-
What Is MITRE ATT&CK Framework?
- MITRE ATT&CK Framework Explained
- Structuring Adversary Behavior by Tactic
- MITRE ATT&CK Tactics and Their Role in Security Intelligence
- MITRE ATT&CK Techniques
- MITRE ATT&CK Use Cases
- Using the MITRE ATT&CK Framework during a Live Attack
- Comparing MITRE ATT&CK and the Cyber Kill Chain
- Advancing Organizational Maturity with ATT&CK
- Toward a Behavioral Framework for Securing AI
- MITRE ATT&CK Framework FAQs
- How Do I Implement MITRE ATT&CK Techniques?
-
What is the MITRE ATT&CK Matrix?
- MITRE ATT&CK Matrix Explained
- Key Components of MITRE ATT&CK: Tactics, Techniques, and Procedures
- Diverse MITRE ATT&CK Matrices: Adapting to Specific Environments
- How Organizations Operationalize MITRE ATT&CK
- Implementing and Maintaining a MITRE ATT&CK Program
- Benefits of Leveraging the MITRE ATT&CK Framework
- Common Challenges and Solutions
- MITRE ATT&CK and the Cybersecurity Landscape
- MITRE ATT&CK Matrix FAQs
-
How Has MITRE ATT&CK Evolved?
- Evolution of MITRE ATT&CK Explained
- The Historical Trajectory of MITRE ATT&CK
- Why TTPs Matter: Shifting the Cybersecurity Paradigm
- Key Milestones in ATT&CK's Expansion and Refinement
- Core Components and Their Evolving Definition
- Why the Evolution Matters: Benefits for Cybersecurity Professionals
- Addressing the Evolving Threat Landscape with ATT&CK
- Operationalizing the Framework: Practical Applications and Challenges
- The Future of MITRE ATT&CK
- Evolution of MITRE ATT&CK FAQs
- What Are MITRE ATT&CK Use Cases?
- A CISO's Guide to MITRE ATT&CK
- How Does MITRE ATT&CK Apply to Different Technologies?
-
What is the Difference Between MITRE ATT&CK Sub-Techniques and Procedures?
- Understanding the MITRE ATT&CK Framework
- Exploring Sub-Techniques in the ATT&CK Framework
- Exploring Procedures in the ATT&CK Framework
- The Role of Sub-Techniques in Cybersecurity Strategies
- Procedures as a Tool for Detailed Threat Analysis
- Continuous Evolution: Staying Updated with ATT&CK Framework
- MITRE ATT&CK Sub-Techniques vs. Procedures FAQs
What Are MITRE ATT&CK Techniques?
Gain Unmatched Visibility. Protect Critical Services. Stay Compliant, Simply.
The Network and Information Security 2 Directive (NIS2) is a major EU directive that has introduced increased cybersecurity requirements and mandated security posture reporting to more organizations compared to its predecessor, NIS. This strengthened cybersecurity framework is designed to significantly enhance the overall resilience of essential and digital service providers across the European Union and, like GDPR, carries worldwide implications for organizations that operate within or engage with entities within the EU. With stricter obligations, a broader scope, and tougher penalties, organizations have had to ensure compliance since October 17, 2024.
Palo Alto Networks offers industry-leading security solutions that directly support your NIS2 compliance journey, helping you navigate these complex requirements with confidence and making the path to compliance simpler.
Why NIS2 Matters for Your Organization
NIS2 replaces the original NIS Directive, evolving to address the escalating sophistication of cyber threats and expanding its reach. It applies to a wider range of critical sectors, including energy, healthcare, finance, digital infrastructure, public administration, and many more.
The NIS2 Directive aims to:
- Manage security risk
- Protect against cyber attacks
- Detect cybersecurity incidents
- Minimize the impact of cybersecurity incidents
NIS2 introduces significant changes that demand your attention:
- Broader Sector Coverage: More types of organizations in critical sectors are now explicitly covered.
- Stricter Obligations: Requires organizations to implement stronger, more detailed technical and organizational security measures.
- Tougher Penalties: Non-compliance can result in substantial fines (up to €10 million or 2% of global turnover for essential entities).
- Management Accountability: Senior management can be held liable for compliance failures, underscoring the importance of robust cybersecurity.
Which organizations will NIS2 affect? Your organization is likely to be impacted if it:
- Is based in or operates in an EU member state or supplies into organizations based in the EU.
