Enterprise, or specialized API security platforms, including CNAPP. Configure the scanner with multiple authentication contexts representing different user roles. The tool systematically requests that every endpoint-method pair with each credential set, flagging authorization mismatches.
Generate wordlists from common administrative terms. Tools like ffuf, Gobuster, or custom scripts iterate through variations of /api/admin, /api/manage, /api/internal, /api/system, combined with resource names and action verbs. Append discovered endpoints to your testing matrix.
Parse client-side applications for undocumented endpoints. Mobile app binaries, JavaScript bundles, and configuration files leak API routes that documentation omits. Attackers use the same discovery techniques, so security teams must test these hidden paths.
Critical Testing Questions
Verification requires answering specific authorization questions for every endpoint.
- Can authenticated users with standard roles invoke this function?
- What happens when you change GET to DELETE at /api/resources/{id}?
- Do group membership checks prevent cross-group access to /api/billing/invoices from support team credentials?
Test whether new endpoints inherit permissive defaults or require explicit authorization configuration. Deploy a test endpoint without authorization decorators and attempt access with low-privilege tokens. If the request succeeds, your framework permits it by default.
Preventing Broken Function Level Authorization: Best Practices
Secure APIs enforce authorization through centralized, deny-by-default mechanisms that explicitly grant function access based on verified roles. Prevention requires architectural decisions, consistent code patterns, and ongoing validation.
Centralized Authorization Enforcement
Build a single authorization module that every endpoint invokes before executing business logic. Middleware frameworks like Express.js, Spring Security, or ASP.NET Core authorization filters provide injection points that intercept requests before they reach controller code. Configure these components to evaluate role requirements against authenticated user claims.
Deny all access by default. New endpoints start locked until developers explicitly declare which roles can invoke them. Framework configurations should require authorization annotations on every public method. Missing annotations trigger build failures or runtime exceptions in development environments.
Create reusable authorization components that accept role requirements as parameters. Rather than writing custom authorization logic in each endpoint, call a shared function that evaluates whether the current user's roles satisfy the declared requirements. Centralized code undergoes review once and applies consistently across hundreds of endpoints.
Architectural Patterns for Admin Functions
Segregate administrative operations into dedicated controllers that inherit from an AdminBaseController abstract class. The base class constructor or initialization method verifies admin role membership before allowing any child method execution. Developers adding new admin endpoints inherit authorization automatically by extending the protected base class.
Implement attribute-based access control at the controller and method level. Decorators like @RequiresRole("admin") or [Authorize(Roles = "Administrator")] in C# declare authorization requirements directly in code adjacent to the protected function. Code reviewers see authorization requirements without hunting through configuration files.
Platform teams should provide template repositories with preconfigured authorization middleware and base controllers. New services clone the template and inherit secure-by-default patterns. Custom authorization logic gets reviewed as an exception requiring security team approval.
Method and Endpoint Verification
Write authorization checks that evaluate both the HTTP verb and the resource path. An endpoint allowing GET /api/reports for standard users requires separate authorization logic for DELETE /api/reports. Routing frameworks that map multiple verbs to the same handler function need explicit authorization checks for each supported verb.
Place authorization validation inside business logic methods, not just at controller boundaries. A shared service method like UserService.deleteUser should verify caller permissions even when invoked from internal code paths. Defense in depth prevents authorization bypass through alternative invocation routes.
Avoid authorization decisions based on URL patterns. Code checking whether the path contains "/admin/" creates false security boundaries. Attackers request administrative functions deployed under non-admin paths. Role-based authorization logic should evaluate user claims against required permissions without parsing URLs.
Continuous Authorization Audits
Maintain an authorization matrix mapping every endpoint-method combination to required roles. API gateway configurations, OpenAPI specifications with security schemes, or dedicated authorization documentation should serve as the source of truth. Compare the actual endpoint auth code against the documented requirements during each deployment.
Automated tests should execute every endpoint with multiple role contexts and assert expected authorization outcomes. Integration test suites authenticate as different user types and verify that admin endpoints reject standard user tokens while user endpoints permit appropriate access.
Review authorization implementations when business requirements change. New user roles, organizational restructuring, or feature releases alter which users should access which functions. Schedule quarterly authorization audits that reconcile code-level permissions with current business policies.