- Is not a micro-enterprise (i.e., >50 employees, annual turnover >€10 million, or annual balance sheet >€10 million).
- Is a micro-enterprise, but provides a vital service.
Organizations will need to be able to demonstrate that they have a roadmap for compliance and are implementing appropriate measures, or they will face significant fines and direct penalties for the C-Suite. We recommend working with legal counsel and security teams as soon as possible to determine if you are covered and begin developing a compliance strategy.
What NIS2 Requires: Key Objectives and Priorities
To manage cyber risks effectively and comply with NIS2, organizations must implement appropriate technical, operational, and organizational measures. Key areas of focus include:
- Risk Management: Organizations need to implement comprehensive measures to reduce cyber threats. These measures include securing their supply chains, improving network and access security, and implementing encryption.
- Cyber Hygiene & Training: Implementing basic security practices like Zero Trust, strong access control (including Multi-Factor Authentication), and fostering continuous staff awareness and training.
- Corporate Accountability: The NIS2 directive requires organizational leaders to monitor and endorse cybersecurity efforts and address cyber risk, ensuring accountability at the highest levels.
- Reporting Obligations: NIS2 contains specific obligations and expectations for reporting significant security incidents, including an initial notification within less than 24 hours.
- Business Continuity: Organizations should have a continuity plan for major cyber events covering system recovery, emergency protocols, and establishing a crisis response team.
What Articles of NIS2 Compliance Does Palo Alto Networks Help with
To ensure adequate coverage of your NIS2 implementation, Palo Alto Networks provides the most comprehensive coverage of the main articles that help to prove the cybersecurity posture and resilience of your business. Key Articles include:
Key Points
-
Granular Detail:
Techniques specify the "how" of an adversary's actions, providing precise behavioral descriptions. -
Standardized Catalog:
Each technique has a unique ID and detailed description, offering a common language for cybersecurity professionals. -
Real-World Basis:
Techniques are derived from observed adversary behaviors, ensuring their practical relevance to current threats. -
Foundation for Defense:
Understanding techniques is crucial for developing targeted detection rules, mitigation strategies, and validating security controls. -
Evolving Knowledge:
The knowledge base of techniques is continuously updated to reflect new adversary methods and evolving attack landscapes.
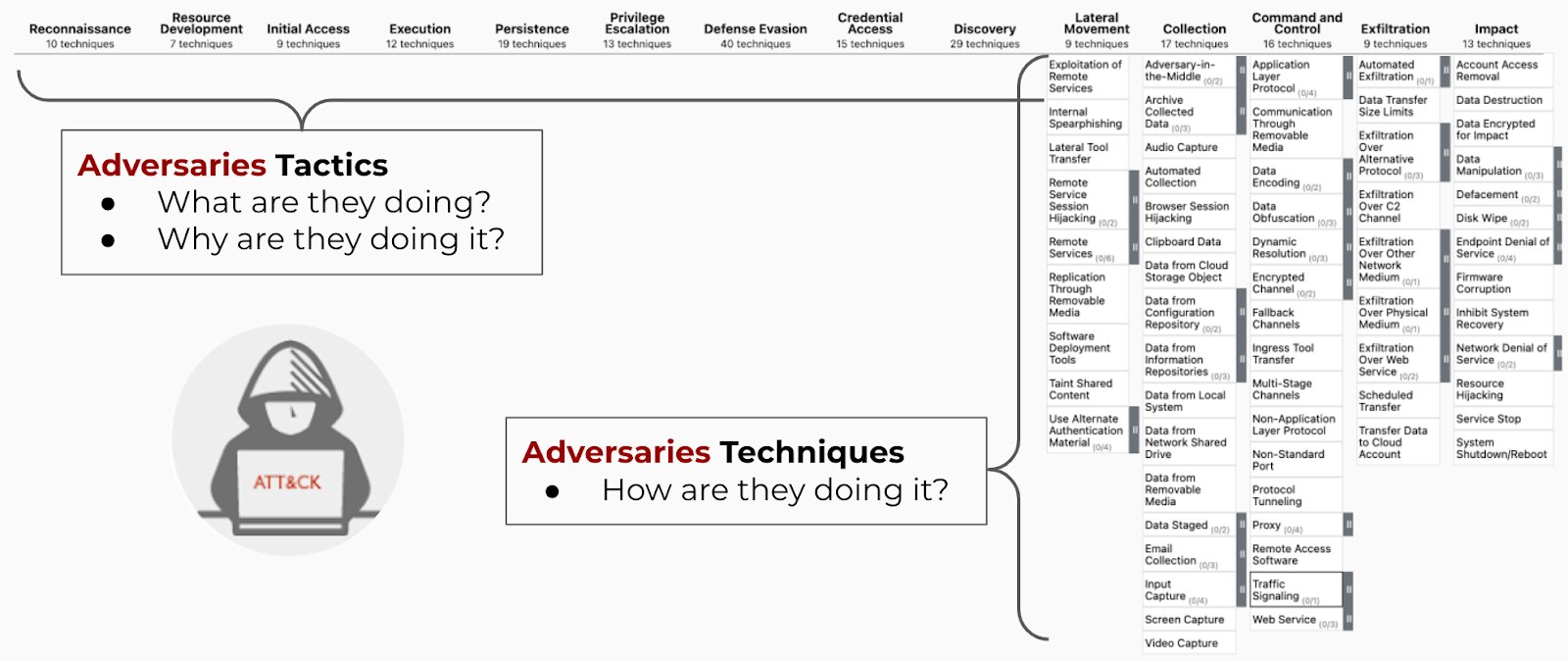
Figure 1: MITRE ATT&CK techniques describe “how” a threat actor performs specific actions.
MITRE ATT&CK Techniques Explained
Within the comprehensive MITRE ATT&CK framework, "techniques" are the fundamental building blocks that describe how a threat actor performs a specific action. Unlike broad tactics that define overall goals, such as gaining initial access or achieving persistence, techniques articulate the detailed behavioral step required to accomplish these objectives.
For example, to achieve "Execution," an adversary might use the "Command and Scripting Interpreter" technique. Each technique is meticulously cataloged with an identifier, description, and related metadata, offering a standardized lexicon for the global cybersecurity community to understand, track, and counter the nuanced actions of cyber adversaries based on real-world observations.
The Anatomy of a MITRE ATT&CK Technique
Every MITRE ATT&CK technique is a structured entry within the framework, meticulously documented to provide comprehensive insights into adversary behaviors. Understanding this anatomy is essential for effectively leveraging the ATT&CK knowledge base for defense and analysis. Each technique serves as a discrete unit of adversary action.
Identifying Techniques
Each technique is assigned a unique identifier, making it easy to reference and discuss. This standardization ensures clarity and consistency across security teams and threat intelligence reports.
The ID format typically begins with 'T' followed by a four-digit number, such as T1059 for "Command and Scripting Interpreter."
Core Components of a Technique Entry
Beyond a simple name and ID, each technique entry provides a wealth of information critical for security practitioners. These details help in understanding the context, impact, and detection possibilities of a given adversary action.
- Name and Description: A concise name and a detailed explanation of the adversary's method. The description covers the core concept and how it's typically employed.
- Associated Tactics: Each technique is mapped to one or more tactics. This link highlights the high-level objective that an adversary aims to achieve by employing that specific technique. For instance, "Process Injection" (T1055) can be used for Privilege Escalation, Defense Evasion, and Persistence.
- Sub-techniques: Many techniques have sub-techniques, providing even more granular detail on how a technique can be executed. These are identified with a decimal, like T1059.001 for "PowerShell" under "Command and Scripting Interpreter."
- Platforms Affected: Specifies the operating systems or environments where the technique is applicable (e.g., Windows, Linux, macOS, AWS, Azure, ICS).
- Mitigations: Recommended general defensive measures or security controls that can prevent or make it harder for an adversary to use a particular technique successfully. Examples include multifactor authentication (MFA), network segmentation, or user account management.
- Detections: Information on how to detect an adversary's use of a technique. This often includes data sources (e.g., process monitoring, network flow), common analytics, and potential indicators.
- Associated Groups/Software: Lists known threat groups or malware families that have been observed using this specific technique in real-world attacks. This provides concrete examples of the technique's operational use.
The Role of Sub-techniques
Sub-techniques offer a deeper level of specificity, breaking down complex techniques into more precise actions. This granularity allows for more targeted detection rules and more accurate mapping of adversary behavior.
For example, the technique "Account Manipulation" (T1098) encompasses sub-techniques such as "Additional Email Delegate Permissions" (T1098.002) and "Exchange Email Delegate Permissions" (T1098.003), each detailing a distinct method for manipulating accounts. This fine-grained detail facilitates an understanding of nuanced attack variations.

Figure 2: MITRE ATT&CK Uses
Understanding Common and Emerging ATT&CK Techniques
Staying abreast of the most common and emerging MITRE ATT&CK techniques is paramount for cybersecurity professionals. Adversaries continually refine their methods, and understanding these trends allows organizations to prioritize their defensive efforts effectively against the most prevalent threats.
Categories of Techniques by Tactic
While techniques span all tactics within the ATT&CK framework, some tactical categories consistently feature a higher volume of frequently observed techniques. These areas often represent critical stages in an attack lifecycle.
- Initial Access (TA0001): Techniques used to gain an initial foothold in a system or network. Common examples include "Phishing" (T1566) for credential harvesting or "Drive-by Compromise" (T1189) through malicious websites.
- Execution (TA0002): Techniques that result in adversary-controlled code running on a local or remote system. "Command and Scripting Interpreter" (T1059) and "Scheduled Task/Job" (T1053) are frequently observed in this context.
- Persistence (TA0003): Techniques used to maintain access to a system across restarts, changes in credentials, or other interruptions. "Create Account" (T1136) and "Registry Run Keys / Startup Folder" (T1547) are common.
- Defense Evasion (TA0005): Techniques adversaries use to avoid detection or hide their presence. "Impair Defenses" (T1562) by disabling security tools or "Obfuscated Files or Information" (T1027) are key here.
- Credential Access (TA0006): Techniques for stealing credentials like usernames and passwords. "OS Credential Dumping" (T1003), often via tools like Mimikatz, is a highly effective and prevalent technique.
Top Observed Techniques
Recent analyses from cybersecurity reports, including insights from Unit 42, consistently reveal specific techniques that dominate the threat landscape. These techniques are often effective, versatile, and frequently employed by various threat actors, making them high-priority targets for defense.
- Command and Scripting Interpreter (T1059): Continues to be a top technique across various stages of an attack. Its versatility allows adversaries to execute commands natively within compromised systems using legitimate tools, such as PowerShell or cmd.exe.
- Process Injection (T1055): Frequently used for stealth and persistence. Adversaries inject malicious code into legitimate running processes to evade detection and gain higher privileges without creating new process entries.
- Data from Local System (T1005): A foundational technique for collection. Adversaries gather data directly from the compromised local system, often a precursor to exfiltration.
- Application Layer Protocol (T1071): Critical for Command and Control (C2) communication. Attackers blend C2 traffic with legitimate application layer protocols like HTTP, DNS, or HTTPS to bypass network filtering and detection.
- Impair Defenses (T1562): Regularly observed as adversaries attempt to disable or modify security software and configurations to maintain their foothold and reduce the chances of detection.
Emerging Techniques and Trends
The threat landscape is dynamic, with adversaries constantly innovating or adapting existing techniques. Emerging trends often involve increasingly sophisticated methods of evasion and lateral movement.
- Living-off-the-Land Binaries (LOLBins): Increased reliance on legitimate system tools and binaries (LOLBins) to perform malicious actions. This makes detection more challenging as the activity appears "normal."
- Cloud-Specific Techniques: As organizations migrate to the cloud, adversaries are developing and refining techniques targeting cloud infrastructure, identity and access management (IAM), and cloud services. Examples include "Cloud API Spoofing" (T1609) or "Create Cloud Instance" (T1607).
- Supply Chain Compromise (T1195): Although a tactic, the techniques within this category, such as "Software Supply Chain Compromise" (T1195.002), are becoming more prevalent and sophisticated, leveraging trust in third-party software.
Detecting and Mitigating MITRE ATT&CK Techniques
Effectively detecting and mitigating MITRE ATT&CK techniques requires a structured approach that moves beyond simple signature matching to behavioral analysis. Organizations must develop comprehensive telemetry, analytics, and control validation processes to counter adversary actions.
Detection Strategies
Detecting specific ATT&CK techniques involves collecting the correct data and applying appropriate analytical methods to identify deviations from normal behavior or indicators of malicious activity.
- Comprehensive Telemetry Collection: To detect techniques, rich telemetry data is crucial. This includes:
- Process Monitoring: Tracking process creation, parent-child relationships, command-line arguments, and process injection attempts. This helps identify execution techniques like T1059 (Command and Scripting Interpreter) or T1055 (Process Injection).
- Network Flow and Packet Capture: Monitoring network connections, protocols, and data transfers to detect C2 techniques like T1071 (Application Layer Protocol) or data exfiltration.
- Endpoint Activity Logs: Collecting logs related to file access, registry modifications, scheduled tasks, and service installations for persistence and defense evasion techniques.
- Authentication Logs: Monitoring successful and failed login attempts, privilege escalation, and account manipulation for techniques like T1078 (Valid Accounts) or T1136 (Create Account).
- Behavioral Analytics and Rule Development: Developing detection rules and analytics that identify patterns associated with specific techniques, rather than just known malicious files. This includes:
- Heuristics: Rules based on suspicious sequences of actions (e.g., a Microsoft Word process spawning cmd.exe).
- Machine Learning (ML): Using ML models to identify anomalies that may indicate advanced techniques, especially those that blend with legitimate activity.
- Correlation Rules: Linking multiple low-fidelity alerts across different data sources to form a high-fidelity detection of a complete technique or attack chain.
Mitigation Approaches
Mitigating ATT&CK techniques involves applying specific security controls and configurations that either prevent the technique's execution or significantly hinder its effectiveness. Mapping controls to techniques ensures comprehensive coverage.
- Control Mapping: Organizations should map their existing security controls (e.g., endpoint protection, network segmentation, identity management) to the MITRE ATT&CK techniques they are designed to mitigate, identifying gaps and overlaps in their defensive capabilities.
- Principle of Least Privilege (PoLP): Implementing PoLP extensively helps mitigate many techniques related to privilege escalation and lateral movement. By limiting user and process permissions, attackers have fewer avenues to elevate access.
- Application Control and Whitelisting: Preventing unauthorized executables from running can effectively block many execution techniques (T1059) and prevent the loading of malicious tools.
- Network Segmentation: Segmenting networks isolates critical assets, limiting an adversary's ability to move laterally (e.g., T1021 - Remote Services) and exfiltrate data (T1041 - Exfiltration Over C2 Channel).
- Multi-Factor Authentication (MFA): Implementing MFA significantly mitigates techniques that rely on stolen credentials (e.g., T1078 - Valid Accounts) by adding another layer of authentication, even if a password is compromised.
- Security Awareness Training: Educating users on phishing, social engineering, and safe computing practices can directly mitigate initial access techniques like T1566 (Phishing) and T1534 (Internal Spear Phishing).
Prioritization of Techniques
Given the extensive number of techniques, prioritizing which ones to focus on for detection and mitigation is crucial. Not all techniques pose the same risk to every organization.
- Threat-Informed Defense: Prioritize techniques known to be used by threat actors most likely to target your organization, based on industry, geographic location, and intelligence reports. Unit 42's threat intelligence reports frequently highlight prevalent techniques used by specific threat groups.
- Impact Assessment: Evaluate the potential impact of a successful execution of each technique on your critical assets and operations. Techniques with high potential impact should be prioritized.
- Maturity Model: Assess your organization's current detection and mitigation capabilities against various techniques using frameworks like the ATT&CK Evaluations or ATT&CK Navigator. This provides a clear roadmap for improvement.
Leveraging ATT&CK Techniques for Enhanced Security Operations
MITRE ATT&CK techniques offer a powerful and actionable framework for enhancing various aspects of security operations. By focusing on adversary behaviors, security teams can move from reactive defense to proactive threat hunting, precise control validation, and effective adversary emulation.
Threat Hunting with Techniques
Threat hunting, a proactive search for undetected threats within a network, becomes significantly more effective when guided by ATT&CK techniques. Instead of merely reacting to alerts, hunters can proactively search for specific adversary behaviors.
- Hypothesis Generation: Threat hunters can develop hypotheses based on specific ATT&CK techniques. For example, a hypothesis might be: "Are adversaries using 'Process Hollowing' (T1055.012) for defense evasion in our environment?"
- Data Source Alignment: Techniques help identify the necessary data sources required for hunting. When hunting for "DLL Side-Loading" (T1574.002), a hunter should focus on process creation logs and DLL loads.
- Behavioral Pattern Recognition: ATT&CK provides the behavioral patterns to look for, enabling hunters to identify subtle anomalies that might indicate the presence of an advanced persistent threat (APT) that has bypassed initial defenses.
Adversary Emulation and Red Teaming
Adversary emulation involves simulating the TTPs of known threat actors to test an organization's security posture. ATT&CK techniques are the blueprint for these simulations, making them highly realistic and relevant.
- Realistic Attack Simulations: Red teams can precisely mimic the techniques used by specific threat groups, identified through ATT&CK's "Groups" section, to test defensive capabilities against real-world threats. For example, emulating a group known for "Valid Accounts" (T1078) and "Lateral Movement" (TA0008) via "Remote Desktop Protocol" (T1021.001) provides a targeted assessment.
- Measuring Defensive Efficacy: By executing specific ATT&CK techniques, organizations can objectively measure how well their security tools and processes detect and prevent those actions. This direct feedback is invaluable for refining security controls.
- Purple Teaming: The collaboration between red teams (offensive) and blue teams (defensive) using ATT&CK techniques is known as purple teaming. Red teams execute techniques, while blue teams actively try to detect and respond, fostering a continuous improvement cycle.
Security Control Validation
ATT&CK techniques provide a structured method for validating whether security controls are effectively mitigating specific adversary actions, ensuring that security investments yield tangible protection.
- Mapping Controls to Techniques: Security engineers can map their existing controls (e.g., EDR rules, firewall policies) directly to the ATT&CK techniques they are intended to block or detect. This visual mapping helps identify areas of strong coverage and areas where gaps exist.
- Automated Validation: Tools exist that can automatically execute ATT&CK techniques in a controlled environment and report on whether security controls generated alerts or prevented the activity. This provides continuous validation of security effectiveness.
- Performance Benchmarking: Organizations can benchmark their detection and prevention capabilities against ATT&CK techniques, comparing their performance over time or against industry peers to drive continuous improvement.
The Future Evolution of ATT&CK Techniques
The MITRE ATT&CK framework is a dynamic and continuously evolving resource, adapting to the ever-changing cybersecurity landscape. Its future evolution will likely involve deeper integration with emerging technologies, expanded coverage into new domains, and continued community-driven enrichment of its technique knowledge base.
Adapting to New Adversary Behaviors
As adversaries innovate, new techniques and variations of existing ones emerge. The ATT&CK framework's update cycle is designed to capture these new behaviors, ensuring its continued relevance.
This includes detailing how adversaries leverage new technologies or exploit new vulnerabilities. The framework consistently introduces new techniques and sub-techniques to reflect the latest observed attack patterns, maintaining its comprehensiveness and accuracy.
Expansion into Emerging Domains
While ATT&CK currently covers enterprise, mobile, and industrial control systems, the scope of adversary activity is constantly broadening. Future expansions of the technique knowledge base may include:
- Artificial Intelligence (AI) and Machine Learning (ML) Systems: With the rise of AI in critical applications, adversaries are developing techniques to compromise or manipulate AI/ML models. MITRE ATLAS (Adversarial Threat Landscape for Artificial-intelligence Systems) is an early indicator of this expansion, categorizing techniques for attacking AI systems themselves.
- Supply Chain Security: While ATT&CK has "Supply Chain Compromise" (T1195) as a technique, a deeper dive into specific techniques targeting various stages of the supply chain, from software development to deployment, may become more granular.
- Specialized IoT/OT Environments: As the Internet of Things (IoT) proliferates in critical infrastructure and enterprises, more specific techniques targeting these unique environments will likely be documented and detailed within the framework.
Deeper Integration with Automation and Orchestration
The detailed nature of ATT&CK techniques makes them ideal for integration with security automation and orchestration (SOAR) platforms. This allows for automated detection, response, and even proactive defense.
Future developments will likely enhance the machine-readability and actionability of technique data, enabling more sophisticated automated security operations. This includes using AI-powered analytics to identify complex technique chains and trigger automated mitigations.
Community-Driven Growth and Collaboration
The strength and comprehensiveness of MITRE ATT&CK are significantly bolstered by its active and diverse community of security practitioners, researchers, and vendors. This collaborative approach ensures that the framework remains relevant and comprehensive.
Continuous community contributions, feedback, and shared intelligence will drive the ongoing refinement and expansion of the technique knowledge base, ensuring it remains an authoritative source for understanding and countering adversary behaviors.
